Decoding/ Canadian Security Intelligence Service Computer Engineering Assignment


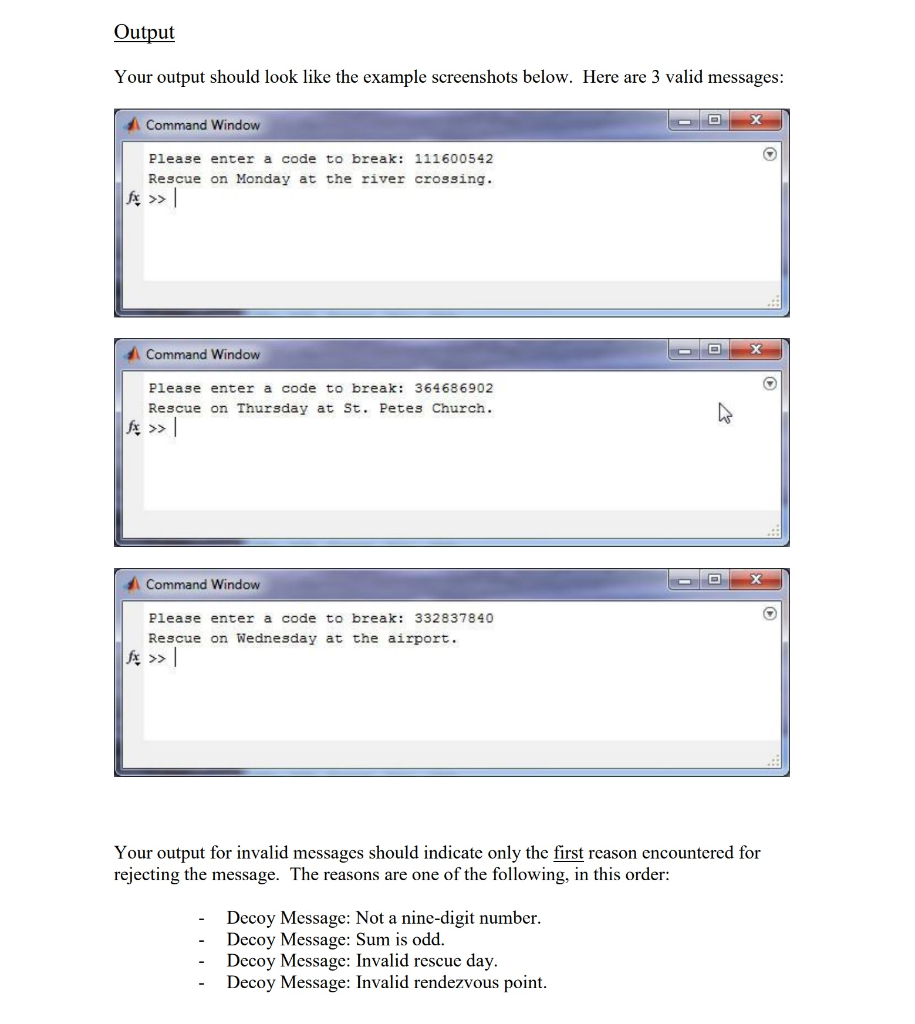
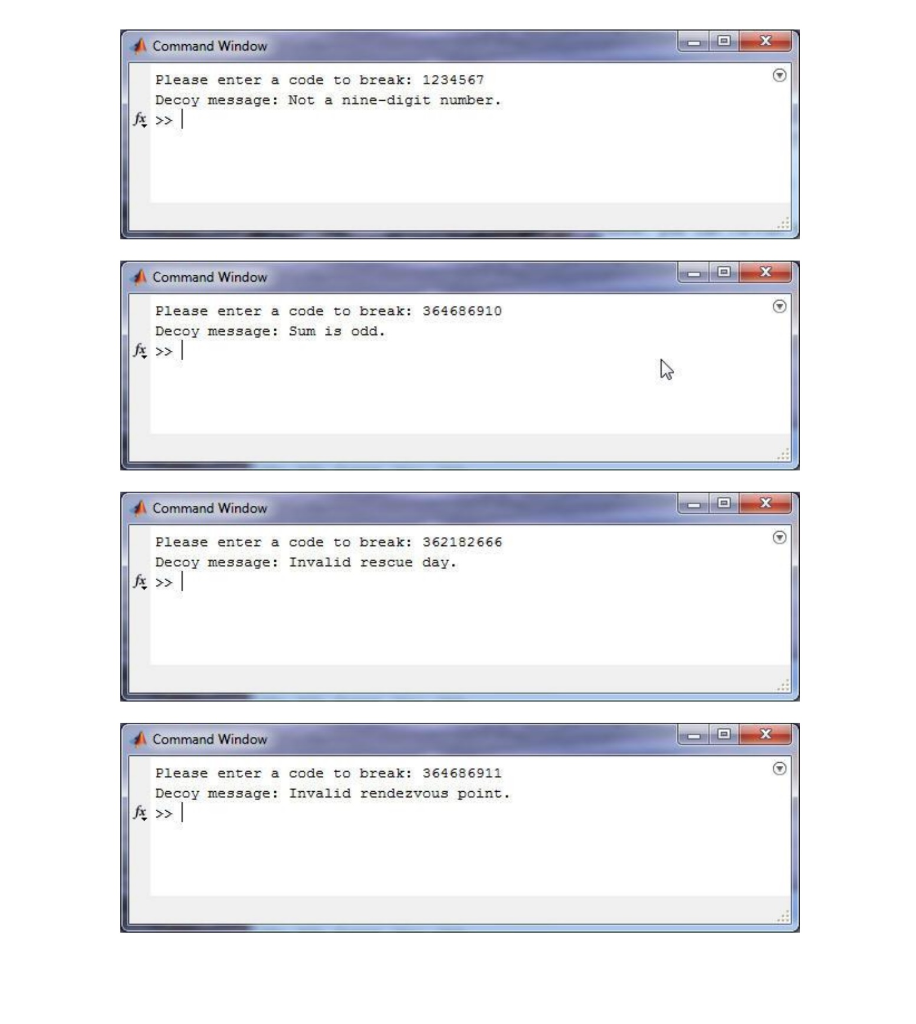


Background Your friend Maverick recently landed a lucrative engineering co-op work term in an oil- rich country. Meanwhile, you chose to make a modest salary as a co-op intern with the Canadian Security Intelligence Service (CSIS). A week after arriving in the foreign country, Maverick is kidnapped by rebels opposed to oil exploration. He is held captive in a small village within rebel territory. Luckily, a group of disenchanted rebels are willing to smuggle Maverick to one of seven rendezvous points: - the village bridge the village library river crossing nearby airport bus terminal hospital at St. Pete's Church - - where an allied helicopter will pick them up and fly them to safety. For the plan to work, the friendly rebels need to know two pieces of information: - the day of the rendezvous - the rendezvous point CSIS has devised a nine-digit code to carry this information to the friendly rebels. When the time is ripe, CSIS will insert a coded message into the online newspaper of the oil- rich country, as a number on the front page. The rebels have Internet access via satellite links and follow the news. While it is helpful (as a decoy strategy) that the newspaper has other numbers on the front page, e.g. in real adverts, it is vital that the rebel insiders can detect and decode the secret message. CSIS has found a way to smuggle a decoder to the friendly rebels. You are asked to program the decoder in MATLAB. The safety of your friend Maverick depends on your ability to program the decoder correctly. Details The four rules for detecting and decoding the code are as follows: 1. A valid code must be a 9-digit number. e.g. 123456789, message MAY be valid e.g. 12345678, message invalid c.g. 1234567890, message invalid Assume that the input data contains only digits, with a non-zero first digit. 2. The code must pass the odd-even "truth test. - If the sum of the digits is odd, the message is invalid. e.g. 222222223, sum = 19, message invalid - If the sum of the digits is even, the message MAY be valid. e.g. 222222222,, sum = 18, message may be valid 3. To determine the rescue day, multiply the 1st digit by the 3rd digit, then subtract the 5th digit. The answer indicates the rescue day, as follows: 1 = Monday 2 = Tuesday 3 = Wednesday 4 = Thursday 5 = Friday 6= Saturday 7 = Sunday Any other number indicates that the message is invalid. Examples: 234567890 712245420 2x4-6 = 2 7x2-4 = 10 Rescue is on Tuesday Message is invalid. 