Answered step by step
Verified Expert Solution
Question
1 Approved Answer
course name routing and switching Nererences Mailings Review View Help Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected
course name routing and switching
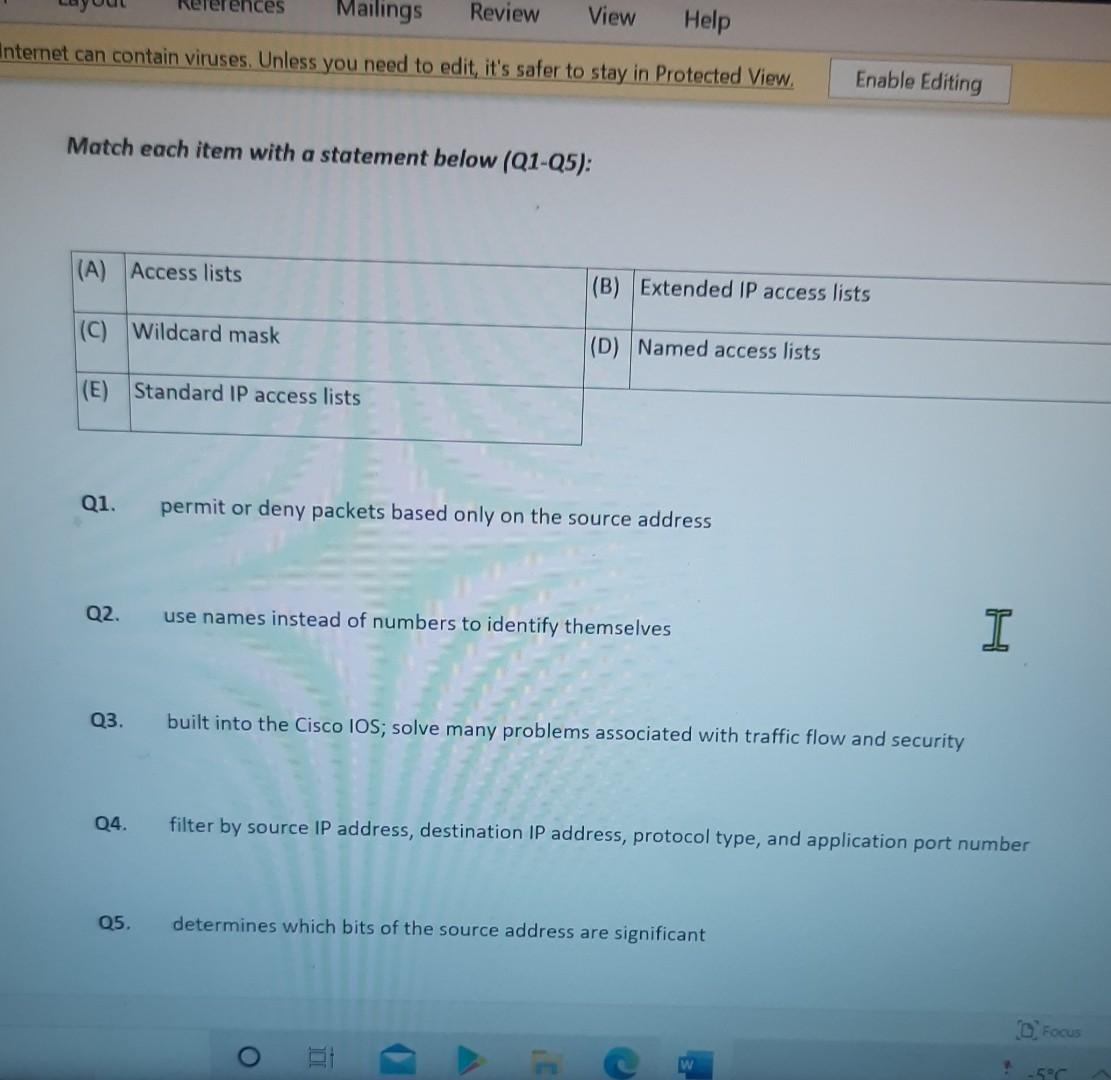
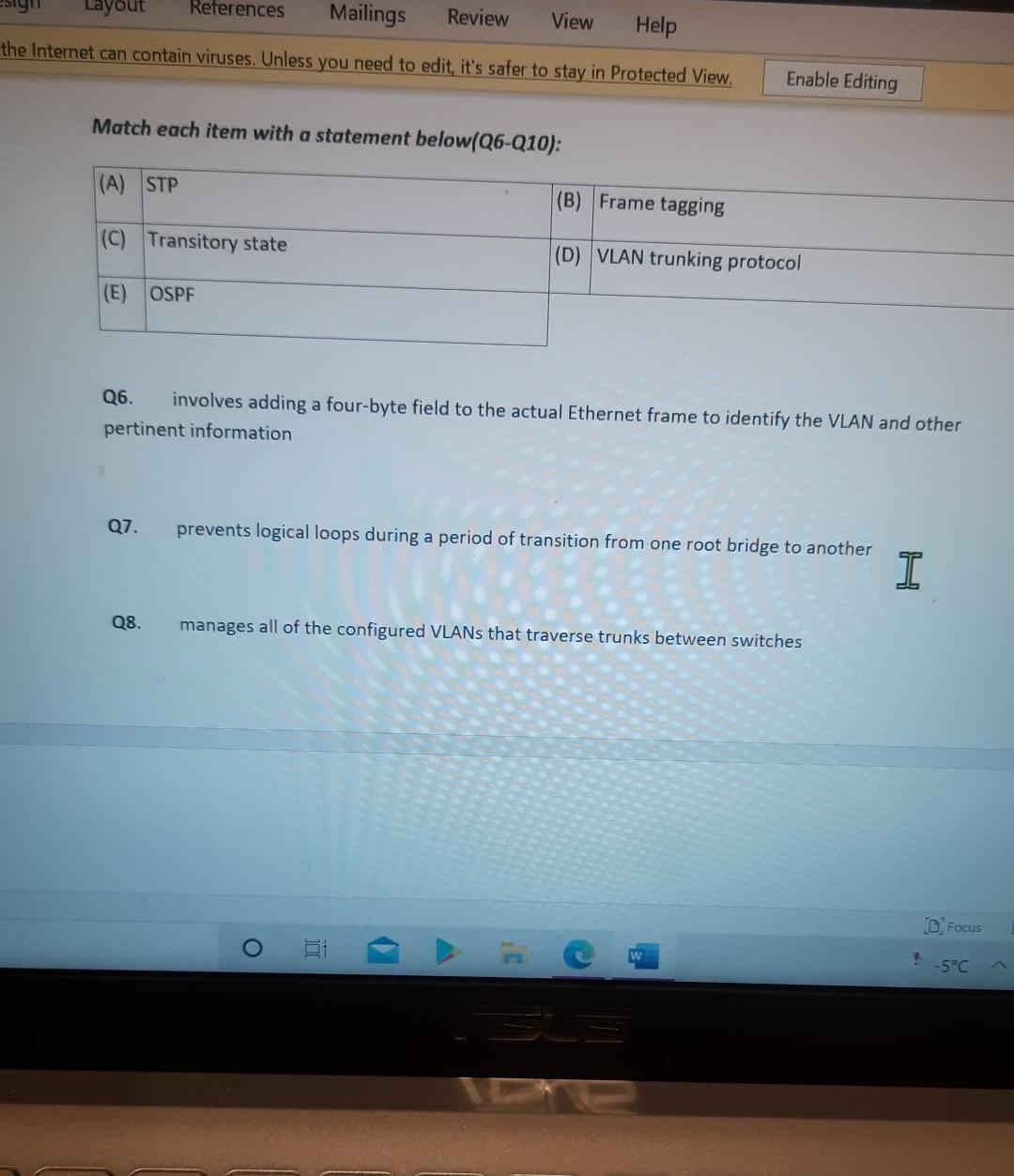
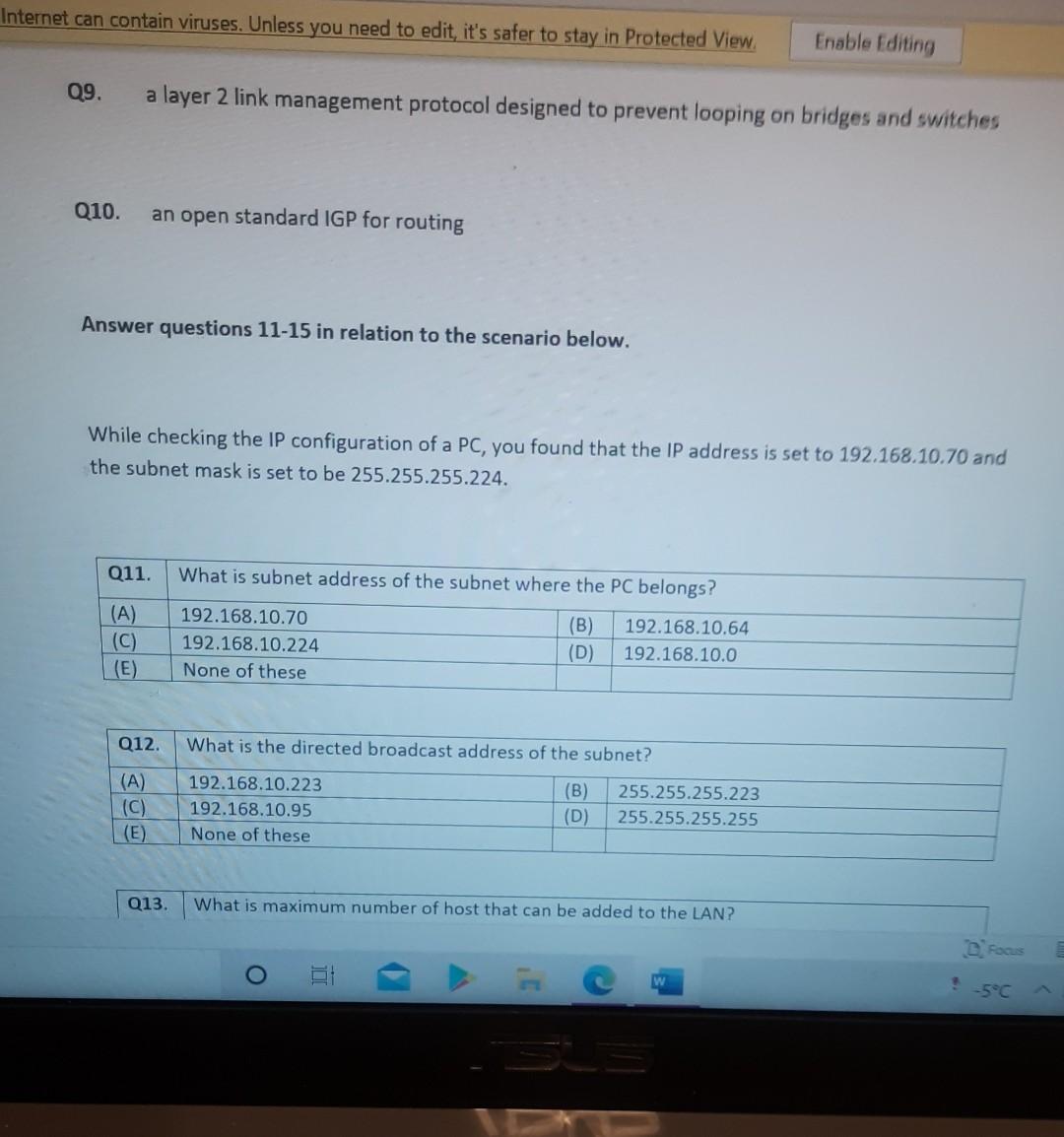
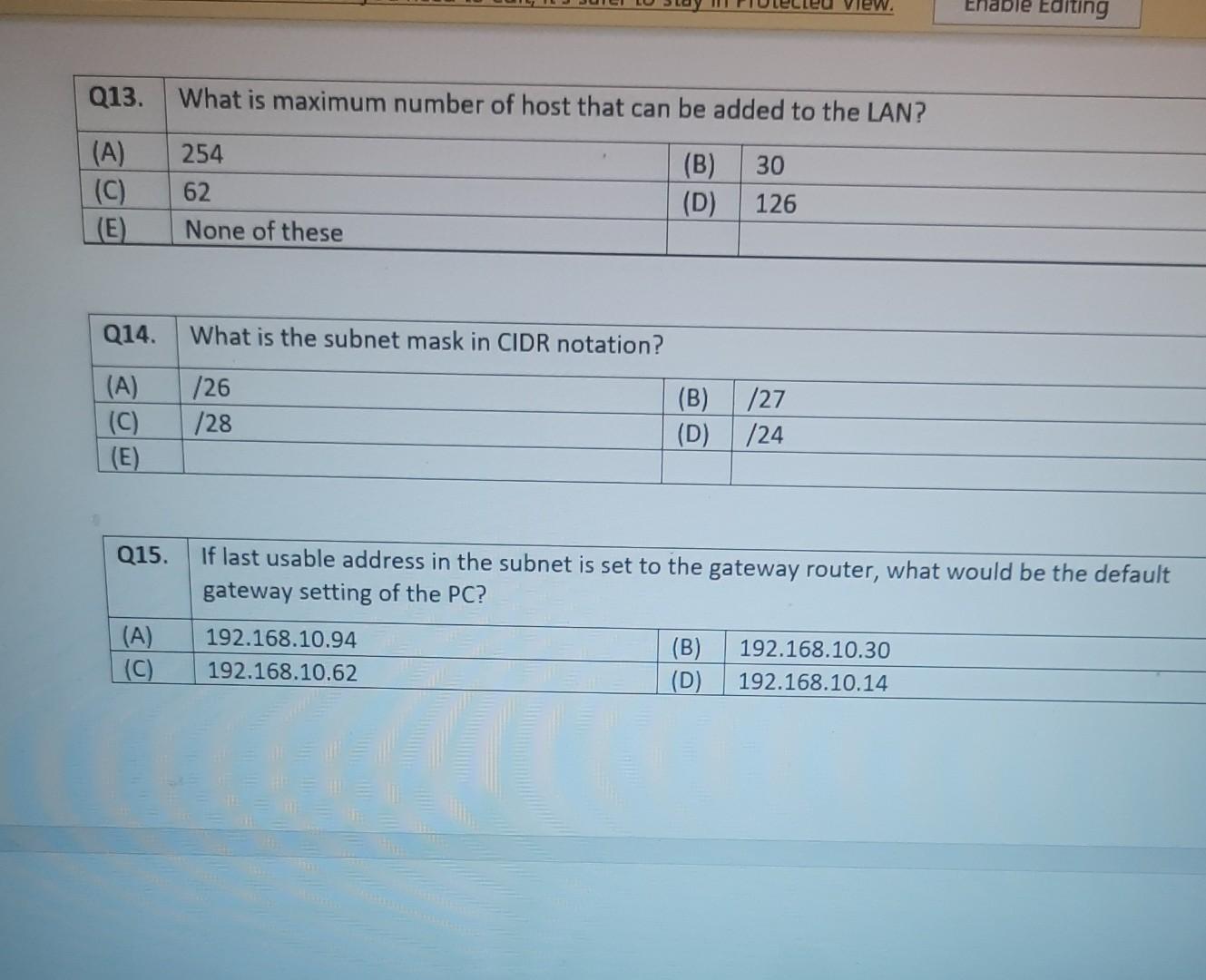
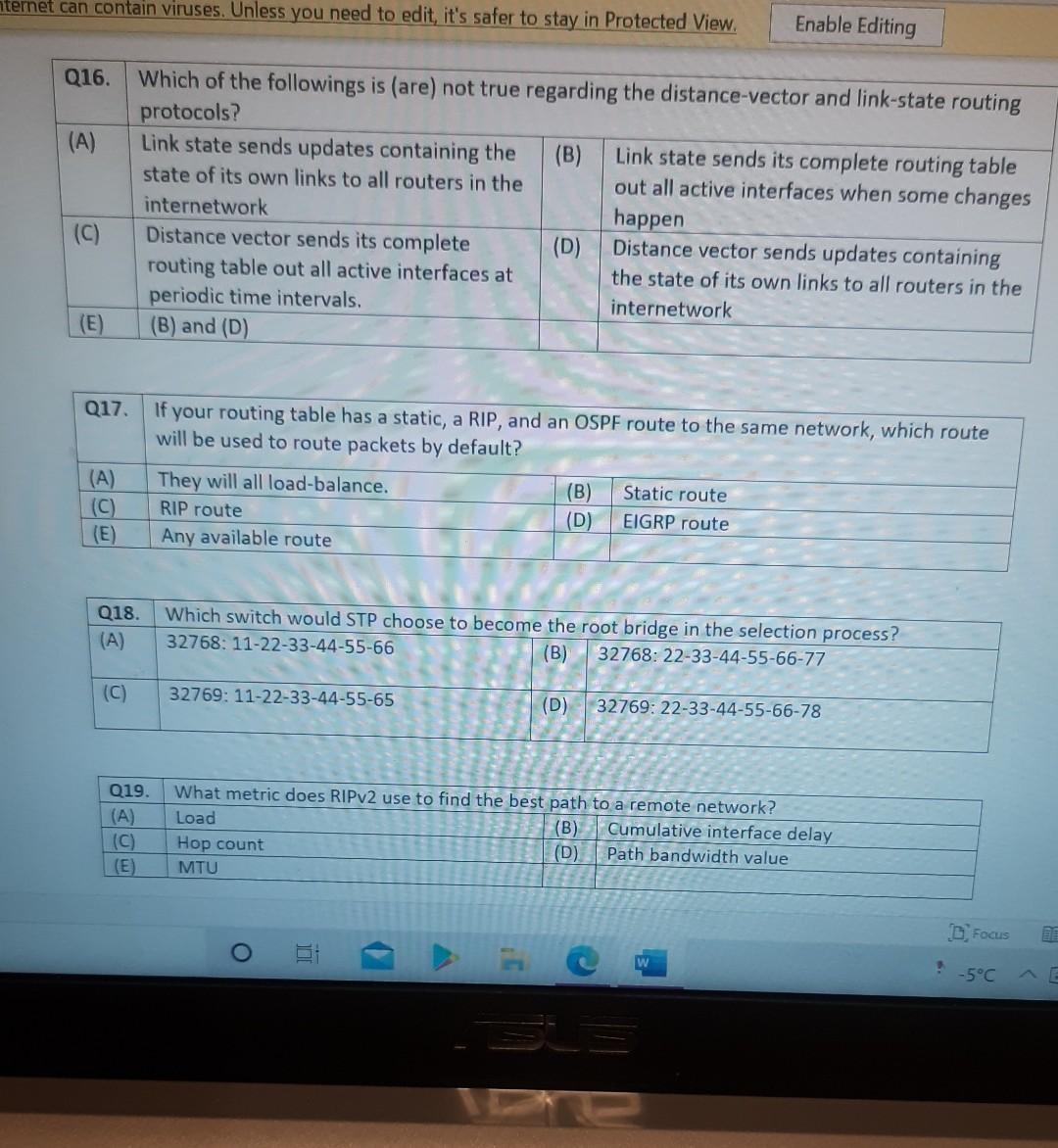
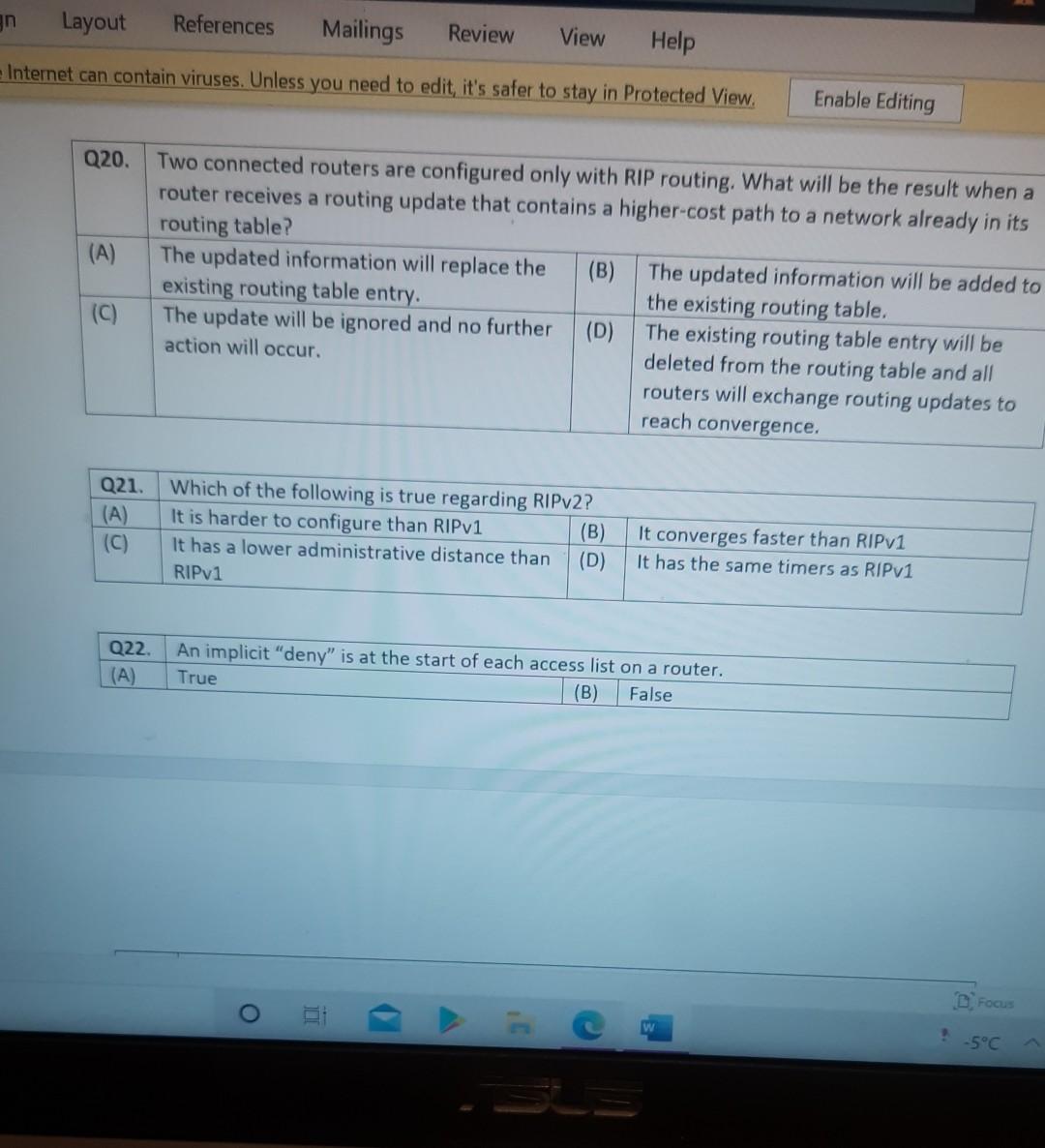
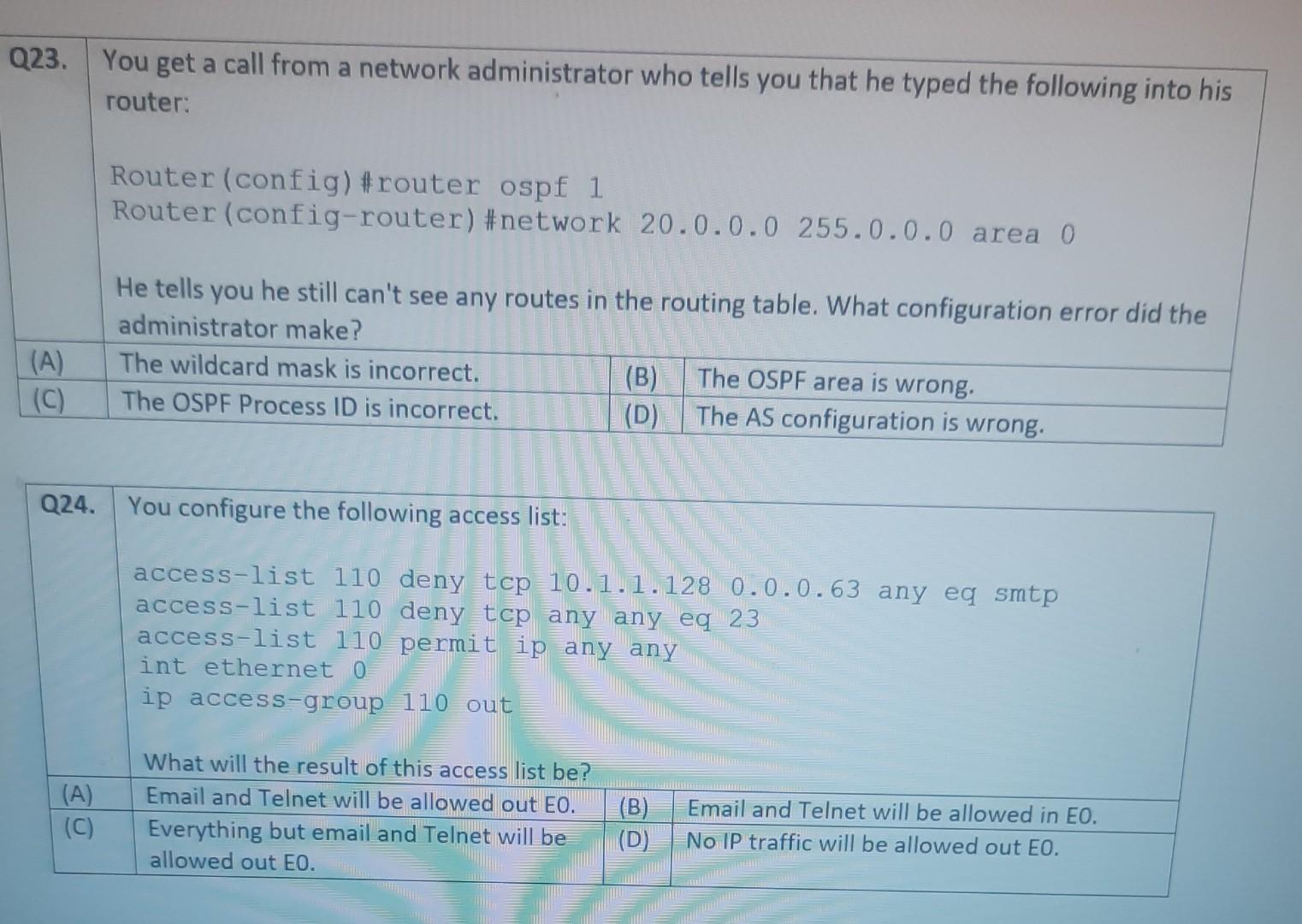
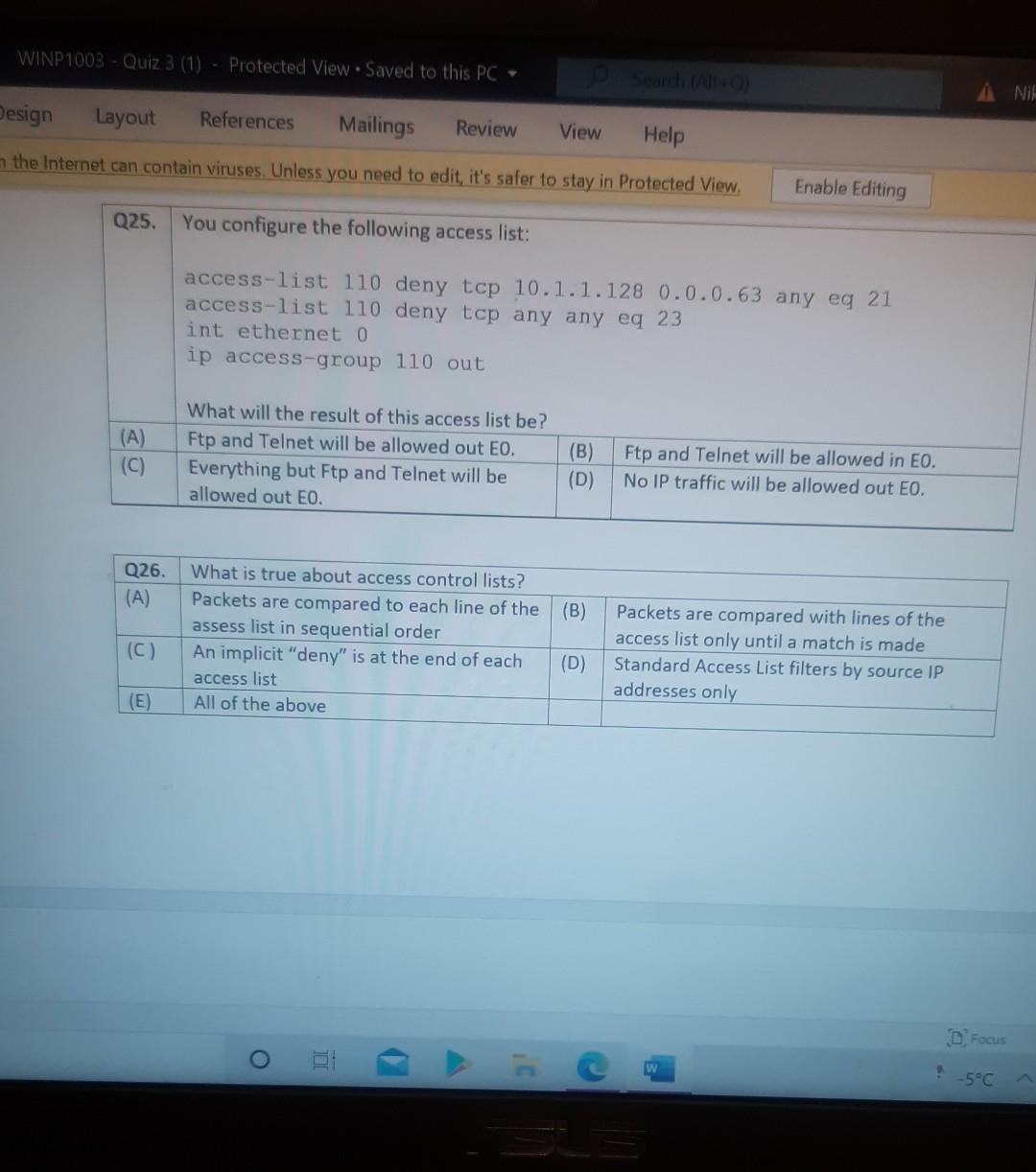
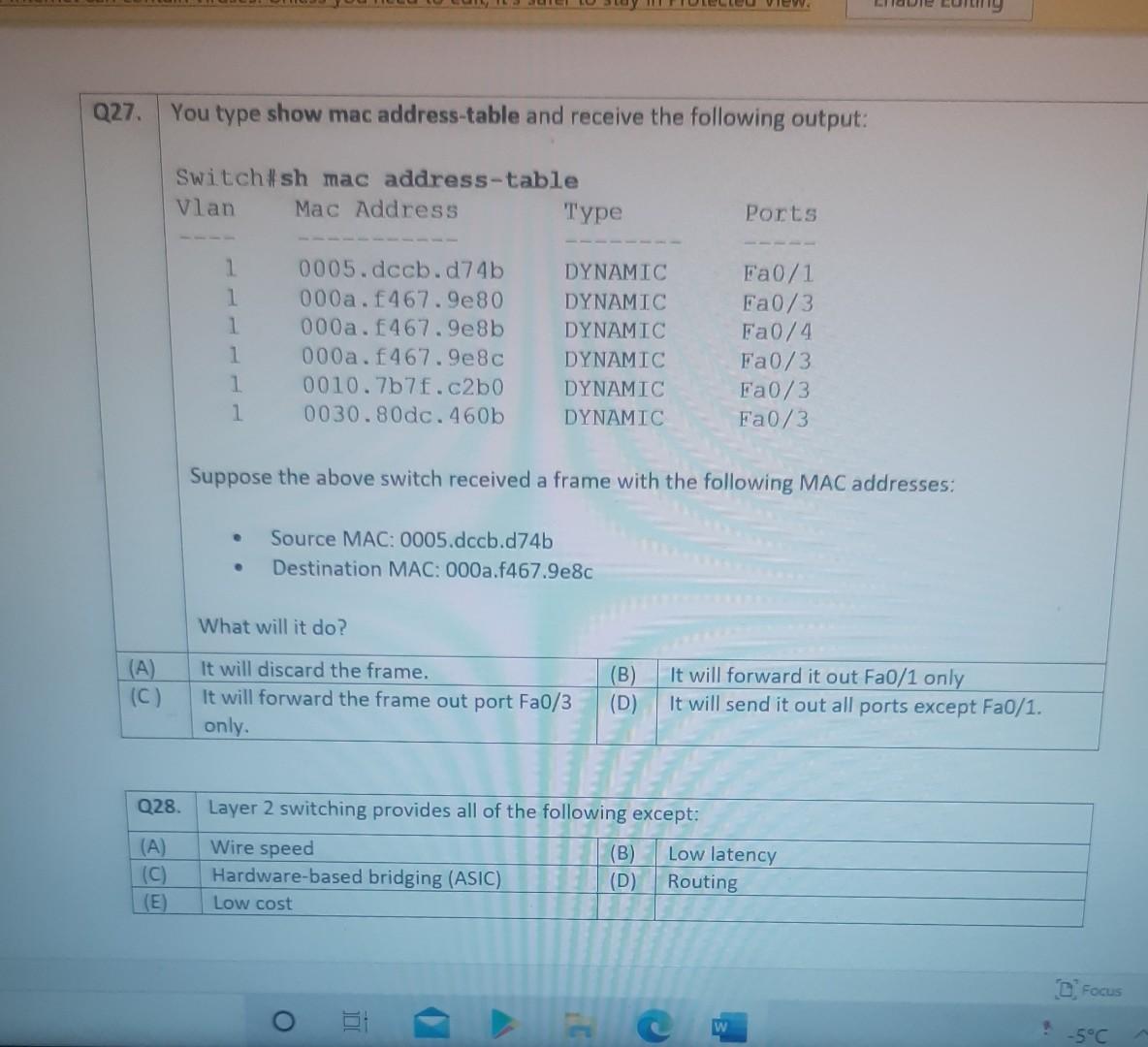
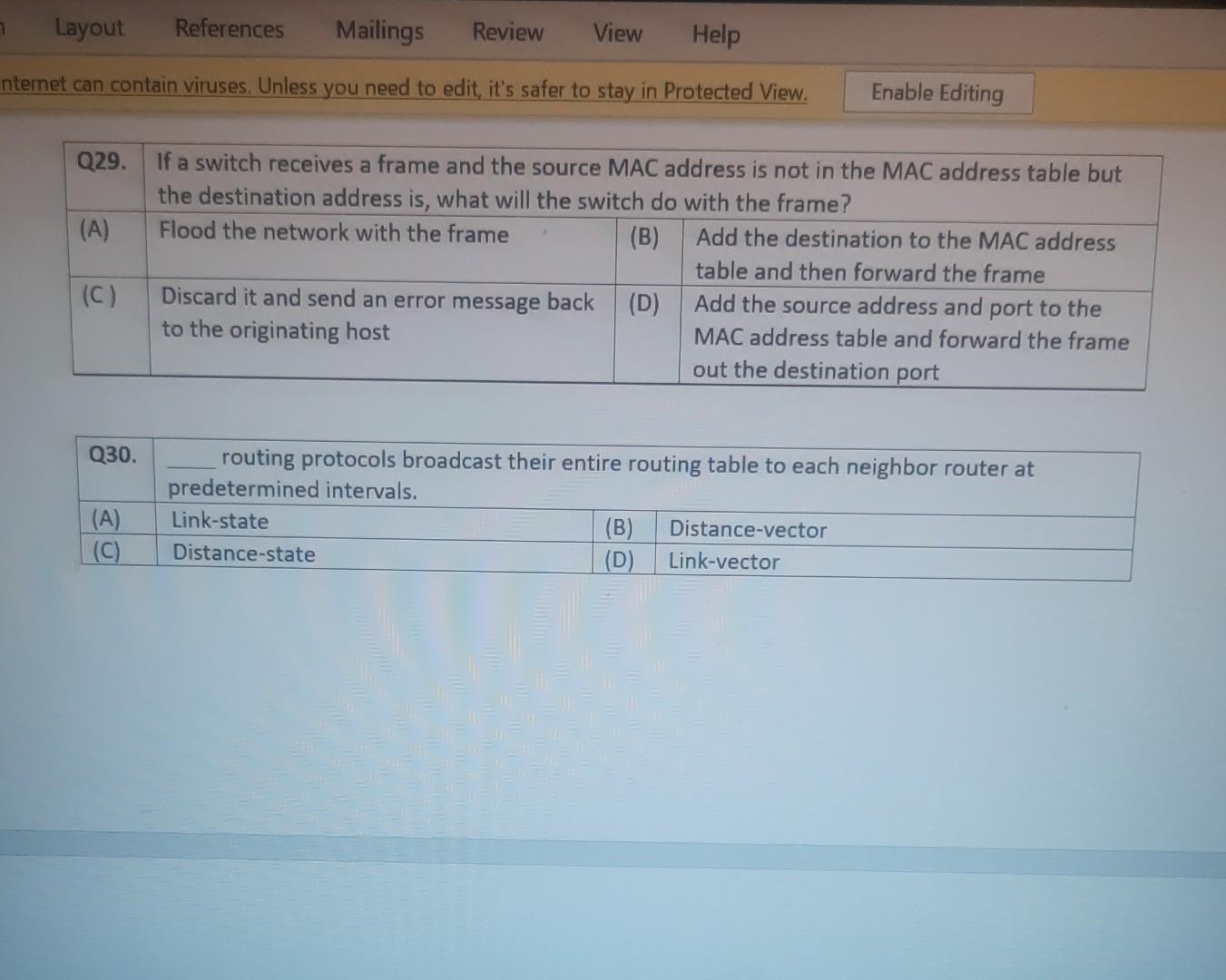
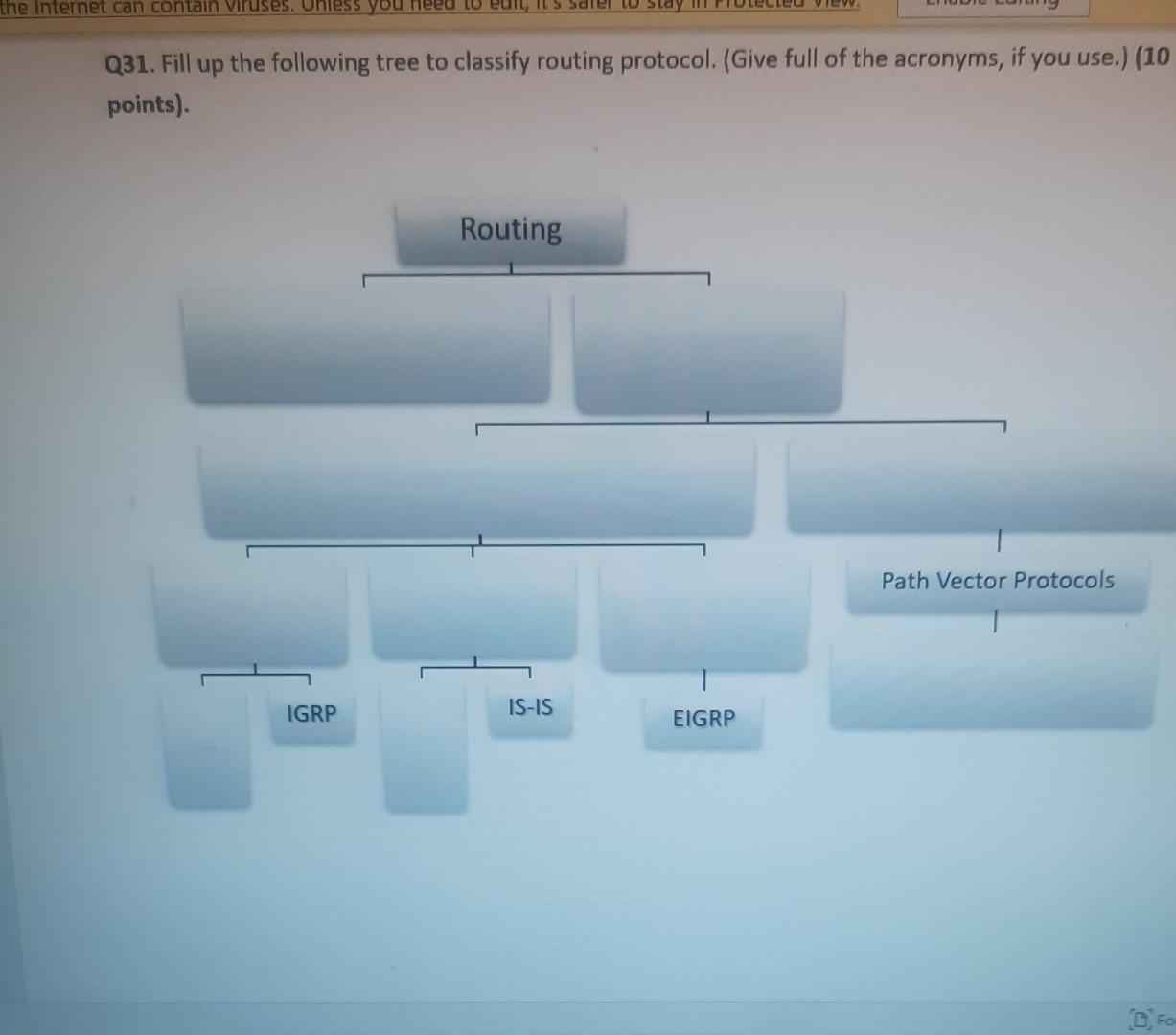
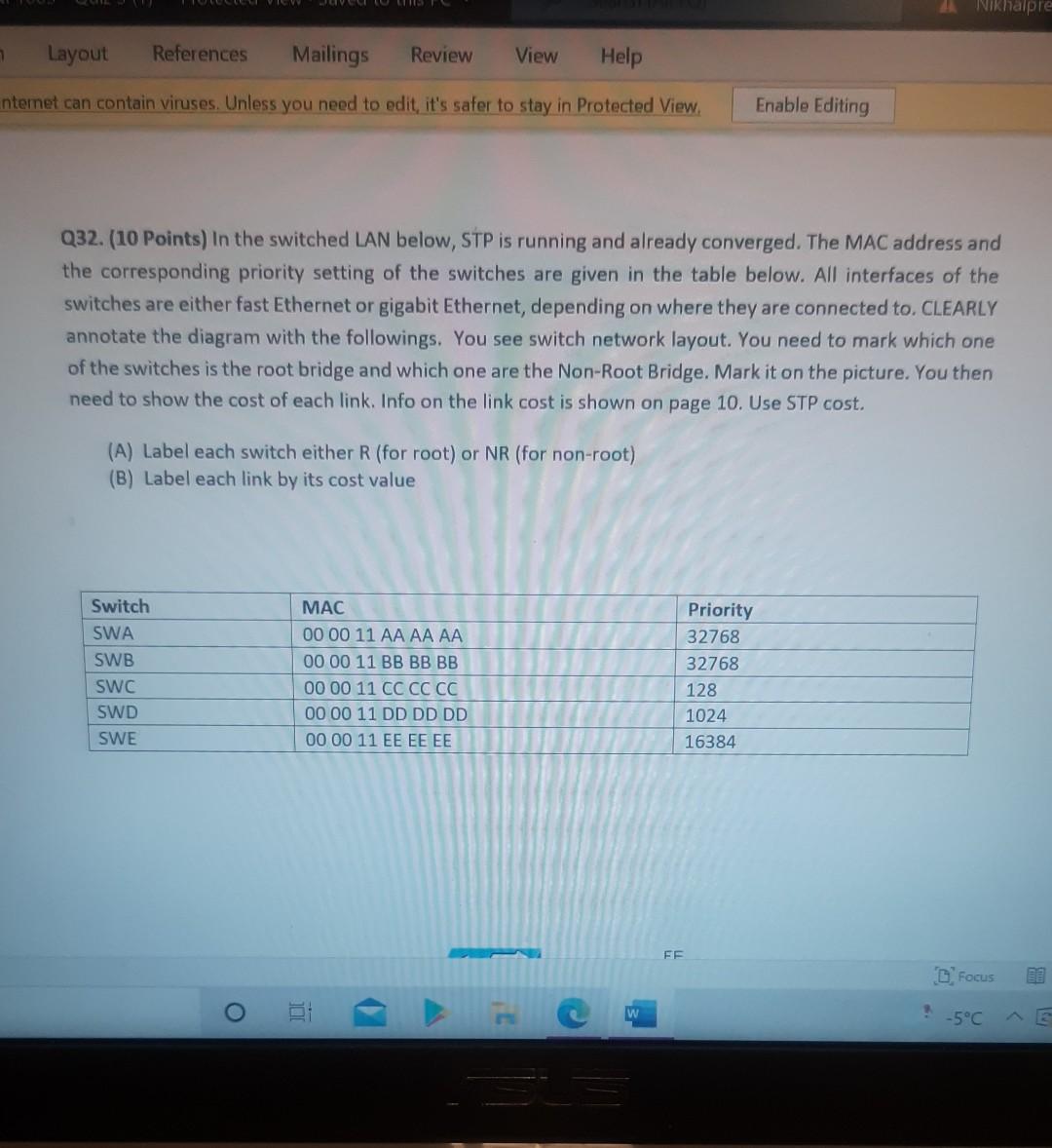
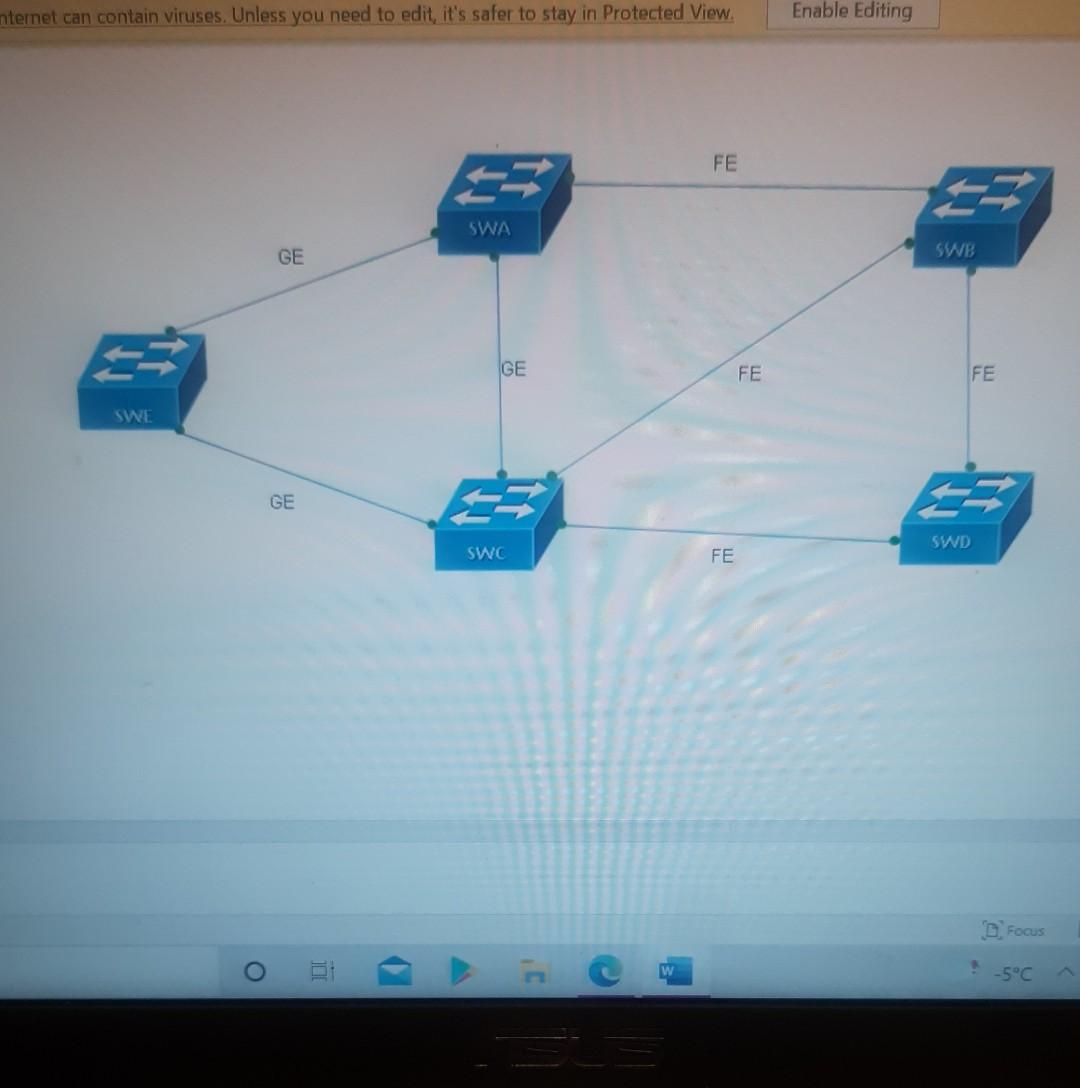
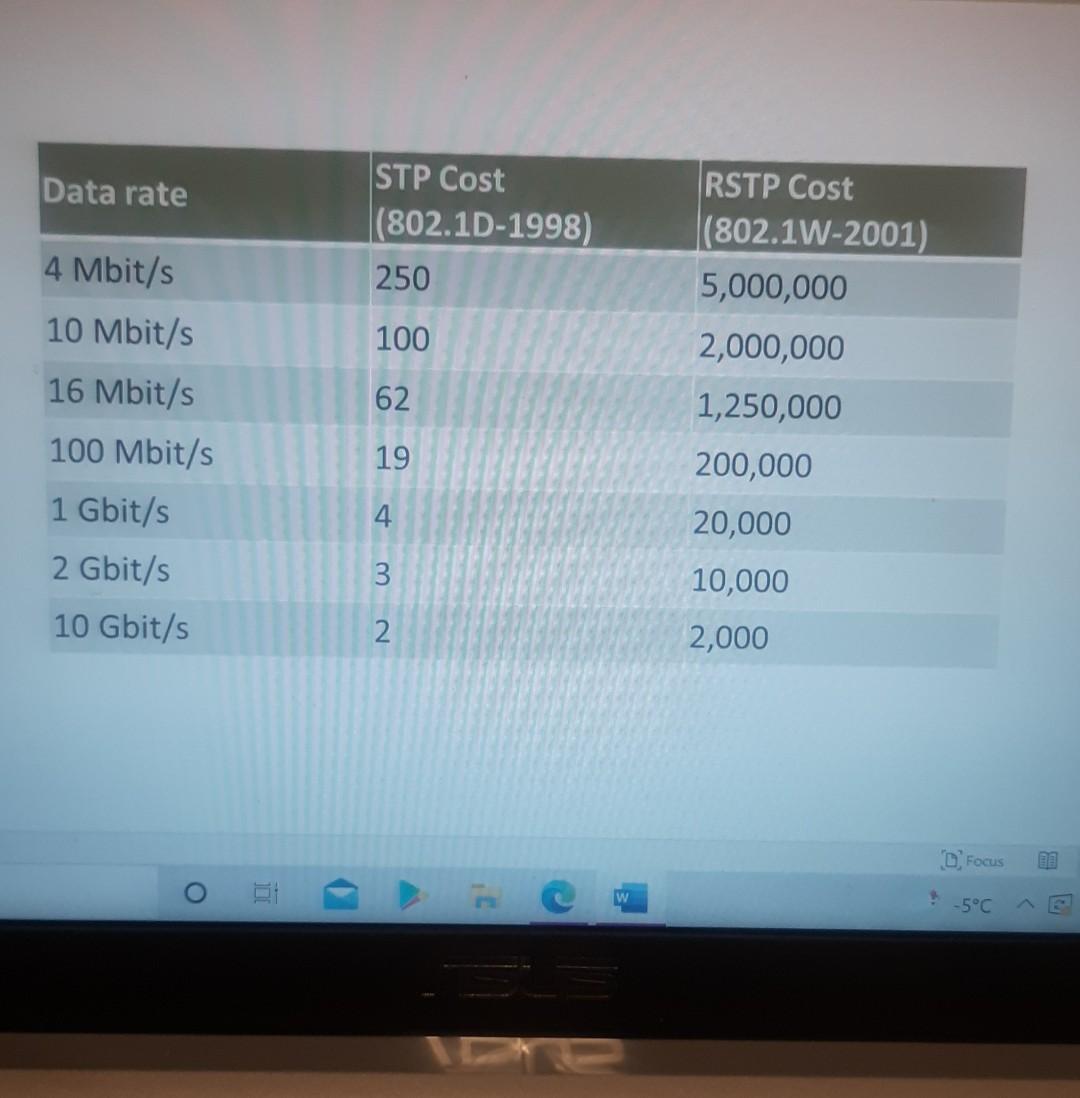
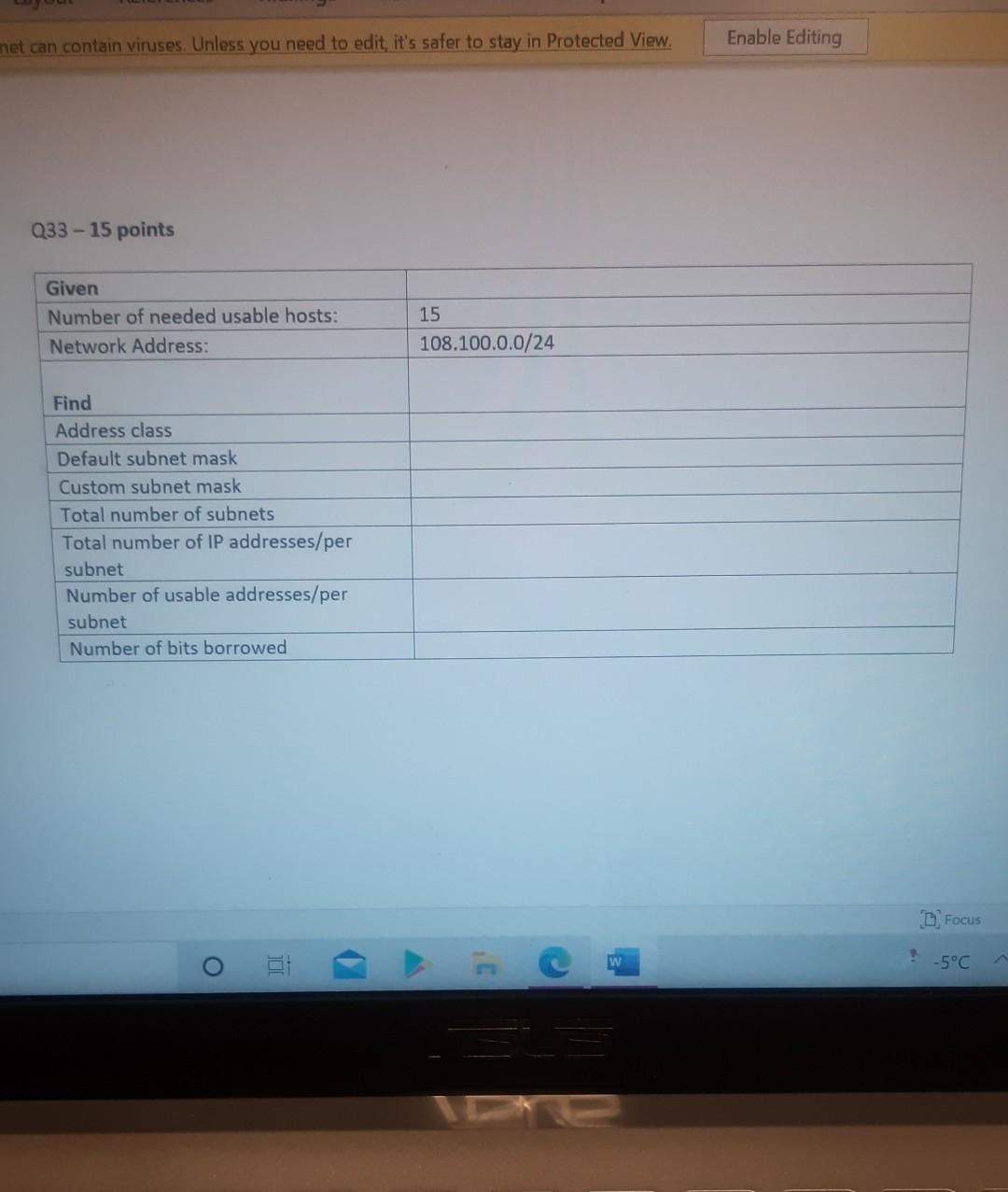
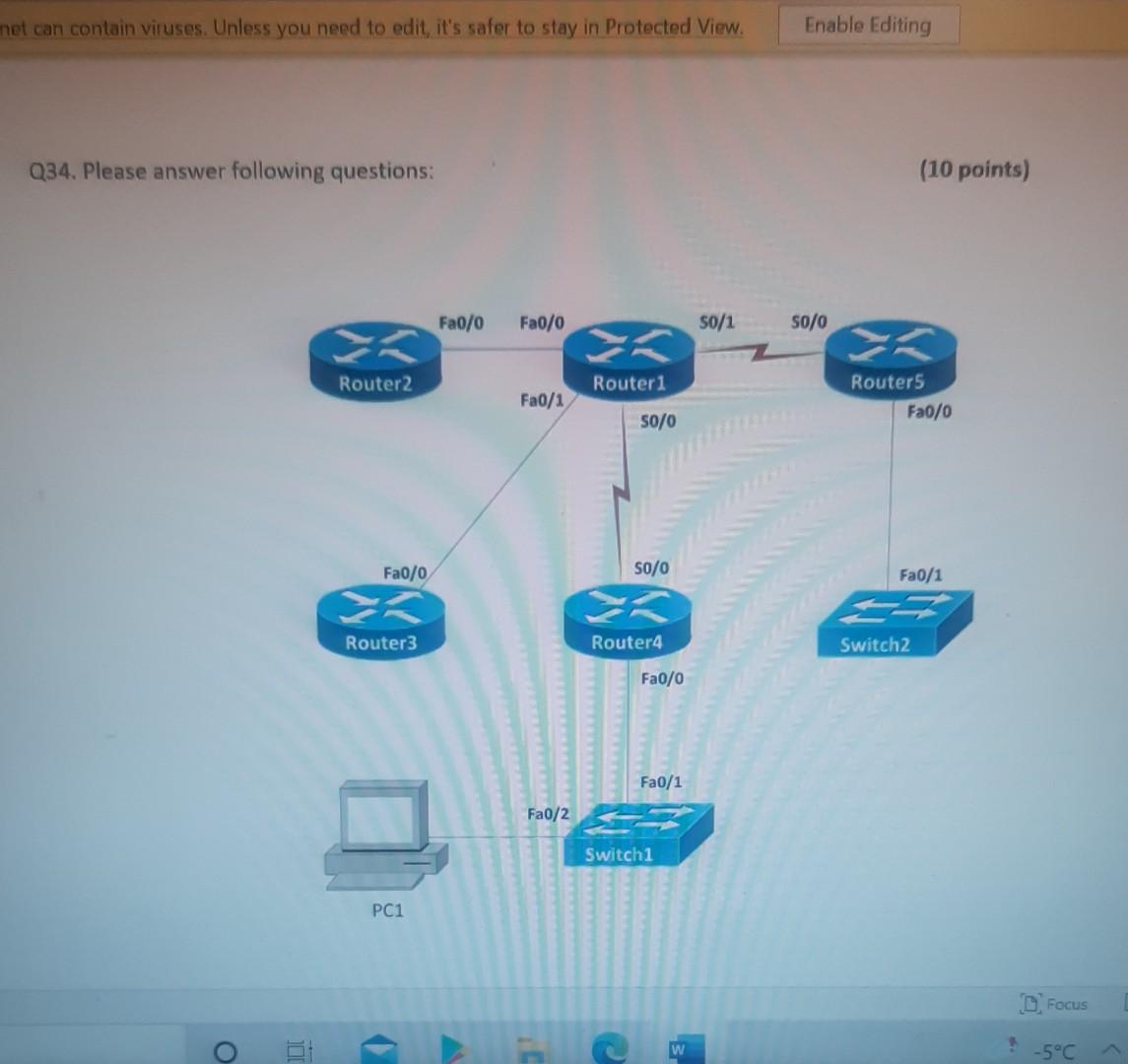
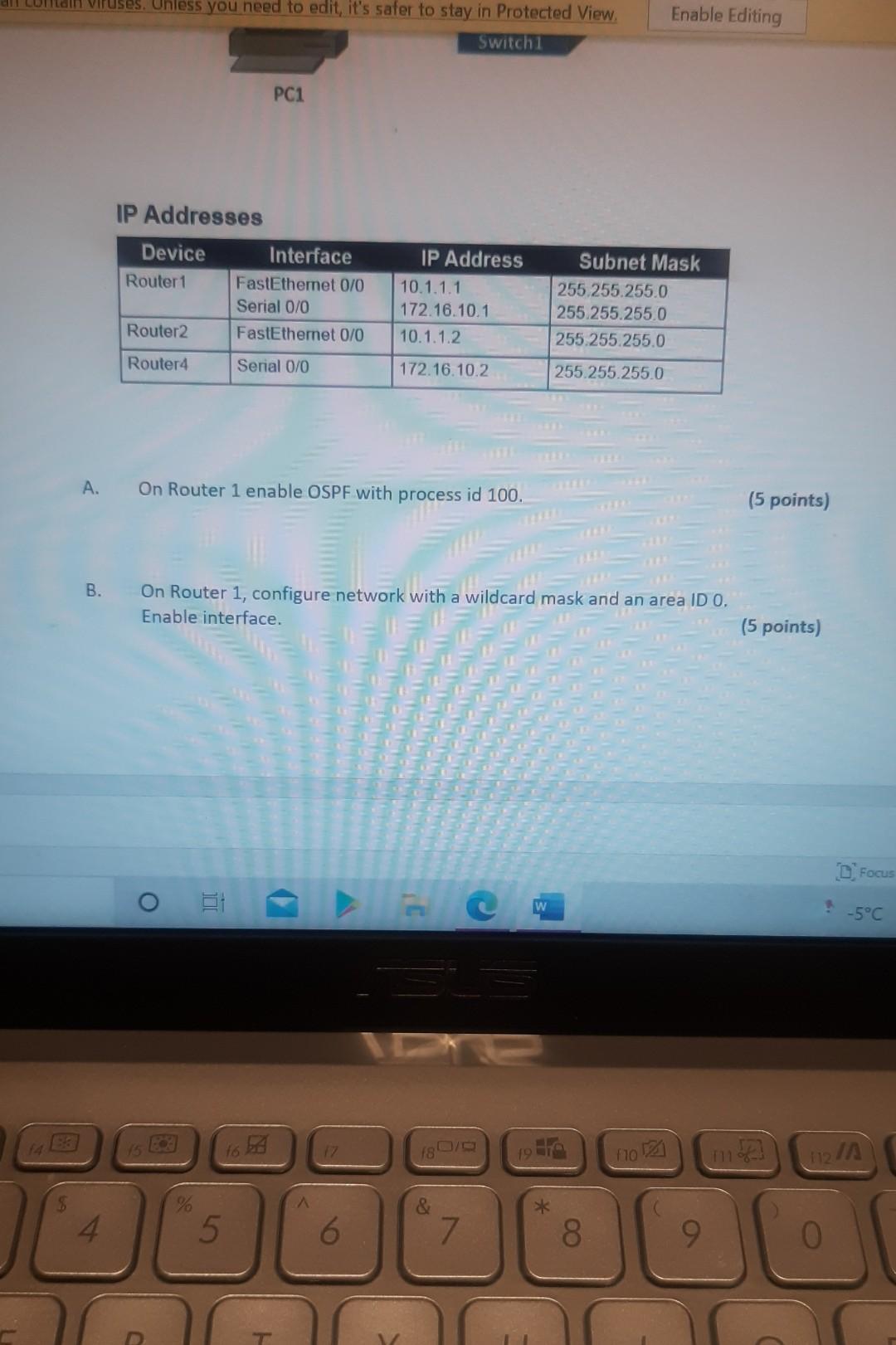
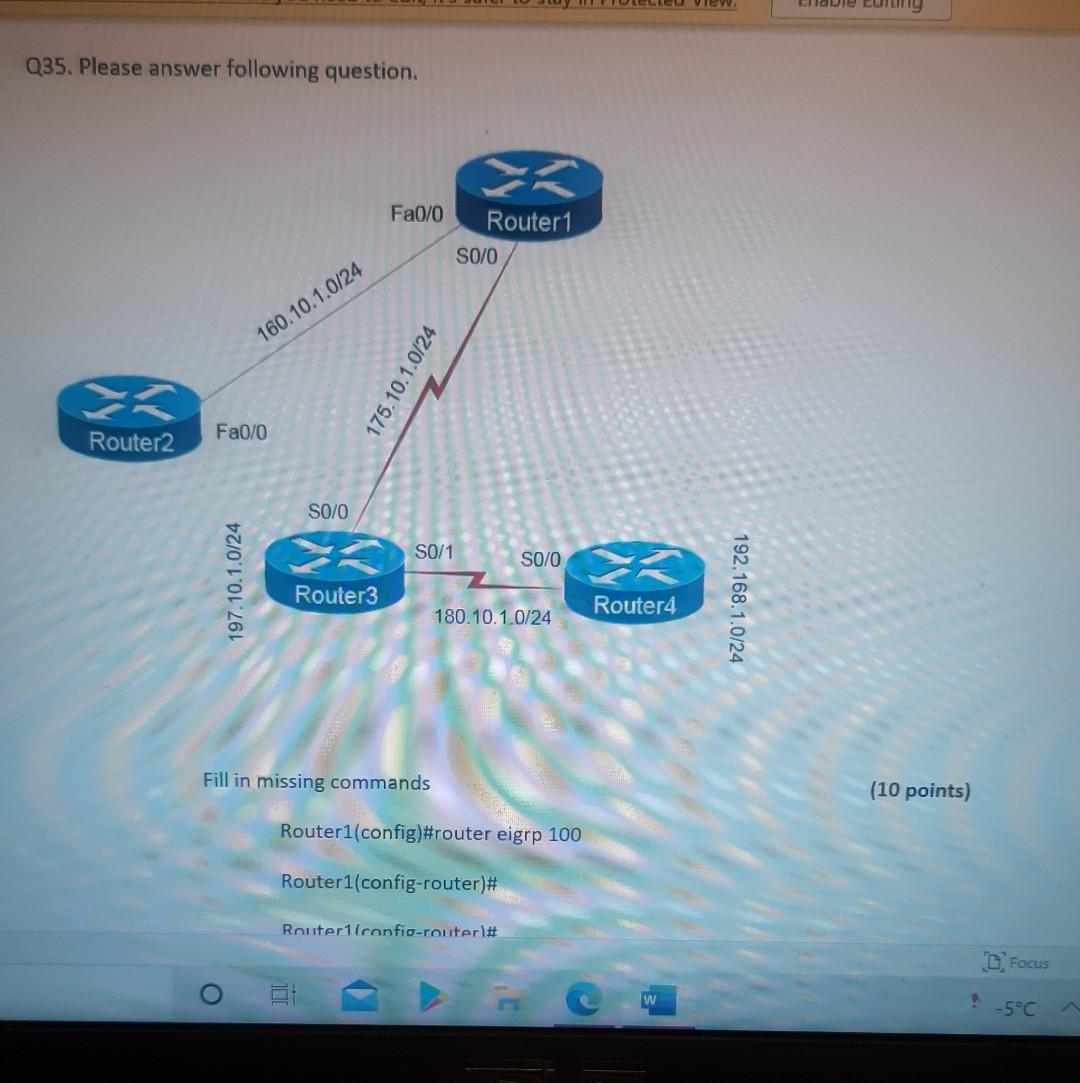
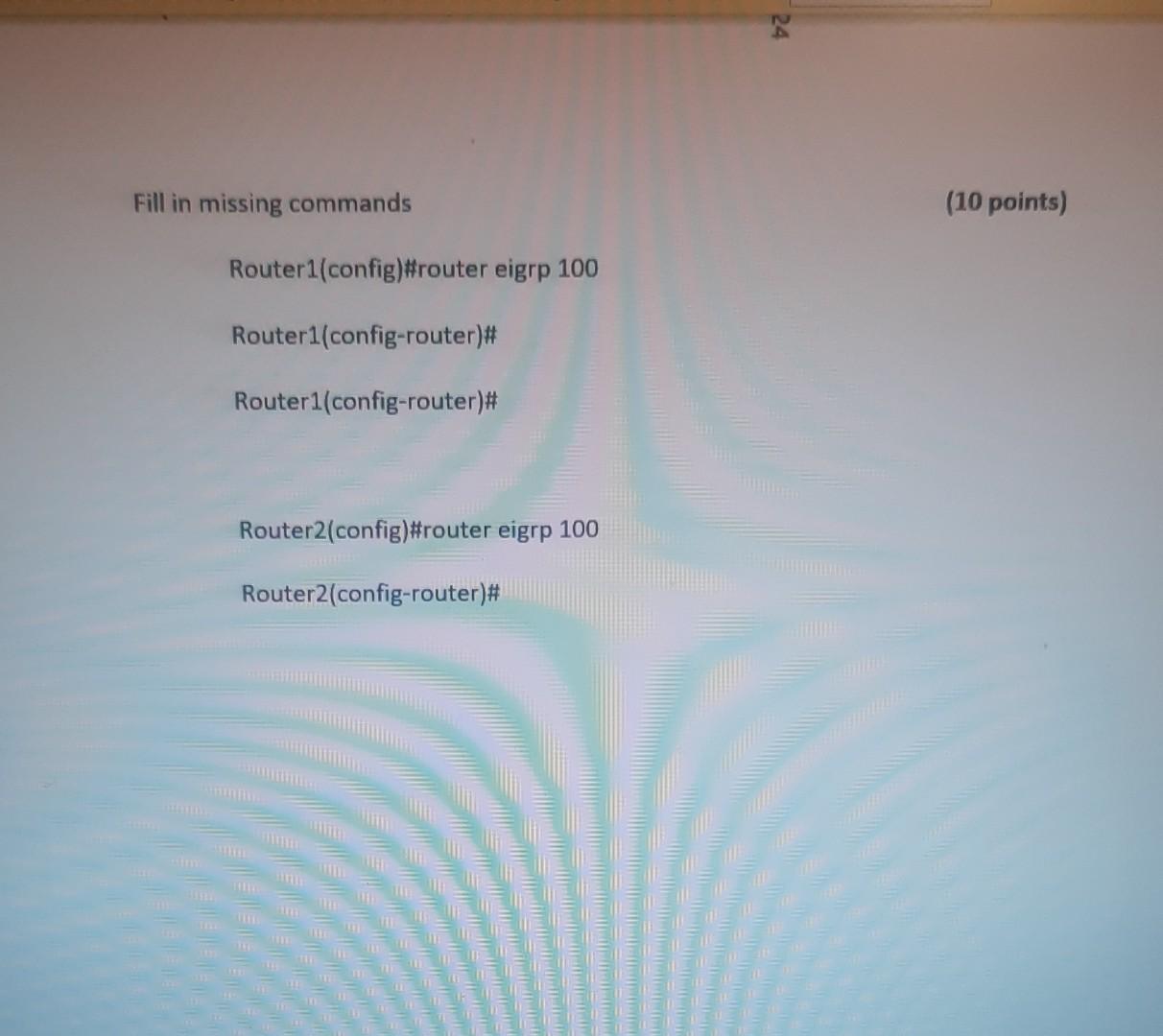
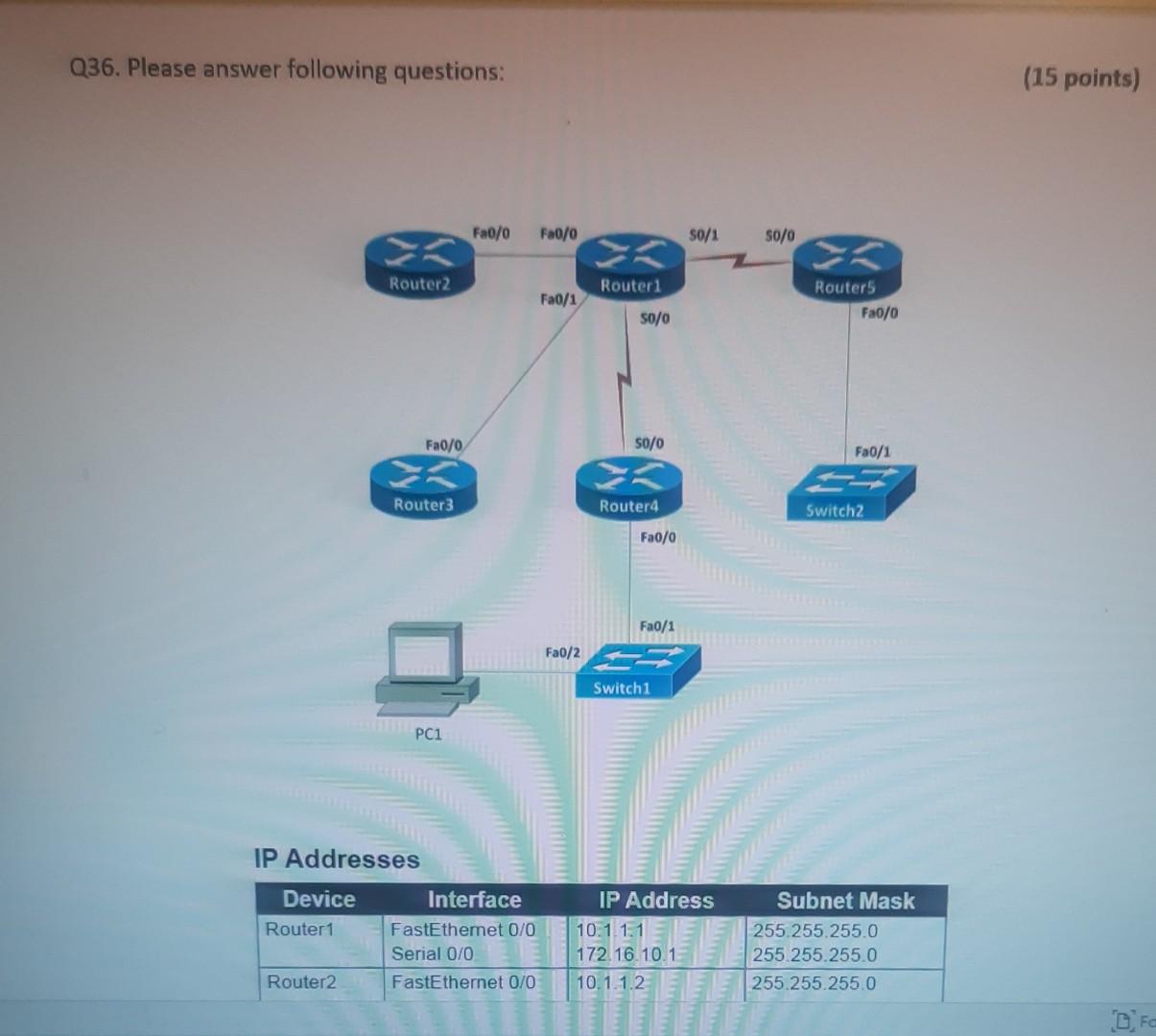
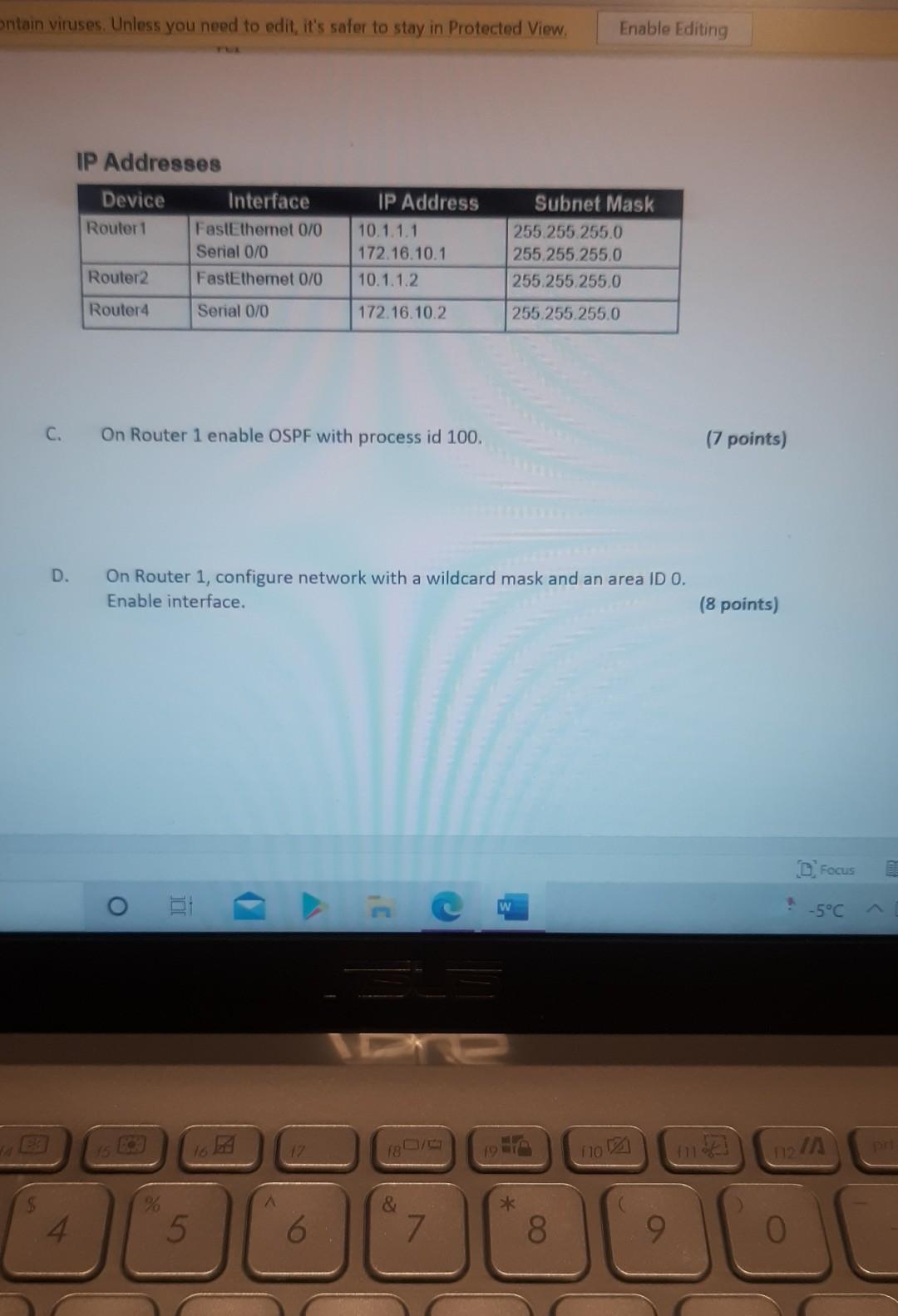
Nererences Mailings Review View Help Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Match each item with a statement below (Q1-05): (A) Access lists (B) Extended IP access lists (C) Wildcard mask (D) Named access lists (E) Standard IP access lists Q1. permit or deny packets based only on the source address Q2. use names instead of numbers to identify themselves I Q3. built into the Cisco IOS; solve many problems associated with traffic flow and security 04. filter by source IP address, destination IP address, protocol type, and application port number Q5. determines