Answered step by step
Verified Expert Solution
Question
1 Approved Answer
definitions: Term Definition 1. a. Code that corrects Vulnerability a flaw in a program 2. b. Verification of Exploit claimed identity 3. c. The firewall

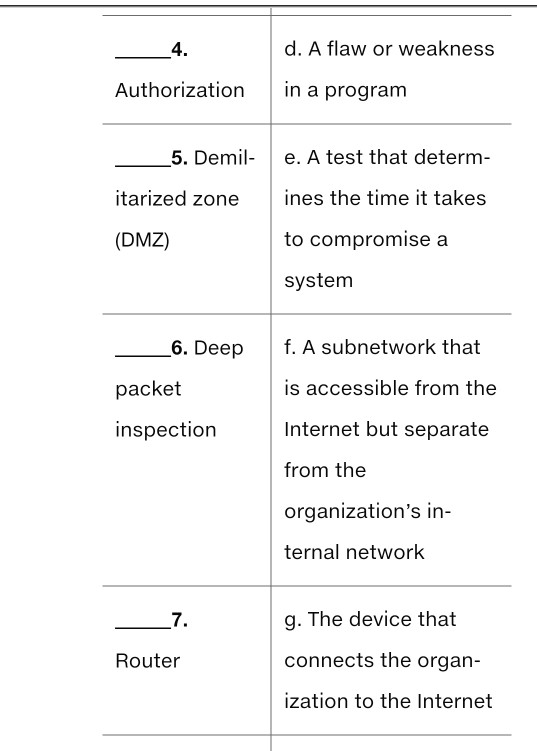
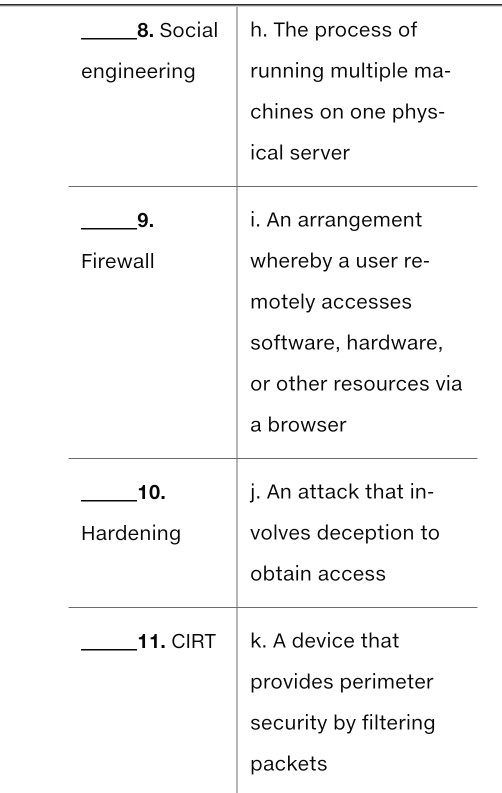

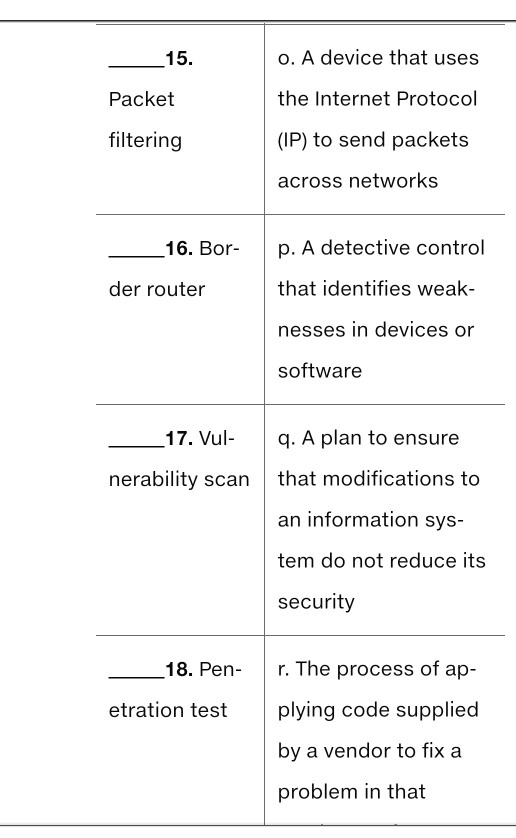

definitions: Term Definition 1. a. Code that corrects Vulnerability a flaw in a program 2. b. Verification of Exploit claimed identity 3. c. The firewall tech- Authentication nique that filters traffic by examining only the information in packet headers to the rules in an ACL 4. d. A flaw or weakness Authorization in a program 4. d. A flaw or weakness Authorization in a program 5. Demil- e. A test that determ- itarized zone ines the time it takes (DMZ) to compromise a system 6. Deep f. A subnetwork that packet is accessible from the inspection Internet but separate from the organization's in- ternal network 7. g. The device that Router connects the organ- ization to the Internet 8. Social h. The process of engineering running multiple ma- chines on one phys- ical server 9. i. An arrangement Firewall whereby a user re- motely accesses software, hardware, or other resources via a browser 10. j. An attack that in- Hardening volves deception to obtain access 11. CIRT k. A device that provides perimeter security by filtering packets 12. 1. The set of employ- Patch ees assigned re- sponsibility for resolv- ing problems and incidents 13. m. Restricting the ac- Virtualization tions that a user is permitted to perform 14. n. Improving security Change con- by removal or dis- trol and abling of unnecessary change programs and management features 15. 0. A device that uses Packet the Internet Protocol (IP) to send packets filtering across networks 15. o. A device that uses Packet the Internet Protocol filtering (IP) to send packets across networks 16. Bor- p. A detective control der router that identifies weak- nesses in devices or software 17. Vul- q. A plan to ensure nerability scan that modifications to an information sys- tem do not reduce its security 18. Pen- r. The process of ap- etration test plying code supplied by a vendor to fix a problem in that 19. S. Software code that Patch can be used to take management advantage of a flaw and compromise a system 20. t. A firewall technique Cloud that filters traffic by computing examining not just packet header in- formation but also the contents of a packet
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


