Answered step by step
Verified Expert Solution
Question
1 Approved Answer
CST8116 Lab Exercise 06 (22W) Concept and/or Idea provided by Professor David Haley [1] Instructions The five parts of the Software Development Process as
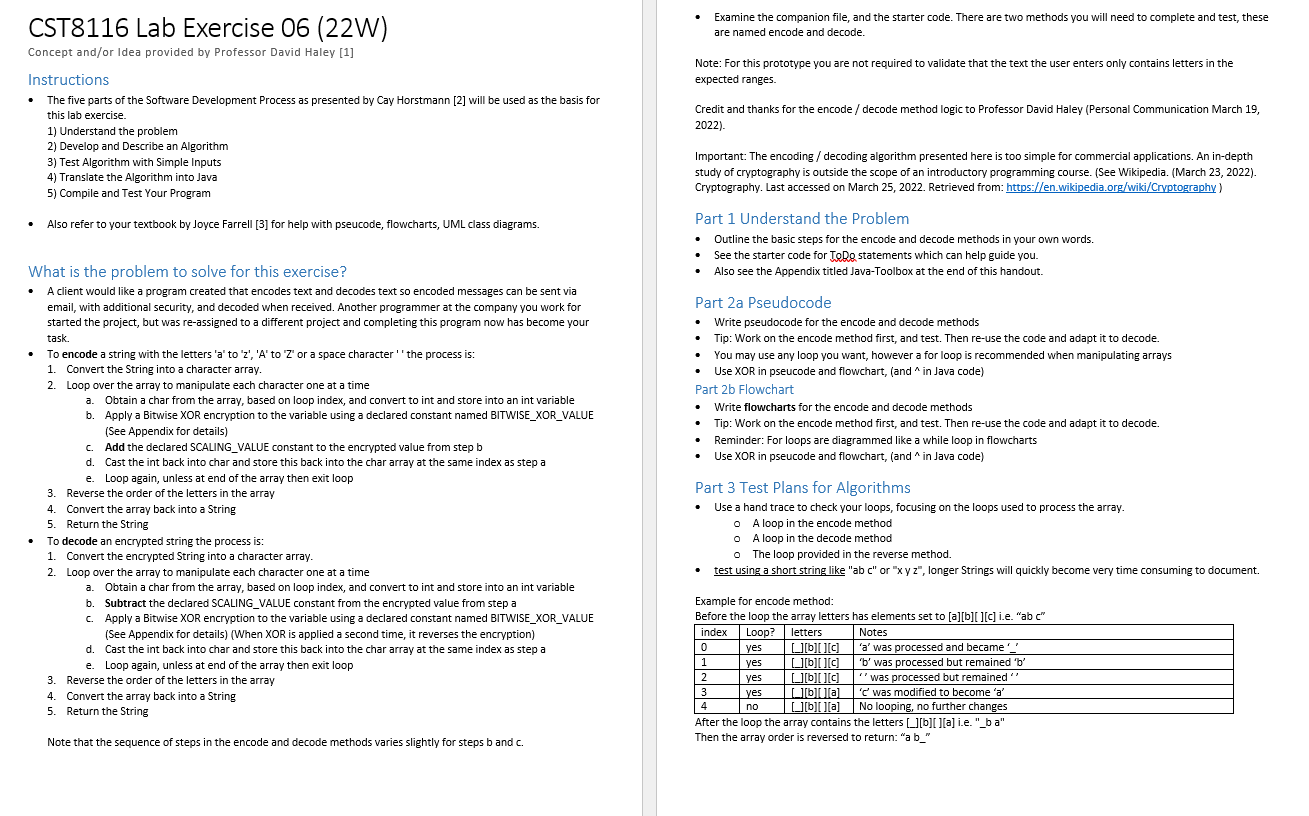
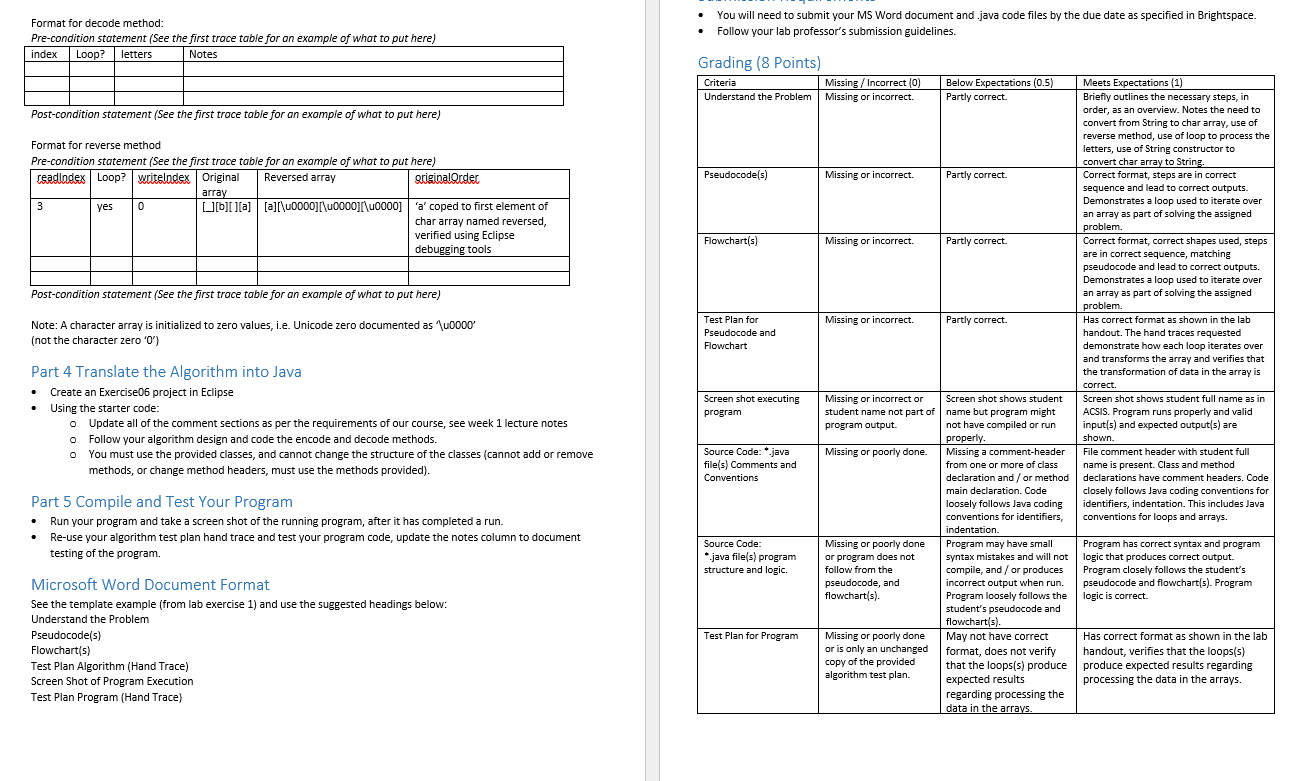

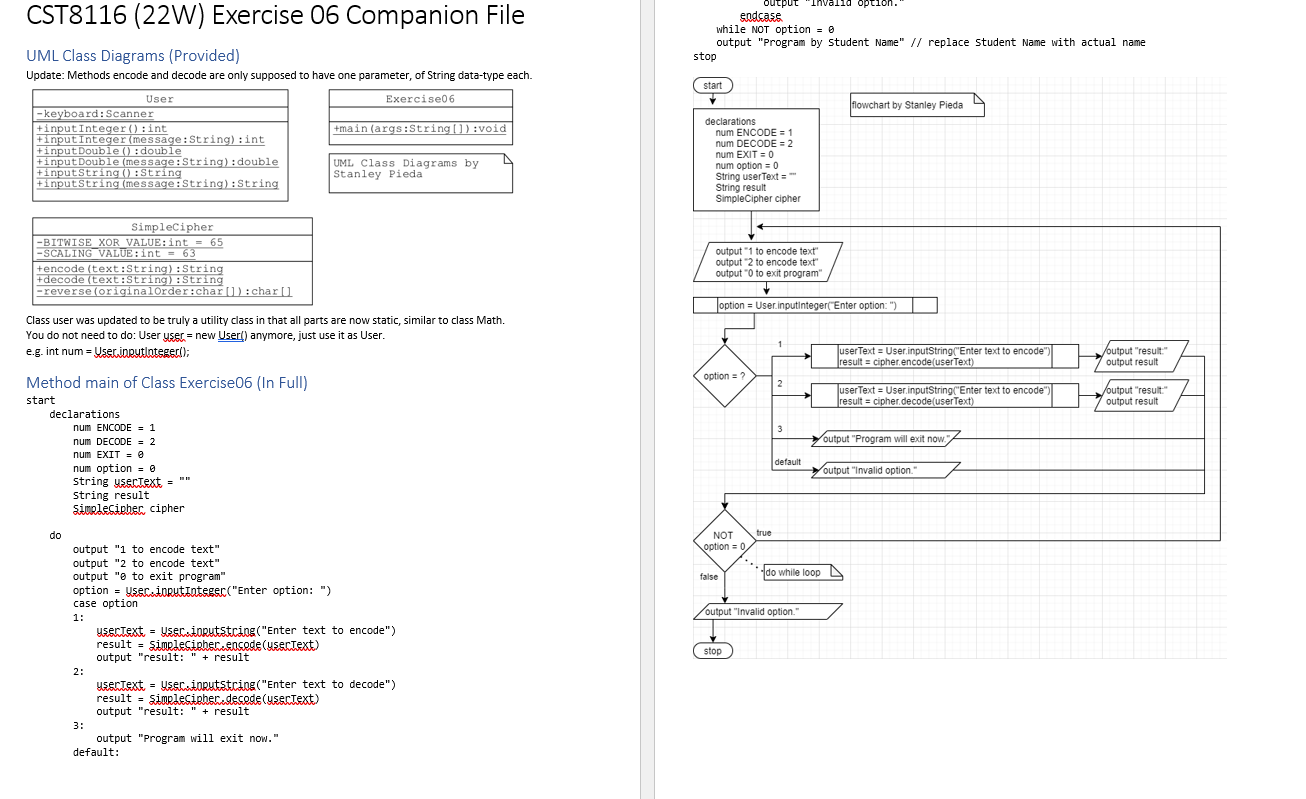
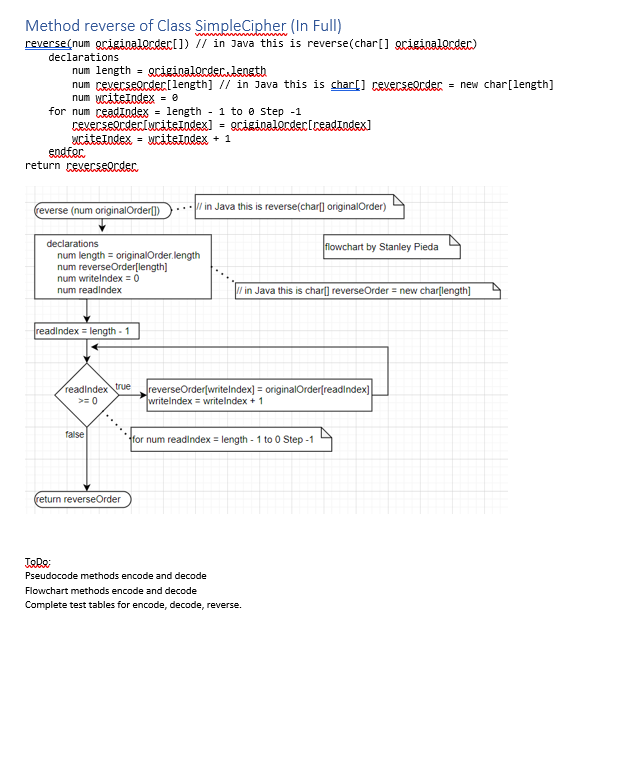
CST8116 Lab Exercise 06 (22W) Concept and/or Idea provided by Professor David Haley [1] Instructions The five parts of the Software Development Process as presented by Cay Horstmann [2] will be used as the basis for this lab exercise. 1) Understand the problem 2) Develop and Describe an Algorithm 3) Test Algorithm with Simple Inputs 4) Translate the Algorithm into Java 5) Compile and Test Your Program Also refer to your textbook by Joyce Farrell [3] for help with pseucode, flowcharts, UML class diagrams. What is the problem to solve for this exercise? A client would like a program created that encodes text and decodes text so encoded messages can be sent via email, with additional security, and decoded when received. Another programmer at the company you work for started the project, but was re-assigned to a different project and completing this program now has become your task. To encode a string with the letters 'a' to 'z', 'A' to 'Z' or a space character the process is: 1. Convert the String into a character array. 2. Loop over the array to manipulate each character one at a time a. Obtain a char from the array, based on loop index, and convert to int and store into an int variable b. Apply a Bitwise XOR encryption to the variable using a declared constant named BITWISE_XOR_VALUE (See Appendix for details) c. Add the declared SCALING_VALUE constant to the encrypted value from step b d. Cast the int back into char and store this back into the char array at the same index as step a e. Loop again, unless at end of the array then exit loop 3. Reverse the order of the letters in the array 4. Convert the array back into a String 5. Return the String To decode an encrypted string the process is: 1. Convert the encrypted String into a character array. 2. Loop over the array to manipulate each character one at a time a. Obtain a char from the array, based on loop index, and convert to int and store into an int variable b. Subtract the declared SCALING_VALUE constant from the encrypted value from step a Apply a Bitwise XOR encryption to the variable using a declared constant named BITWISE_XOR_VALUE (See Appendix for details) (When XOR is applied