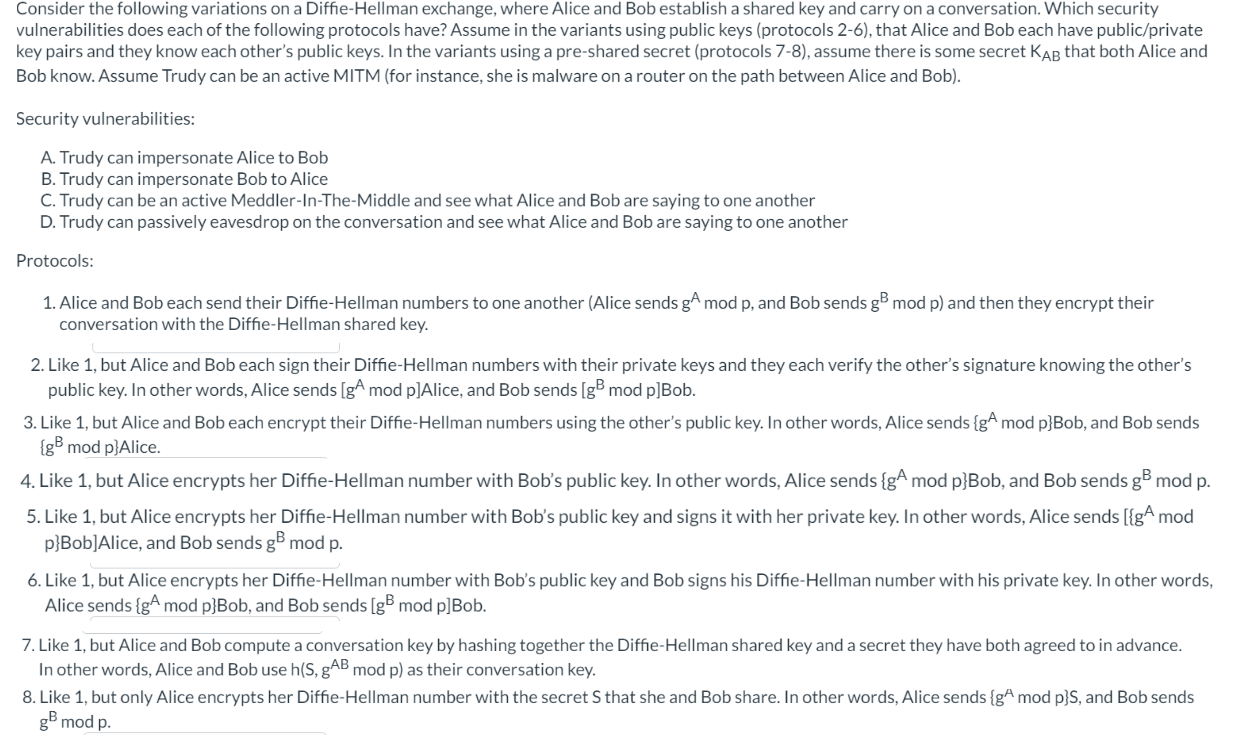
Question: Consider the following variations on a Diffie - Hellman exchange, where Alice and Bob establish a shared key and carry on a conversation. Which security
Consider the following variations on a DiffieHellman exchange, where Alice and Bob establish a shared key and carry on a conversation. Which security
vulnerabilities does each of the following protocols have? Assume in the variants using public keys protocols that Alice and Bob each have publicprivate
key pairs and they know each other's public keys. In the variants using a preshared secret protocols assume there is some secret that both Alice and
Bob know. Assume Trudy can be an active MITM for instance, she is malware on a router on the path between Alice and Bob
Security vulnerabilities:
A Trudy can impersonate Alice to Bob
B Trudy can impersonate Bob to Alice
C Trudy can be an active MeddlerInTheMiddle and see what Alice and Bob are saying to one another
D Trudy can passively eavesdrop on the conversation and see what Alice and Bob are saying to one another
Protocols:
Alice and Bob each send their DiffieHellman numbers to one another Alice sends mod and Bob sends mod and then they encrypt their
conversation with the DiffieHellman shared key.
Like but Alce and Bob each sgn their DiffieHellman numbers with their private keys and they each verify the other's signature knowing the other's
public key. In other words, Alice sends gA mod pAlice and Bob sends gB mod pBob
Like but Alice and Bob each encrypt their DiffieHellman numbers using the other's public key. In other words, Alice sends mod pBob and Bob sends
g mod pAlice
Like but Alice encrypts her DiffieHellman number with Bob's public key. In other words, Alice sends mod p
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