which bits of the source address are significant Focus TDI - 50 Layout References Mailings Review View Help the Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Match each item with a statement below(Q6-010): (A) STP (B) Frame tagging (C) Transitory state (D) VLAN trunking protocol (E) OSPF Q6. involves adding a four-byte field to the actual Ethernet frame to identify the VLAN and other pertinent information Q7. prevents logical loops during a period of transition from one root bridge to another I Q8. manages all of the configured VLANs that traverse trunks between switches D Focus 0 - -5C Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View Enable Editing 09. a layer 2 link management protocol designed to prevent looping on bridges and switches Q10. an open standard IGP for routing Answer questions 11-15 in relation to the scenario below. While checking the IP configuration of a PC, you found that the IP address is set to 192.168.10.70 and the subnet mask is set to be 255.255.255.224. Q11. What is subnet address of the subnet where the PC belongs? (A) (C) (E) 192.168.10.70 192.168.10.224 None of these (B) (D) 192.168.10.64 192.168.10.0 Q12. What is the directed broadcast address of the subnet? (A) (C) (E) 192.168.10.223 192.168.10.95 None of these (B) (D) 255.255.255.223 255.255.255.255 Q13. What is maximum number of host that can be added to the LAN? Focus w -5C new. Enable Editing Q13. What is maximum number of host that can be added to the LAN? (A) (C) (E) 254 62 None of these (B) (D) 30 126 Q14. What is the subnet mask in CIDR notation? (A) (C) (E) /26 /28 (B) (D) /27 /24 Q15. If last usable address in the subnet is set to the gateway