a second time, it reverses the encryption) d. Cast the int back into char and store this back into the char array at the same index as step a e. Loop again, unless at end of the array then exit loop 3. Reverse the order of the letters in the array 4. Convert the array back into a String 5. Return the String Note that the sequence of steps in the encode and decode methods varies slightly for steps b and c. Examine the companion file, and the starter code. There are two methods you will need to complete and test, these are named encode and decode. Note: For this prototype you are not required to validate that the text the user enters only contains letters in the expected ranges. Credit and thanks for the encode/ decode method logic to Professor David Haley (Personal Communication March 19, 2022). Important: The encoding / decoding algorithm presented here is too simple for commercial applications. An in-depth study of cryptography is outside the scope of an introductory programming course. (See Wikipedia. (March 23, 2022). Cryptography. Last accessed on March 25, 2022. Retrieved from: https://en.wikipedia.org/wiki/Cryptography) Part 1 Understand the Problem Outline the basic steps for the encode and decode methods in your own words. See the starter code for JoDo statements which can help guide you. Also see the Appendix titled Java-Toolbox at the end of this handout. Part 2a Pseudocode Write pseudocode for the encode and decode methods Tip: Work on the encode method first, and test. Then re-use the code and adapt it to decode. You may use any loop you want, however a for loop is recommended when manipulating arrays Use XOR in pseucode and flowchart, (and ^ in Java code) Part 2b Flowchart Write flowcharts for the encode and decode methods Tip: Work on the encode method first, and test. Then re-use the code and adapt it to decode. Reminder: For loops are diagrammed like a while loop in flowcharts Use XOR in pseucode and flowchart, (and ^ in Java code) Part 3 Test Plans for Algorithms Use a hand trace to check your loops, focusing on the loops used to process the array. o A loop in the encode method o A loop in the decode method o The loop provided in the reverse method. test using a short string like "ab c" or "x y z", longer Strings will quickly become very time consuming to document. Example for encode method: Before the loop the array letters has elements set to [a][b][ ][c] i.e. "ab c" index Loop? letters Notes 0 1 2 ][b][][C] 'a' was processed and became '__' [][b][][c] 'b' was processed but remained 'b' [][b][c "'was