Question
Discuss how neural operators which encode, analyse and represent photo shape in herbal visible systems may be implemented in artificial neural networks. Include 4 of
Discuss how neural operators which encode, analyse and represent photo shape in herbal visible systems may be implemented in artificial neural networks. Include 4 of the subsequent troubles to your dialogue: ? receptive subject structure ? adaptiveness and perceptual learning ? hierarchies of tuning variables in successive layers of the visible pathway ? wavelet codes for extracting pattern data in fantastically compressed form ? self-similarity of weighting features ? associative memory or content-addressable reminiscence for recognising patterns which includes faces and eliciting suitable reaction sequences [20 marks] 9 Security Write brief notes on every of the subsequent: (a) the Internet Worm (b) Trojan horses (c) polymorphic viruses (d) virus exploitation of covert channels (e) the distinguishing characteristics of viruses written in interpreted languages
You are required to implement a serial factor-to-factor link the usage of application-specific VLSI chips. The velocity of the link is to be 1 gigabit/sec and the connection to the communicating computer systems is to be sixty four bits extensive. Sketch a probable architecture the usage of chips for each interface. The caricature have to imply the major components within every chip and which present day technology is suitable for every chip. [10 marks] How many gates and pins do you estimate every chip will contain? Justify your answer on the idea of the design requirements. [10 marks] 1 [TURN OVER CST.Ninety seven.7.2 three Comparative Architectures You are a pc architect operating at the layout of your organization's new instruction set structure for the twenty first Century. Analysis of the latest implementation of the present day structure suggests that removal of common sense to perform eight- and 16-bit masses and shops should bring about a 20% reduction in processor cycle time. You were assigned to assess the overall overall performance implications of disposing of sub-word memory accesses from the present day architecture so one can determine whether or not they'll be not noted from the brand new architecture. First, you want to take into account what series of instructions may be required to emulate sub-phrase masses and shops in software program the use of preferred commands. Show the instruction sequences so as to be required to load and store a signed byte cost given an arbitrary byte deal with stored in a register. Be positive to state any assumptions you make. [10 marks] Here is a precis of some dynamic practise blend statistics that have been amassed from the agency's modern processor executing an crucial integer benchmark: Instruction Percentage Instruction Percentage load 20% upload 18% branch 16% compare thirteen% store 9% or 8% shift 7% different 9% Of the loads and stores, ninety four% are 32-bit, 0% are 16-bit, and 6% are eight-bit. Assuming that your guidance sequences are used to replace all the eight-bit memory accesses, estimate the overall overall performance of the brand new implementation relative to the only with hardware assist for such accesses. [4 marks] In exercise, shorter practise sequences can be used to update most sub-phrase accesses on processors with out such hardware support. What greater coaching set features or compiler optimisations might be used to lessen the overhead of sub-phrase reminiscence accesses? [6 marks] 2 CST.Ninety seven.7.3 four ECAD Topics Describe the major facts structures and algorithms used inside the creation of an event-primarily based virtual logic simulator. [10 marks] Illustrate your answer with an outline of how the simulator might version an RS turn-flop crafted from pass-coupled NOR-gates with the subsequent inputs: Time 10 R & S both zero 15 R will become one 20 S becomes one 25 R will become zero 30 S will become zero The put off of the Q gate should be 6 devices and that of the Q gate 3. [10 marks] five Denotational Semantics Suppose that for each area D we want to have a characteristic YD : (D ? D) ? D (in which as common, D ? D denotes the area of continuous capabilities from D to itself). Consider the following two properties: (a) For all non-stop capabilities f : D ? D, YD(f) = f(YD(f)). (b) For all domain names E and for all non-stop features f : D ? D, g : E ? E and h : D ? E, with h strict, if h ? f = g ? h then YE(g) = h(YD(f)). Prove that there's one of these family of functions YD pleasing (a) and (b). Any information that you use about the life of fixed points need to be proved. [10 marks] Let ? = n > 0 ? d? be the domain such as a countably limitless chain collectively with its least higher certain: for that reason the non-trivial times of the partial order relation on ? are d0 v d1 v d2 v v d?. Let s : ? ? ? be the non-stop function that sends each dn to dn+1 and sends d? to itself. For every non-stop feature g : E ? E on a domain E, show that there is a strict continuous function h : ? ? E pleasurable h ? s = g ? h. Hence, or otherwise, deduce that there is best one family of features YD enjoyable homes (a) and (b). [10 marks] three [TURN OVER CST.Ninety seven.7.Four 6 Artificial Intelligence What kinds of know-how could an automatic journey agent want to represent? [5 marks] Using the automatic journey agent for example, define five problems connected with expertise illustration. [10 marks] Would an expert gadget be a suitable approach for imposing an automatic tour agent? [5 marks] 7 Neural Computing Illustrate how stochasticity can be used in synthetic neural networks to solve, at least in an asymptotic experience, troubles that could otherwise be intractable. Name at least such stochastic engines, describe the r?ole of stochasticity in each, and identify the kinds of problems that such artificial neural gadgets appear capable of solve.
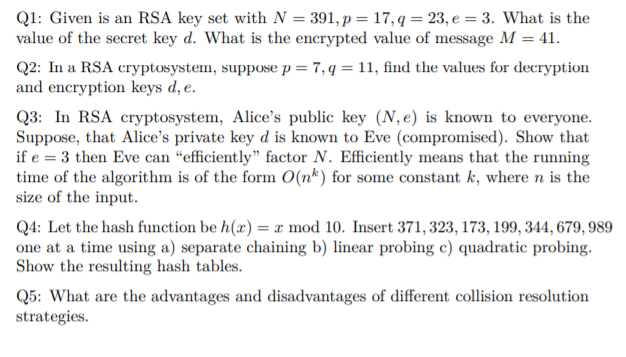

Q1: Given is an RSA key set with N = 391, p = 17, q = 23, e = 3. What is the value of the secret key d. What is the encrypted value of message M = 41. Q2: In a RSA cryptosystem, suppose p = 7, q = 11, find the values for decryption and encryption keys d, e. Q3: In RSA cryptosystem, Alice's public key (N, e) is known to everyone. Suppose, that Alice's private key d is known to Eve (compromised). Show that if e 3 then Eve can "efficiently" factor N. Efficiently means that the running time of the algorithm is of the form O(n) for some constant k, where n is the size of the input. Q4: Let the hash function be h(x) = x mod 10. Insert 371, 323, 173, 199, 344, 679, 989 one at a time using a) separate chaining b) linear probing c) quadratic probing. Show the resulting hash tables. Q5: What are the advantages and disadvantages of different collision resolution strategies.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