router, what would be the default gateway setting of the PC? (A) (C) 192.168.10.94 192.168.10.62 (B) (D) 192.168.10.30 192.168.10.14 nternet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Q16. (A) Which of the followings is (are) not true regarding the distance-vector and link-state routing protocols? Link state sends updates containing the (B) Link state sends its complete routing table state of its own links to all routers in the out all active interfaces when some changes internetwork happen Distance vector sends its complete (D) Distance vector sends updates containing routing table out all active interfaces at the state of its own links to all routers in the periodic time intervals. internetwork (B) and (D) (C) (E) Q17. If your routing table has a static, a RIP, and an OSPF route to the same network, which route will be used to route packets by default? (A) (C) (E) They will all load-balance. RIP route Any available route (B) (D) Static route EIGRP route Q18. (A) Which switch would STP choose to become the root bridge in the selection process? 32768: 11-22-33-44-55-66 (B) 32768: 22-33-44-55-66-77 (C) 32769: 11-22-33-44-55-65 (D) 32769: 22-33-44-55-66-78 Q19. (A) (C) (E) What metric does RIPv2 use to find the best path to a remote network? Load (B) Cumulative interface delay Hop count (D) Path bandwidth value MTU Focus o - w -5C E Layout References Mailings Review View Help Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Q20. (A) Two connected routers are configured only with RIP routing. What will be the result when a router receives a routing update that contains a higher-cost path to a network already in its routing table? The