processed but remained" bla 'c' was modified to become 'a' 4 No looping, no further changes [b][][a] After the loop the array contains the letters [][b][ ][a] i.e. "_ba" Then the array order is reversed to return: "a b_" 3 yes yes yes yes no Format for decode method: Pre-condition statement (See the first trace table for an example of what to put here) index Loop? letters Notes Post-condition statement (See the first trace table for an example of what to put here) Format for reverse method Pre-condition statement (See the first trace table for an example of what to put here) readlndex Loop? writelndex Original Reversed array 3 yes 0 o o 0 array [][b][ ][a][a][\u0000][\u0000][\u0000] Post-condition statement (See the first trace table for an example of what to put here) Note: A character array is initialized to zero values, i.e. Unicode zero documented as '\u0000' (not the character zero '0') originalOrder 'a' coped to first element of char array named reversed, verified using Eclipse debugging tools Part 4 Translate the Algorithm into Java Create an Exercise06 project in Eclipse Using the starter code: Update all of the comment sections as per the requirements of our course, see week 1 lecture notes Follow your algorithm design and code the encode and decode methods. You must use the provided classes, and cannot change the structure of the classes (cannot add or remove methods, or change method headers, must use the methods provided). Part 5 Compile and Test Your Program Run your program and take a screen shot of the running program, after it has completed a run. Re-use your algorithm test plan hand trace and test your program code, update the notes column to document testing of the program. Pseudocode(s) Flowchart(s) Test Plan Algorithm (Hand Trace) Screen Shot of Program Execution Test Plan Program (Hand Trace) Microsoft Word Document Format See the template example (from lab exercise 1) and use the suggested headings below: Understand the Problem You will need to submit your MS Word document and .java code files by the due date as specified in Brightspace. Follow your lab professor's submission guidelines. Grading (8 Points) Criteria Missing/Incorrect (0) Understand the Problem Missing or incorrect. Pseudocode(s) Flowchart(s) Test Plan for Pseudocode and Flowchart Screen shot executing program Source Code: *.java file(s) Comments and Conventions Source Code: *java file(s) program structure and logic. Test Plan for Program Missing or incorrect. Missing or incorrect. Missing or incorrect. Missing or incorrect or student