Answered step by step
Verified Expert Solution
Question
1 Approved Answer
COMPLETE THE FOLLOWING PROGRAM IN PYTHON: logentry.py: class LogEntry: def __init__(self, time, ip, success): self.time = time self.ip = ip self.success = success @staticmethod def
COMPLETE THE FOLLOWING PROGRAM IN PYTHON:
logentry.py:
class LogEntry: def __init__(self, time, ip, success): self.time = time self.ip = ip self.success = success
@staticmethod def fromstring(string): time, ip, success = string[1:-1].split('][') if success not in ['SUCCESS', 'FAIL']: raise ValueError("Only 'SUCCESS' and 'FAIL' are valid values.") return LogEntry(float(time), ip, success)
def __str__(self): return "".join(['[', str(self.time), ']','[', str(self.ip), ']','[', str(self.success), ']'])
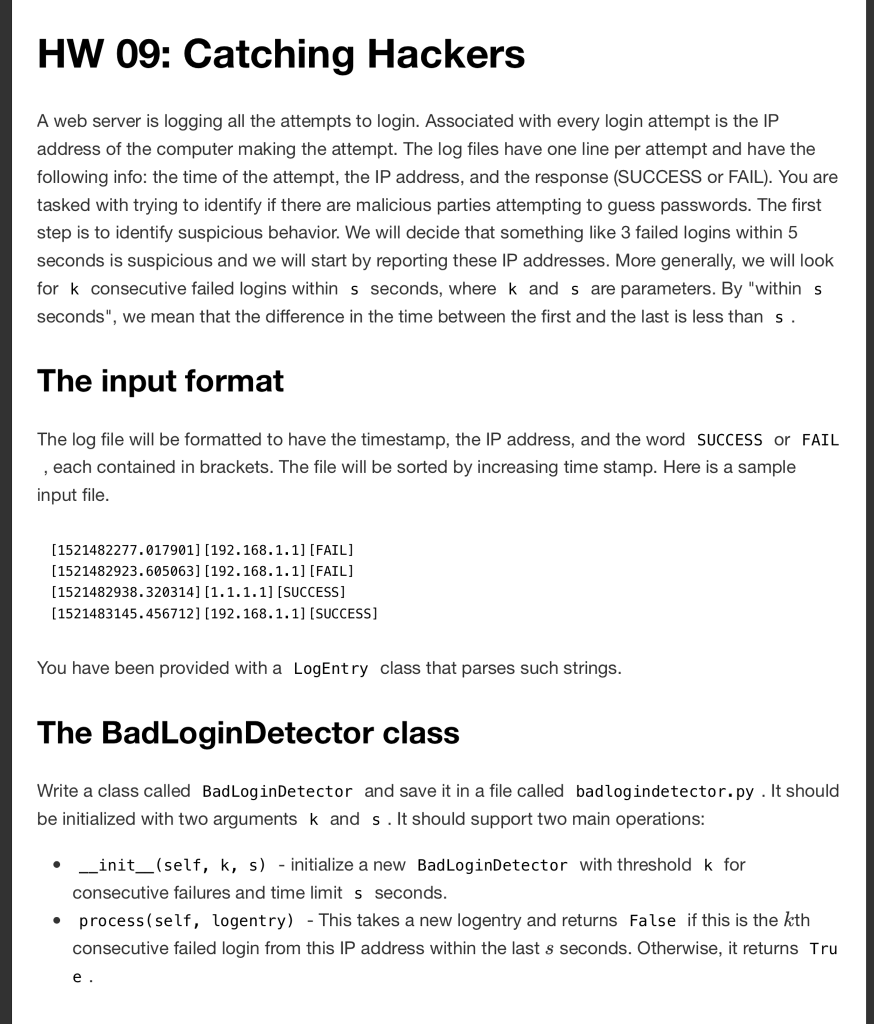
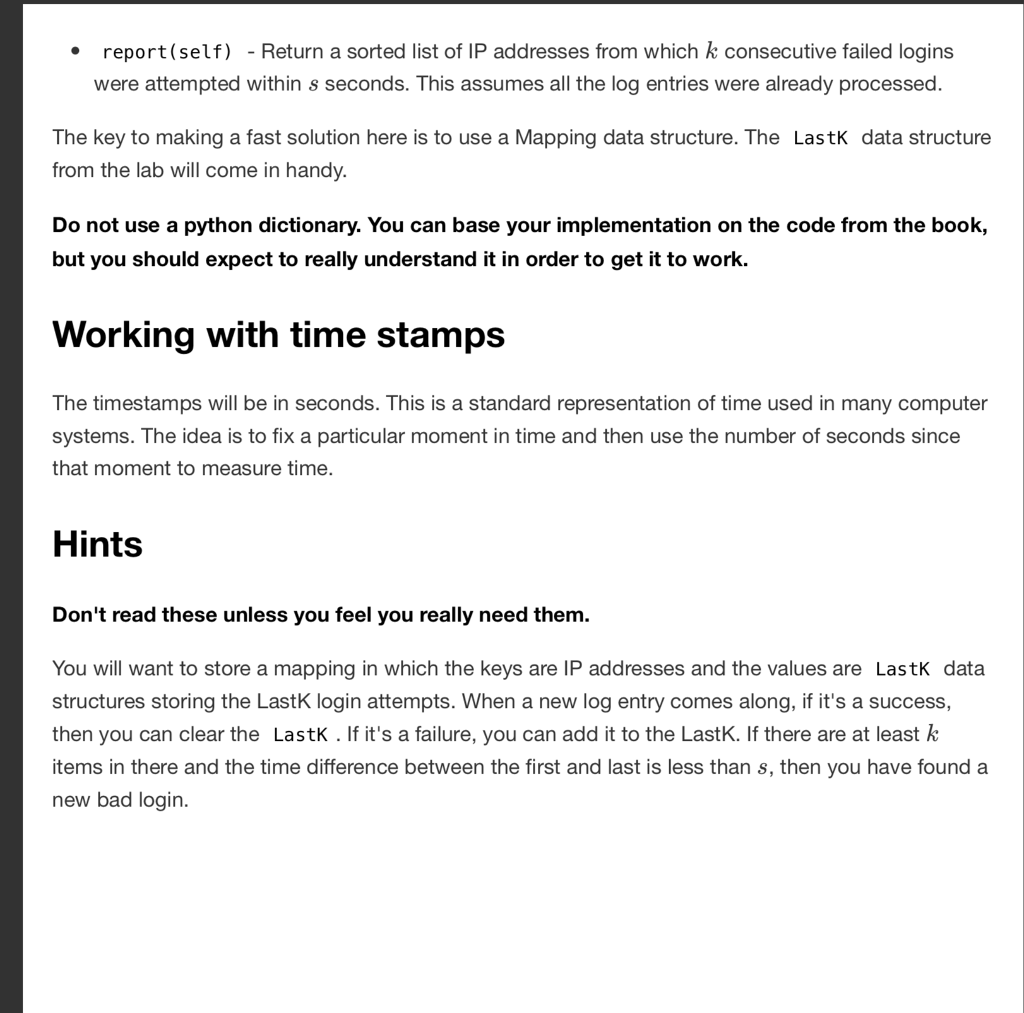
HW 09: Catching Hackers A web server is logging all the attempts to login. Associated with every login attempt is the IP address of the computer making the attempt. The log files have one line per attempt and have the following info: the time of the attempt, the IP address, and the response (SUCCESS or FAIL). You are tasked with trying to identify if there are malicious parties attempting to guess passwords. The first step is to identify suspicious behavior. We will decide that something like 3 failed logins within 5 seconds is suspicious and we will start by reporting these IP addresses. More generally, we will look for k consecutive failed logins within s seconds, where k and s are parameters. By "within s seconds", we mean that the difference in the time between the first and the last is less than s The input format The log file will be formatted to have the timestamp, the IP address, and the word SUCCESS or FAIL each contained in brackets. The file will be sorted by increasing time stamp. Here is a sample input file. [152 1482277.017901] [192.168.1.1] [FAIL] [1521482923.605063] [192. 168. 