updated information will replace the (B) The updated information will be added to existing routing table entry. the existing routing table. The update will be ignored and no further (D) The existing routing table entry will be action will occur. deleted from the routing table and all routers will exchange routing updates to reach convergence. (0) Q21. (A) (C) Which of the following is true regarding RIPv2? It is harder to configure than RIPv1 (B) It has a lower administrative distance than (D) RIPv1 It converges faster than RIPv1 It has the same timers as RIPv1 Q22. (A) An implicit "deny" is at the start of each access list on a router. True (B) False Focus W -5C Q23. You get a call from a network administrator who tells you that he typed the following into his router: Router (config)#router ospf 1 Router (config-router) #network 20.0.0.0 255.0.0.0 area 0 He tells you he still can't see any routes in the routing table. What configuration error did the administrator make? The wildcard mask is incorrect. (B) The OSPF area is wrong. The OSPF Process ID is incorrect. The AS configuration is wrong. (A) (C) (D) Q24. You configure the following access list: access-list 110 deny top 10.1.1.128 0.0.0.63 any eq smtp access-list 110 deny top any any eq 23 access-list 110 permit ip any any int ethernet 0 ip access-group 110 out (A) What will the result of this access list be? Email and Telnet will be allowed out EO. Everything but email and Telnet will be allowed out EO. (C) (B) (D) Email and Telnet will be allowed in EO. No IP traffic will be allowed out EO. WINP1003 - Quiz 3 (1) - Protected View Saved to this PC- Dware (Al Nil Design Layout References