name not part of program output. Missing or poorly done. Missing or poorly done or program does not follow from the pseudocode, and flowchart(s). Missing or poorly done or is only an unchanged copy of the provided algorithm test plan. Below Expectations (0.5) Partly correct. Partly correct. Partly correct. Partly correct. Screen shot shows student name but program might not have compiled or run properly. Missing a comment-header from one or more of class declaration and/or method main declaration. Code loosely follows Java coding conventions for identifiers, indentation. Program may have small syntax mistakes and will not compile, and/or produces incorrect output when run. Program loosely follows the student's pseudocode and flowchart(s). May not have correct format, does not verify that the loops(s) produce expected results regarding processing the data in the arrays. Meets Expectations (1) Briefly outlines the necessary steps, in order, as an overview. Notes the need to convert from String to char array, use of reverse method, use of loop to process the letters, use of String constructor to convert char array to String. Correct format, steps are in correct sequence and lead to correct outputs. Demonstrates a loop used to iterate over an array as part of solving the assigned problem. Correct format, correct shapes used, steps are in correct sequence, matching pseudocode and lead to correct outputs. Demonstrates a loop used to iterate over an array as part of solving the assigned problem. Has correct format as shown in the lab handout. The hand traces requested demonstrate how each loop iterates over and transforms the array and verifies that the transformation of data in the array is correct. Screen shot shows student full name as in ACSIS. Program runs properly and valid input(s) and expected output(s) are shown. File comment header with student full name is present. Class and method declarations have comment headers. Code closely follows Java coding conventions for identifiers, indentation. This includes Java conventions for loops and arrays. Program has correct syntax and program logic that produces correct output. Program closely follows the student's pseudocode and flowchart(s). Program logic is correct. Has correct format as shown in the lab handout, verifies that the loops(s) produce expected results regarding processing the data in the arrays. Appendix: Sample Program Run 1 to encode text 2 to decode text e to exit program Enter option: The exam is Monday April 18, 2022 Invalid input. Enter an integer number: 1 