Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Computer Security Question about the Caesar Cipher: I also don't know this part of the problem Hello I am not sure how to figure this
Computer Security Question about the Caesar Cipher:

I also don't know this part of the problem
Hello I am not sure how to figure this out
Hello so for question 3, I think its +23 "the password is qqzzqqz"
choose the correct multiple choice
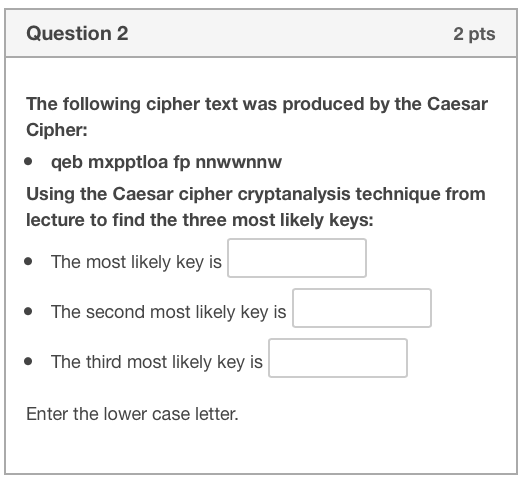
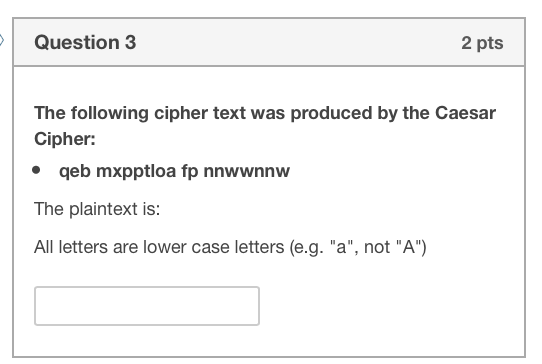
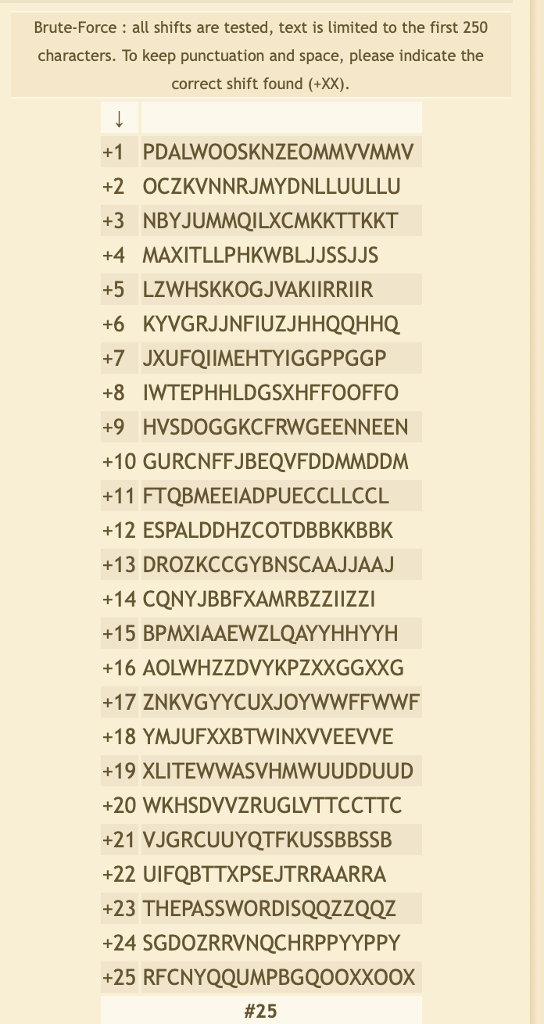
Question1 2 pts The following cipher text was produced by the Caesar Cipher: The Caesar cipher cryptanalysis technique from lecture calculates the most likely keys. When the technique is applied in this case, which of the following best explains the results? o The actual key is not one of three most likely keys because word 4 does not match typical character frequencies The actual key is one the three most likely keys. o The actual key is not one of three most likely keys because word 3 is is too short for the method to work. The actual key is not one of three most likely keys because word 2 is too complex The actual key is not one of three most likely keys because word 1 is not a common word. Question 2 2 pts The following cipher text was produced by the Caesar Cipher: Using the Caesar cipher cryptanalysis technique from lecture to find the three most likely keys: The most likely key is The second most likely key is The third most likely key is * Enter the lower case letter. Question 3 2 pts The following cipher text was produced by the Caesar Cipher: The plaintext is: All letters are lower case letters (e.g. "a", not "A") Brute-Force: all shifts are tested, text is limited to the first 250 characters. To keep punctuation and space, please indicate the correct shift found (+XX) +1 PDALWOOSKNZEOMMVVMMV +2 OCZKVNNRJMYDNLLUULLU +3 NBYJUMMQILXCMKKTTKKT +4 MAXITLLPHKWBLJJSSJJS +5 LZWHSKKOGJVAKIIRRIIR +6 KYVGRJJNFIUZJHHQQHHQ +7 JXUFQIIMEHTYIGGPPGGP +8 IWTEPHHLDGSXHFFOOFFO +9 HVSDOGGKCFRWGEENNEEN +10 GURCNFFJBEQVFDDMMDDM +11 FTQBMEEIADPUECCLLCCL +12 ESPALDDHZCOTDBBKKBBK +13 DROZKCCGYBNSCAAJJAAJ +14 CQNYJBBFXAMRBZZIIZZI +15 BPMXIAAEWZLQAYYHHYYH +16 AOLWHZZDVYKPZXXGGXXG +17 ZNKVGYYCUXJOYWWFFWWF +18 YMJUFXXBTWINXVVEEVVE +19 XLITEWWASVHMWUUDDUUD +20 WKHSDVVZRUGLVTTCCTTC +21 VJGRCUUYQTFKUSSBBSSB +22 UIFQBTTXPSEJTRRAARRA +23 THEPASSWORDiSQQZZQQZ +24 SGDOZRRVNQCHRPPYYPPY +25 RFCNYQQUMPBGQOOXxoox #25Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started