Mailings Review View Help the Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View Enable Editing Q25. You configure the following access list: access-list 110 deny tcp 10.1.1.128 0.0.0.63 any eg 21 access-list 110 deny tcp any any eq 23 int ethernet 0 ip access-group 110 out (A) (C) What will the result of this access list be? Ftp and Telnet will be allowed out EO. Everything but Ftp and Telnet will be allowed out EO. (B) (D) Ftp and Telnet will be allowed in EO. No IP traffic will be allowed out EO. Q26. (A) (B) What is true about access control lists? Packets are compared to each line of the assess list in sequential order An implicit "deny" is at the end of each access list All of the above (C) Packets are compared with lines of the access list only until a match is made Standard Access List filters by source IP addresses only (D) (E) D Focus DO w ! -5C TOWO Q27. You type show mac address-table and receive the following output: Switch#sh mac address-table Vlan Mac Address Type Ports 1 1 1 1 1 1 0005.dccb.d74b 000a.f467.9e80 000a.f467.9e8b 000a.f467.9e8c 0010.7b7f.c2b0 0030.80dc.460b DYNAMIC DYNAMIC DYNAMIC DYNAMIC DYNAMIC DYNAMIC Fa0/1 Fa0/3 Fa0/4 Fa0/3 Fa0/3 Fa0/3 Suppose the above switch received a frame with the following MAC addresses: Source MAC: 0005.dccb.d74b Destination MAC: 000a.f467.9e8c What will it do? (A) (C) It will discard the frame. It will forward the frame out port Fa0/3 only. (B (D) It will forward it out Fa0/1 only It will send it out all ports except Fa0/1. Q28. Layer 2 switching provides all of the following except: (B) (A) (C) (E) Wire speed Hardware-based bridging (ASIC) Low cost Low latency Routing (D) C Focus O JOI