DQ1. What is an Audit Work Program (some call it Audit Program)? The audit work program - Email Surveillance Audit Program What is the structure
DQ1. What is an Audit Work Program (some call it Audit Program)? The audit work program - Email Surveillance Audit Program What is the structure and contents including various audit steps. Find 1-2 steps in the audit program where the audit software can be used. How can audit software be used to gather evidence?. (the Audit program (Email Surveillance Audit Program details is attached).
DQ3. Review the contents of the Audit Manual of Office of University Audits at University of Illinois, UrbanaChampaign. With another internal audit department manual of any other organization, compare its contents at a high (topic) level and identify similarities and differences between the two manuals. Provide the link please.
DQ4. What are some of the difficulties internal auditors face in conducting an audit engagement? What is an appropriate article to support your answer.
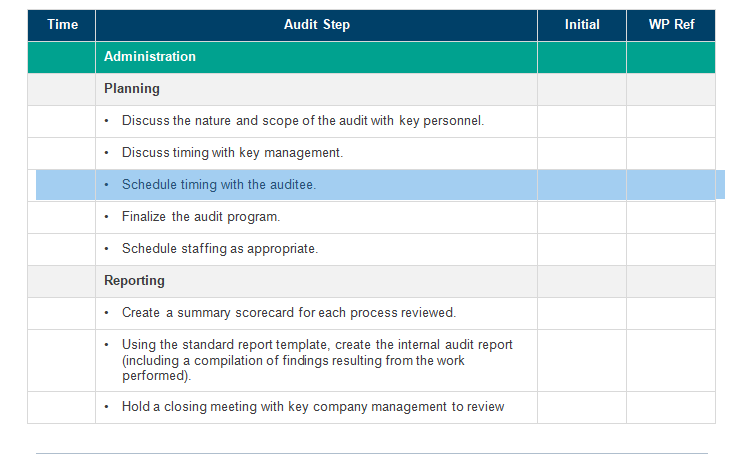
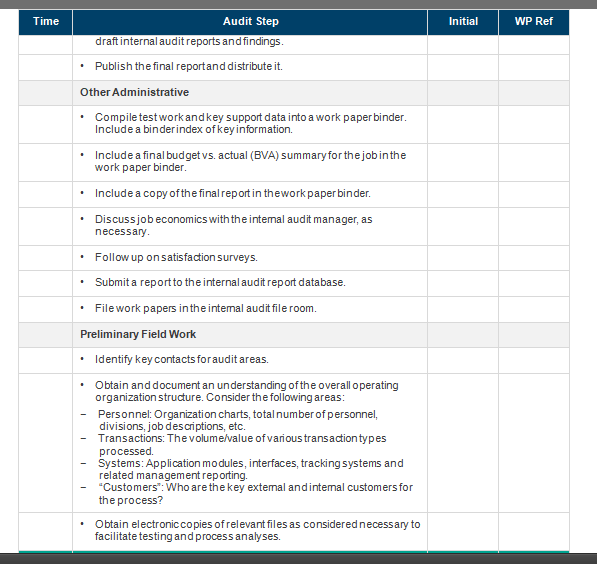
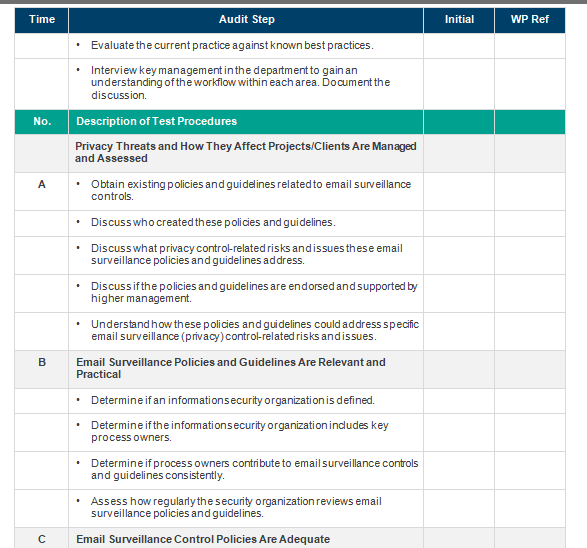
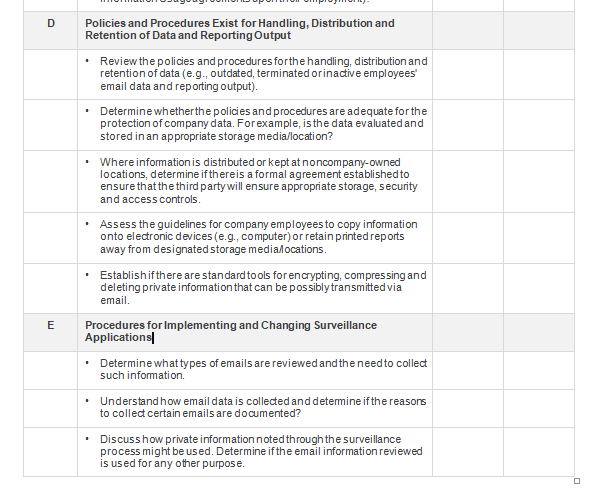
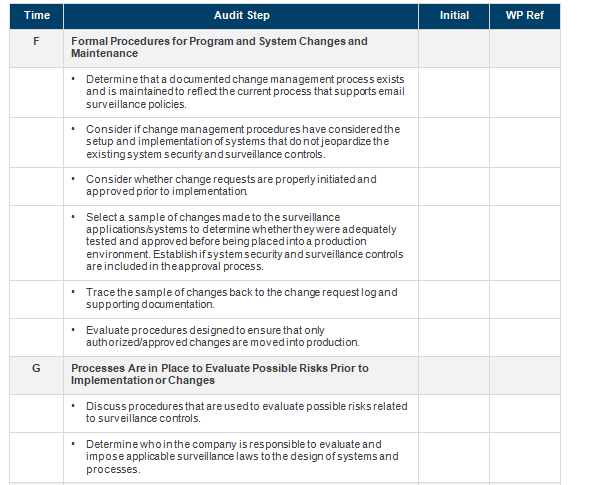
Time Audit Step Initial WP Ref Administration Planning Discuss the nature and scope of the audit with key personnel. Discuss timing with key management. Schedule timing with the auditee. Finalize the audit program. Schedule staffing as appropriate. Reporting Create a summary scorecard for each process reviewed. Using the standard report template, create the internal audit report (including a compilation of findings resulting from the work performed). Hold a closing meeting with key company management to review Time Audit Step Initial WP Ref draft internal audit reports and findings. Publish the final report and distribute it. Other Administrative Compile test work and key support data into a work paper binder. Include a binderindex of keyinformation. . Include a final budget vs. actual (BVA) summary for the job in the work paper binder. . Include a copy of the final report in thework paper binder. Discussjob economics with the internal audit manager, as necessary. Follow up on satisfaction surveys. Submit a report to the internal audit report database. File work papers in the internal audit file room. Preliminary Field Work Identify key contacts for audit areas. Obtain and document an understanding of the overall operating organization structure. Consider the following areas: - Personnel: Organization charts, total number of personnel, divisions, job descriptions, etc. - Transactions: The volume/value of various transaction types processed. - Systems: Application modules, interfaces, tracking systems and related management reporting. - CustomersWho are the key external and internal customers for the process? Obtain electronic copies of relevant files as considered necessary to facilitate testing and process analyses. Time Audit Step Initial WP Ref Evaluate the current practice against known best practices. Interview key management in the department to gain an understanding of the workflow within each area. Document the discussion. No. Description of Test Procedures Privacy Threats and How They Affect Projects/Clients Are Managed and Assessed Obtain existing policies and guidelines related to email surveillance controls. Discuss who created these policies and guidelines Discuss what privacy control-related risks and issues these email surveillance policies and guidelines