Enter text to encode The exam is Monday April 18, 2022 result: 2202 7, LECA? udouk e kxc sht 1 to encode text 2 to decode text e to exit program Enter option: 2 Enter text to decode 2202, lrp? w.dnak gg k.xc sht result: The exam is Monday April 18, 2022 1 to encode text 2 to decode text e to exit program Enter option: 0 Program will exit now. Program by Stanley Pieda Note that the user input in the example above was formatted with bold text and highlighted using MS Word formatting tools. Within the Eclipse IDE the default font color for user input is a light green. (It might be easier to copy and paste the result from the console when testing, rather than typing the resulting characters manually.) Also note that to test the program, the encrypted text was copied from within the console view, and then pasted for the input. Appendix: Java Tool Kit Class String Can Help! https://docs.oracle.com/en/java/javase/11/docs/api/java.base/java/lang/String.html How do I convert a String instance into an array of char? See method toCharArray() e.g. String bar = "abs"; char[] foo = bar.to.charAtrax(); How do I convert a char array into a String object? There is a constructor of class String for this. See the second code sample at the very top of the Java API String class write up page. Do Not Forget What You Have Learned! After I convert the char inside an element of the array into int, I cannot store it back into the array after encrypting or decrypting it. Review lecture notes from week 4 and consider char is a numerical type that can be promoted to int for math (widening conversion) however going from int back to char (narrowing conversion) is not automatic. You will need to cast back to char before you can assign the new value back into the array element. e.g. Accessibility: Good to go int numericCode = letters[i]; // letters is array of char, is a loop index // do the encryption / decryption steps to numericCode letters[] = (char)( numericCode) // cast numericCode back to char, before placing into array at index i What is Bitwise XOR Operator? i.e. ^ Overview Logically XOR is similar to AND or QB, however for XOR: The only time XOR is false, is if both operands are the same. So true XOR true is false // note this one, true and true are the same so false false XOR true is true true XOR false is true false XOR false is false In your program, you might have lines of code like this in the encode method (the decode method subtracts the scaling value before the XOR)(... feel free to re-use inside your loop) // convert from char to int