1.1] [FAIL] 1521482938.320314] 11.1.1.11 [SUCCESS] [1521483145.456712] 1192.168.1.1] [SUCCESS] You have been provided with a LogEntry class that parses such strings. The BadLoginDetector class Write a class called BadLoginDetector and save it in a file called badlogindetector.py.It should be initialized with two arguments k and s.It should support two main operations -init-(self, k, s) -initialize a new BadLoginDetector with threshold k for consecutive failures and time limit s seconds. process (self, logentry) This takes a new logentry and returns False if this is the kth consecutive failed login from this IP address within the last s seconds. Otherwise, it returns Tru . HW 09: Catching Hackers A web server is logging all the attempts to login. Associated with every login attempt is the IP address of the computer making the attempt. The log files have one line per attempt and have the following info: the time of the attempt, the IP address, and the response (SUCCESS or FAIL). You are tasked with trying to identify if there are malicious parties attempting to guess passwords. The first step is to identify suspicious behavior. We will decide that something like 3 failed logins within 5 seconds is suspicious and we will start by reporting these IP addresses. More generally, we will look for k consecutive failed logins within s seconds, where k and s are parameters. By "within s seconds", we mean that the difference in the time between the first and the last is less than s The input format The log file will be formatted to have the timestamp, the IP address, and the word SUCCESS or FAIL each contained in brackets. The file will be sorted by increasing time stamp. Here is a sample input file. [152 1482277.017901] [192.168.1.1] [FAIL] [1521482923.605063] [192. 168. 1.1] [FAIL] 1521482938.320314] 11.1.1.11 [SUCCESS] [1521483145.456712] 1192.168.1.1] [SUCCESS] You have been provided with a LogEntry class that parses such strings. The BadLoginDetector class Write a class called BadLoginDetector and save it in a file called badlogindetector.py.It should be initialized with two arguments k and s.It should support two main operations -init-(self, k, s) -initialize a new BadLoginDetector with threshold k for consecutive failures and time limit s seconds. process (self, logentry) This takes a new logentry and returns False if this is the kth consecutive failed login from this IP address within the last s seconds. Otherwise, it returns TruStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


