Question
Clearly, in the view of the SEC, the likelihood of compromise of an integrated system of hardware and software is considerably less than the likelihood
Clearly, in the view of the SEC, the likelihood of compromise of an integrated system of hardware and software is considerably less than the likelihood of compromise of a system of authentication, passwords, and procedures. Do you agree with this view? Why or why not? (from passage below:)
In 1937, the Securities and Exchange Commission (SEC) set out rules that stipulated records retention requirements for securities brokers and dealers. The SECs concern was (and is) that records of financial transactions not be altered after the fact, that they be retained for a stipulated period of time, and that indexes be created so that the records can be readily searched.
In 1937, the rules assumed that such records were recorded on paper media. With the rise of information systems storage, in 1997 the SEC updated the rules by stating that such records can be kept electronically, provided that the storage devices are write once, read many times (WORM) devices. This rule was readily accepted by the financial services industry because the first CDs and DVDs were WORM devices.
However, as technology developed, broker-dealers and other financial institutions wanted to store records using regular disk storage and petitioned the SEC for guidance on how they might do that. In May 2003, the SEC interpreted the rule to enable the storage of such records on read-write media, provided that the storage mechanism included software that would prohibit data alteration:
A broker-dealer would not violate the requirement in paragraph (f)(2)(ii)(A) of the rule if it used an electronic storage system that prevents the overwriting, erasing or otherwise altering of a record during its required retention period through the use of integrated hardware and software control codes. Rule 17a-4 requires broker-dealers to retain records for specified lengths of time. Therefore, it follows that the non-erasable and non-rewriteable aspect of their storage need not continue beyond that period.
The Commissions interpretation does not include storage systems that only mitigate the risk a record will be overwritten or erased. Such systemswhich may use software applications to protect electronic records, such as authentication and approval policies, passwords or other extrinsic security controlsdo not maintain the records in a manner that is non-rewriteable and non-erasable. The external measures used by these other systems do not prevent a record from being changed or deleted. For example, they might limit access to records through the use of passwords. Additionally, they might create a finger print of the record based on its content. If the record is changed, the fingerprint will indicate that it was altered (but the original record would not be preserved). The ability to overwrite or erase records stored on these systems makes them non-compliant with Rule 17a-4(f) (U.S. Securities and Exchange Commission, SEC Interpretation: Electronic Storage of Broker-Dealer Records, last modified May 5, 2003, www.sec.gov/rules/interp/34-47806.htm (Links to an external site.)Links to an external site.)
Notice the SEC specifically excludes extrinsic controls such as authentication, passwords, and manual procedures because it believes it would be possible for such systems to be readily misused to overwrite records. The SEC is striking a fine line in this ruling; if, for example, someone were to tamper with the storage systems software, it would be possible to overwrite data. Apparently, the SEC assumes such tampering would be illegal and so rare as to not be a concern.
Given this ruling, organizations began to develop systems in compliance. The NASDAQ OMX Group, a multinational corporation that owns and operates the NASDAQ stock market as well as eight European exchanges, began to develop FinQloud, a cloud-based storage system that was developed to be compliant with the SECs (and other regulating organizations) rulings. NASDAQ OMX operates in 70 different markets, in 50 countries worldwide, and claims that it processes one out of 10 stock transactions worldwide (NASDAQ OMX, NASDAQ OMX FinQloud, accessed May 2013, www.nasdaqomx.com/technology/yourbusiness/finqloud/.)