4. To determine the rendezvous point, this is completed in two steps, first multiply the 2nd digit by the 4th digit, then subtract the 6th digit second determine if the resulting value is divisible by 3 If the following result when you multiply the 2nd digit by the 4th digit, then subtract the 6th digit is divisible by 3, then the rendezvous point is 7th digit minus 9th digit If the following result when you multiply the 2nd digit by the 4th digit, then subtract the 6th digit is not divisible by 3, then the rendezvous point is 8th digit minus 9th digit If the result is one of the following rendezvous numbers, the message is valid: Rendezvous Number 2 Rendezvous Point bridge library river crossing airport bus terminal hospital St. Petes Church 4 Any other rendezvous number means that the message is invalid Output Your output should look like the example screenshots below. Here are 3 valid messages: Command Window Please enter a code to break: 111600542 Rescue on Monday at the river crossing. Command Window Please enter a code to break: 364686902 Rescue on Thursday at St. Petes Church. >> fx Command Window Please enter a code to break: 332837840 Rescue on Wednesday at the airport. Your output for invalid messages should indicate only the first reason encountered for rejecting the message. The reasons are one of the following, in this order: - Decoy Message: Not a nine-digit number. - Decoy Message: Sum is odd. - Decoy Message: Invalid rescue day. Decoy Message: Invalid rendezvous point. Command Window Please enter a code to break: 1234567 Decoy message: Not a nine-digit number. >> fx Command Window Please enter a code to break: 364686910 Decoy message: Sum is odd. Command Window Please enter a code to break: 362182666 Decoy message: Invalid rescue day. Command Window Please enter a code to break: 364686911 Decoy message: Invalid rendezvous point. Code Requirements You are required to use two switch statements in this assignment, one to determine the rescue day and another to determine the rendezvous point. Failure to use two switch statements in this assignment will result in a mark of zero on Successful testing of the rules portion of the mark breakdown. Do not use the error function, use either disp or fprintf functions to display outputs to the command window. Hints 