w -5C 2 Layout References Mailings Review View Help Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Q29. (A) If a switch receives a frame and the source MAC address is not in the MAC address table but the destination address is, what will the switch do with the frame? Flood the network with the frame (B) Add the destination to the MAC address table and then forward the frame Discard it and send an error message back (D) Add the source address and port to the to the originating host MAC address table and forward the frame out the destination port (C) Q30. routing protocols broadcast their entire routing table to each neighbor router at predetermined intervals. Link-state (B) Distance-vector Distance-state (D) Link-vector (A) (C) the internet can contain viruses. Unless you ed to eUL ILS Sale U Q31. Fill up the following tree to classify routing protocol. (Give full of the acronyms, if you use.) (10 points) Routing Path Vector Protocols IGRP IS-IS EIGRP DF Nikmalpre Layout References Mailings Review View Help Internet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing Q32. (10 Points) in the switched LAN below, STP is running and already converged. The MAC address and the corresponding priority setting of the switches are given in the table below. All interfaces of the switches are either fast Ethernet or gigabit Ethernet, depending on where they are connected to. CLEARLY annotate the diagram with the followings. You see switch network layout. You need to mark which one of the switches is the root bridge and which one are the Non-Root Bridge. Mark it on the picture. You then need to show the cost of each link. Info on the link cost is shown