Figure6-25
Components of the FinQloud System
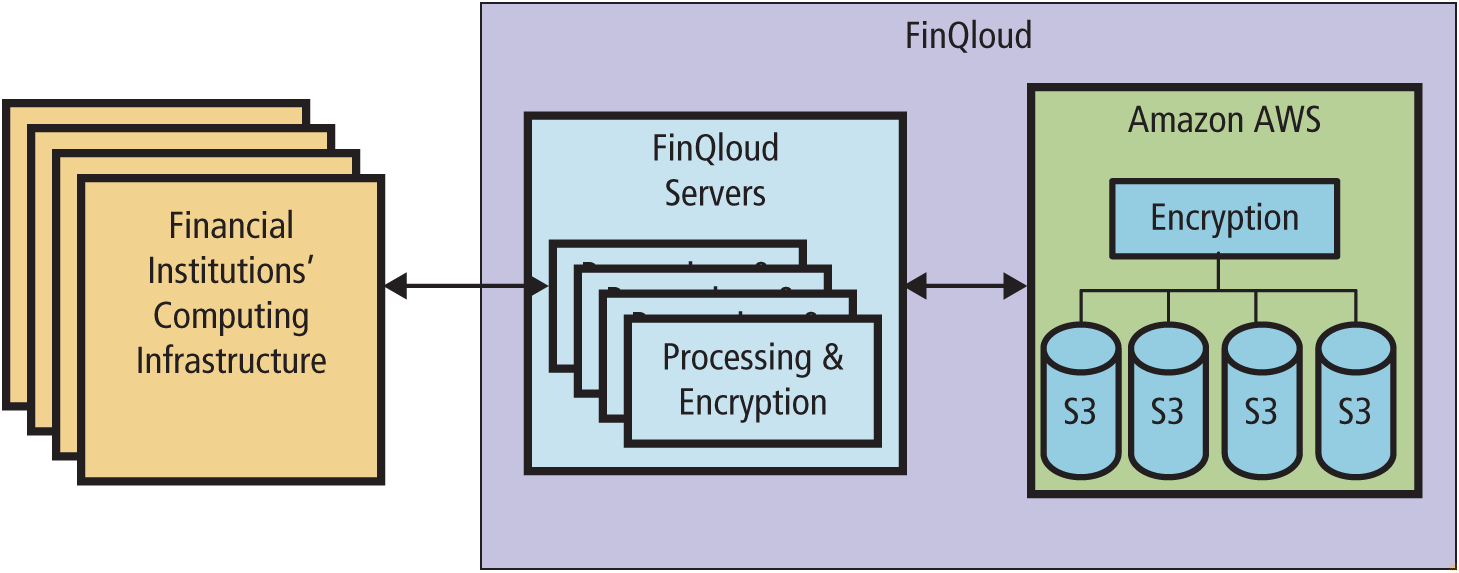
Figure6-25 (Links to an external site.)Links to an external site. shows the fundamental structure of the FinQloud system. On the back end, it uses Amazons S3 product to provide scalable, elastic storage. When financial institutions submit records to FinQloud for storage, FinQloud processes the data in such a way that it cannot be updated, encrypts the data, and transmits the processed, encrypted data to AWS, where it is encrypted yet again and stored on S3 devices. Data is indexed on S3 and can be readily read by authorized users. NASDAQ OMX then claimed that FinQlouds processing and encryption is done is such a way that it meets the SEC requirement.
Of course, NASDAQ OMX knew this statement would be perceived as self-serving, so it hired two independent companies to verify that claim: Jordan & Jordan, a securities industry consulting company, and Cohasset Associates, a document-processing consulting company. According to TheWall Street Journal, both organizations concluded that when properly configured, FinQloud meets the requirements of the SECs rule (Rule 17a-3) as well as a similar rule set out by the Commodities Futures Trading Commission (Greg MacSweeney, Nasdaq OMX FinQloud R3 Meets SEC/CFTC Regulatory Requirements, Say Consultants, April 15, 2013, www.wallstreetandtech .com/data-managementasdaq-omx-finqloud-r3-meets-seccftc-reg/240152909.)
Consequently, NASDAQ OMX customers can use FinQloud, and as long as they can demonstrate that they have properly configured it, their auditors will find this system to be in compliance with the SEC rulings.
FinQloud Amazon AWS FinQloud Servers Encryption Financial Institutions Computing Infrastructure Processing & ?? Encryption S3 S3 S3 S3Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