letterNumber = letters[index]; // Bitwise XOR encryption letterNumber = letterNumber ^ BITWISE_XOR_VALUE; // Scale result to a printable value letterNumber = letterNumber+ SCALING_VALUE; // convert from int to char letters[index] = (char)letterNumber; Where the letterNumber and BITWISE_XOR_VALUE variables are integer, each will have 32 bits, each bit a zero or a 1 BITWISE_XOR_VALUE set to 65 has a binary representation of: 00000000000000000000000001000001 If the extracted letter Number is for 'B' the int value is 66, and the binary is: 000000000000000000000000 01000010 The ^operator will examine the bits and report false(i.e. 0) if they are the same, or true(i.e. 1) if they are different, bit by bit from left to right. letter Number Bitwise XOR BITWISE_XOR_VALUE 0000000000000000 00000000 01000001 000000000000000000000000 01000010 A JetterNumber 00000000000000000000000000000011 Vertically if the 0 or 1 are the same the resulting value is 0 (false), if they are different the value is 1 (true). The resulting value stored as 0000000000000000 00000000 00000011, represents the number 3. So we add 63 as the SCALING_VALUE so that it becomes a visible letter, 63 +3 is 66 i.e. the letter B (oddly) (Rest assured not every letter will result in itself, so far in testing only b and a space-character have this result) Note: the binary values in the write-up above were calculated using the Signed Integer (32bit) converter website by Franois Grondin, (2022), as well as with reference to the ASCII table by RapidTables.com (n.d.) Focus 80 CST8116 (22W) Exercise 06 Companion File UML Class Diagrams (Provided) Update: Methods encode and decode are only supposed to have one parameter, of String data-type each. Exercise06 -keyboard: Scanner +input Integer (): int +inputInteger (message: String): int +input Double ():double +inputDouble (message:String): double +inputString(): String +inputString (message:String): String SimpleCipher -BITWISE_XOR_VALUE: int = 65 -SCALING VALUE:int = 63 +encode (text:String): String +decode (text:String):String -reverse (originalOrder:char[]): char[] User Method main of Class Exercise06 (In Full) start declarations Class user was updated to be truly a utility class in that all parts are now static, similar to class Math. You do not need to do: User user = new User() anymore, just use it as User. e.g. int num = Useineytiateger(); do num ENCODE 1 num DECODE = 2 num EXIT = 0 num option = 0 string userText = string result Simplecieher, cipher case option 1: output "1 to encode text" output "2 to encode text" output "e