on page 10. Use STP cost. (A) Label each switch either R (for root) or NR (for non-root) (B) Label each link by its cost value Switch SWA SWB SWC SWD MAC 00 00 11 AA AA AA 00 00 11 BB BB BB 00 00 11 CC CC CC 00 00 11 DD DD DD 00 00 11 EE EE EE Priority 32768 32768 128 1024 16384 SWE EF Focus O UL F -5C nternet can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Enable Editing FE SWA GE SWB GE FE FE SWE GE SWD SWC FE D Focus -5C Data rate STP Cost (802.1D-1998) 250 100 62 4 Mbit/s 10 Mbit/s 16 Mbit/s 100 Mbit/s 1 Gbit/s 2 Gbit/s 10 Gbit/s RSTP Cost (802.1W-2001) 5,000,000 2,000,000 1,250,000 200,000 20,000 10,000 19 4. 3 2. 2,000 D. Focus IC w & 5C Enable Editing net can contain viruses. Unless you need to edit, it's safer to stay in Protected View. Q33-15 points Given Number of needed usable hosts: Network Address: 15 108.100.0.0/24 Find Address class Default subnet mask Custom subnet mask Total number of subnets Total number of IP addresses/per subnet Number of usable addresses/per subnet Number of bits borrowed Focus w . -5C net can contain viruses. Unless you need to edit it's safer to stay in Protected View. Enable Editing Q34. Please answer following questions: (10 points) Fa0/0 Fa0/0 50/1 S0/0 Router2 Router1 Fa0/1 Routers Fa0/0 50/0 Fa0/0 S0/0 Fa0/1 Router3 Router4 Switch2 Fa0/0 Fa0/1 Fa0/2 Switch1 PC1 D Focus O w -5C di una vifuses. Unless you need to edit, it's safer to stay in Protected View. Switchi Enable Editing PC1 IP Addresses Device Interface Router1 FastEthernet 0/0 Serial 0/0 Router2 FastEthernet 0/0 IP Address 10.1.1.1 172.16.10.1 10.1.1.2 Subnet Mask 255.255.255.0 255.255.255.0 255.255.255.0 Router4 Serial 0/0 172.16.10.2 255.255.255.0 A. On Router 1 enable OSPF with process id 100. (5 points) B. On Router 1, configure network with a wildcard mask and an area ID O. Enable interface. (5 points) Focus O DI -5C 19 nor 1121 A & 4. 