address. Discuss if the policies and guidelines are endorsed and supported by higher management. Understand how these policies and guidelines could address specific email surveillance (privacy) control-related risks and issues. B Email Surveillance Policies and Guidelines Are Relevant and Practical Determine if an informations ecurity organization is defined. Determine if the informations ecurity organization includes key process owners. Determine if process owners contribute to email surveillance controls and guidelines consistently. Assess how regularly the security organization reviews email surveillance policies and guidelines. C Email Surveillance Control Policies Are Adequate D Policies and Procedures Exist for Handling, Distribution and Retention of Data and Reporting Output Review the policies and procedures forthe handling, distribution and retention of data (e.g., outdated, terminated orinactive employees email data and reporting output) Determine whetherthe policies and procedures are adequate for the protection of company data. For example, is the data evaluated and stored in an appropriate storage media/location? Where information is distributed or kept at noncompany-owned locations, determine if thereis a formal agreement established to ensure that the third party will ensure appropriate storage, security and access controls. Assess the guidelines for company employees to copy information onto electronic devices (e.g., computer) or retain printed reports away from designated storage medialocations. Establish if there are standard tools for encrypting, compressing and deleting private information that can be possibly transmitted via email E Proc Procedures for implementing and Changing Surveillance Applications! Determine what types of emails are reviewed and the need to collect such information Understand how email data is collected and determine if the reasons to collect certain emails are documented? Discuss how private information noted through the surveillance process might be used. Determine if the email information reviewed is used for any other purpose. Time Audit Step Initial WP Ref Formal Procedures for Program and System Changes and Maintenance Determine that a documented change management process exists and is maintained to reflect the current process that supports email surveillance policies. Consider if change management procedures have considered the setup and implementation of systems that do not jeopardize the existing system security and surveillance controls. Consider whether change requests are properly initiated and approved prior to implementation Select a sample of changes made to the surveillance applications/systems to determine whether they were adequately tested and approved before being placedinto a production environment. Establish if system security and surveillance controls are included in the approval process. Trace the sample of changes back to the change request log and supporting documentation. Evaluate procedures designed to ensure that only authorized approved changes are moved into production Processes Are in Place to Evaluate Possible Risks Prior to Implementation or Changes Discuss procedures that are used to evaluate possible risks related to surveillance controls. Determine whoin the company is responsible to evaluate and impose applicable surveillance laws to the design of systems and processes
Step by Step Solution
There are 3 Steps involved in it
Step: 1

See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