to exit program" option=sec.inputInteger("Enter option: ") 2: 3: BR +main (args:String[]):void UML Class Diagrams by Stanley Pieda usertext = user.inrutstring("Enter text to encode") result = simplecipher encode(userText) output "result: " + result output "Program will exit now." default: usertext = user inputstring("Enter text to decode") result = simplesigher decode(usertext) output "result: " + result andcase while NOT option = 0 output "Program by student Name" // replace Student Name with actual name. stop start declarations num ENCODE = 1 num DECODE=2 num EXIT = 0 num option = 0 String userText=" String result SimpleCipher cipher output "1 to encode text output"2 to encode text" output "O to exit program" option=? output Invalld option. option = User.inputinteger("Enter option:") NOT option = 0, false stop true ... -1- 2 3 default do while loop output "Invalid option." flowchart by Stanley Pieda userText = User.inputString("Enter text to encode" result = cipher.encode(userText) userText = User.inputString("Enter text to encode result = cipher decode(userText) output "Program will exit now." output "Invalid option." /output "result" output result /output "result" output result Method reverse of Class SimpleCipher (In Full) reverse(num griginalerdec[]) // in Java this is reverse(char[] originalonder) declarations num length = griginalorder length num ceverseorder[length] // in Java this is char[] ceverseonder = new char[length] num wciteindex = 0 for num ceadindex = length - 1 to 0 step -1 = reverseorder[writeIndex] wciteIndex = wciteindex + 1 endfer return revecssorden (reverse (num originalOrder[]) declarations num length = originalOrder.length num reverse Order[length] num writelndex = 0 num readIndex readindex = length-1 readindex true >=0 false return reverseOrder originalorder[readIndex] // in Java this is reverse(char[] originalOrder) flowchart by Stanley Pieda in Java this is char[] reverseOrder = new char[length] reverseOrder[writeIndex] = originalOrder[readindex] writelndex = writelndex + 1 for num readindex = length - 1 to 0 Step -1 ToDo: Pseudocode methods encode and decode Flowchart methods encode and decode Complete test tables for encode, decode, reverse.
Step by Step Solution
★★★★★
3.37 Rating (144 Votes )
There are 3 Steps involved in it
Step: 1
HAProjectMethodsjava Program Name HAProjectMethodsjava Purpose This class stores all the methods used for the Caesar project HARegularCaesarjava Imports Scanner class from the utility package import j...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