1. Before you even begin to write out any MATLAB code, sit down and sketch out your program design in abbreviated English. This kind of high-level program design is called pseudo code. Please see secondary link for full pseudo code of the assignment two. It would start off something like this: Get secret code from user as a string Get an array of the individual digits If code not 9 digits Output error message Else Get sum of digits If sum is odd Output error message Else Get rescue day Etc, ... Notice how the logic naturally translates into an if-else chain. The if clauses in the chain contain messages for invalid codes. After such a message is output, the control flow breaks out of the entire chain. You end up reaching the final else clause in the chain only if the code is valid. It is there that the valid message is composed and output. For the complete pseudo code for this assignment, please see second link on eClass site under Assignment #2. Please note that the posted pseudo code is a "first pass" attempt of what you should do when creating pseudo code for your assignments. 2. To help you read in a secret code from the user as a string, type in help input on the command window or search the input command using the help function. 3. When converting an array of characters (string) to an array of numbers, you need to subtract the ASCII value of zero from each character. For example, if your string is called code_str and your number array is called digits, you can do the following: digits = code_str - '0'; 4. Remember to use the built-in MATLAB functions. For example, to check if the string contains nine digits, you might find the length function helpful. To find the sum of the digits, you might find the sum function helpful. To check if the sum of digits is odd or even, you may find the mod function helpful. 5. Build up your program design in stages. After you have completed the code for Rule 1, compile and test with a variety of codes that satisfy and fail to satisfy the rule. Then go on to write the code for the next rule, etc. 6. Please remember to include your header at the top of your .m file. % Course: ENCMP 100 % Assignment: 2 % Name: Joe MacDonald % CCID: jmac % U of A ID: 1234567 % Acknowledgements: %I received help from Jason Smith on using the mod function. olo oo oo oo oo oo % Description: This program contains four rules which can be used to crack the % secret code to save Maverick the co-op student