5 7 8 9 T EW Hoje Q35. Please answer following question. Fa0/0 Router1 S0/0 160.10.1.0/24 175.10.1.0/24 a Router2 Fa0/0 S0/0 S011 SO/0 197.10.1.0/24 NY Router 3 Router4 192.168.1.0/24 180.10.1.0/24 Fill in missing commands (10 points) Router1(config)#router eigrp 100 Router1(config-router)# Router1(confio-router # Focus -5C 24 Fill in missing commands (10 points) Router1(config)#router eigrp 100 Router1(config-router)# Router1(config-router)# Router2(config)#router eigrp 100 Router2(config-router)# Q36. Please answer following questions: (15 points) Fa0/0 Fa0/0 so/1 S0/0 Router2 Router1 Fa0/1 Routers Fa0/0 30/0 Fa0/0 Fa0/1 Router3 Router4 Switch2 Fa0/0 Fa0/1 Fa0/2 Switch1 PC1 IP Addresses Device Interface Router1 FastEthemet 0/0 Serial 0/0 Router2 FastEthernet 0/0 IP Address 10.1.1.1 172.16.10.1 10.1.1.2 Subnet Mask 255.255.255.0 255.255.255.0 255.255.255.0 Fo ontain viruses. Unless you need to edit it's safer to stay in Protected View Enable Editing IP Addresses Device Interface Router1 FastEthernet 0/0 Serial 0/0 Router2 FastEthemet 0/0 IP Address 10.1.1.1 172.16.10.1 10.1.1.2 Subnet Mask 255.255.255.0 255.255.255.0 255.255.255.0 Router4 Serial 0/0 172.16.10.2 255.255.255.0 C. On Router 1 enable OSPF with process id 100. (7 points) D. On Router 1, configure network with a wildcard mask and an area ID O. Enable interface. (8 points) D Focus 0 w -5C 16 A 18 no12 A & sk 4. 5 6 7 8 9 o
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


