Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Computer Fraud and Abuse Techniques. Match the Internet-related computer fraud and abuse technique in the left column with the scenario in the right column. The
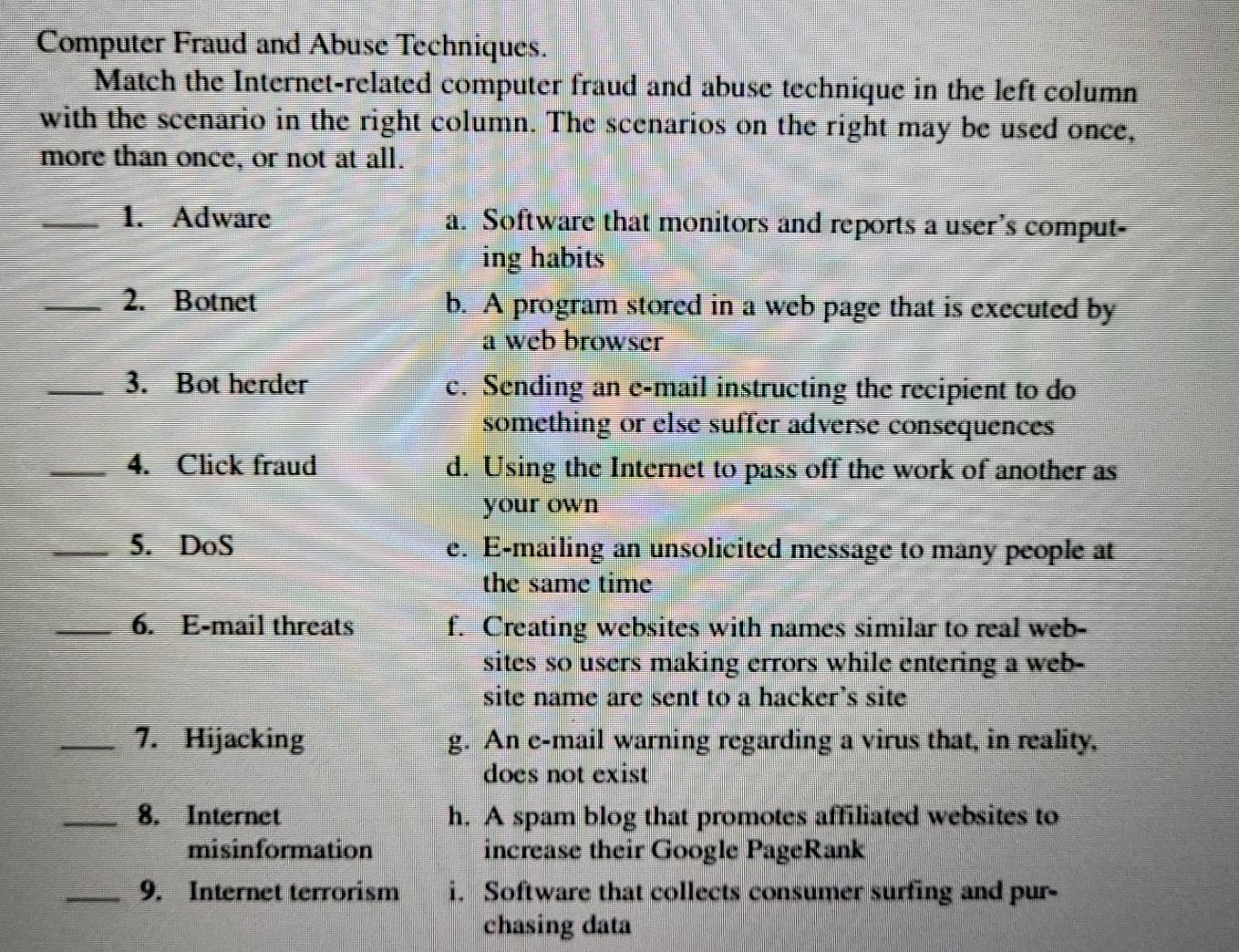

Computer Fraud and Abuse Techniques. Match the Internet-related computer fraud and abuse technique in the left column with the scenario in the right column. The scenarios on the right may be used once, more than once, or not at all. 1. Adware 2. Botnet 3. Bot herder 4. Click fraud 5. Dos a. Software that monitors and reports a user's comput- ing habits b. A program stored in a web page that is executed by a web browser c. Sending an e-mail instructing the recipient to do something or else suffer adverse consequences d. Using the Internet to pass off the work of another as your own e. E-mailing an unsolicited message to many people at the same time f. Creating websites with names similar to real web- sites so users making errors while entering a web- site name are sent to a hacker's site g. An e-mail warning regarding a virus that, in reality, does not exist h. A spam blog that promotes affiliated websites to increase their Google PageRank i. Software that collects consumer surfing and pur- chasing data 6. E-mail threats 7. Hijacking 8. Internet misinformation 9. Internet terrorism 10. Key logger 11. Pharming 12. Phishing 13. Spamming 14. Splog j. E-mails that look like they came from a legitimate source but are actually from a hacker who is trying to get the user to divulge personal information k. Making an e-mail look like it came from someone else 1. Gaining control of a computer to carry out unau- thorized illicit activities m. Using the Internet to disrupt communications and e-commerce n. Diverting traffic from a legitimate website to a hacker's website to gain access to personal and confidential information 0. A network of hijacked computers p. Using a legion of compromised computers to launch a coordinated attack on an Internet site q. Use of spyware to record a user's keystrokes r. Hackers that control hijacked computers s. Circulating lies or misleading information using the world's largest network t. Overloading an Internet service provider's e-mail server by sending hundreds of e-mail messages per second from randomly generated false addresses u. Inflating advertising revenue by clicking online ads numerous times 15. Spyware 16. Spoofing 17. Typosquatting
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


