Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Ex. 2 A C Program to implement Caesars Cipher. Part 1,2,3,4,5 are the hardest parts for me but I would be very grateful if you

 Ex. 2 A C Program to implement Caesars Cipher.
Ex. 2 A C Program to implement Caesars Cipher.
Part 1,2,3,4,5 are the hardest parts for me but I would be very grateful if you can do all 7 parts.Thank you.
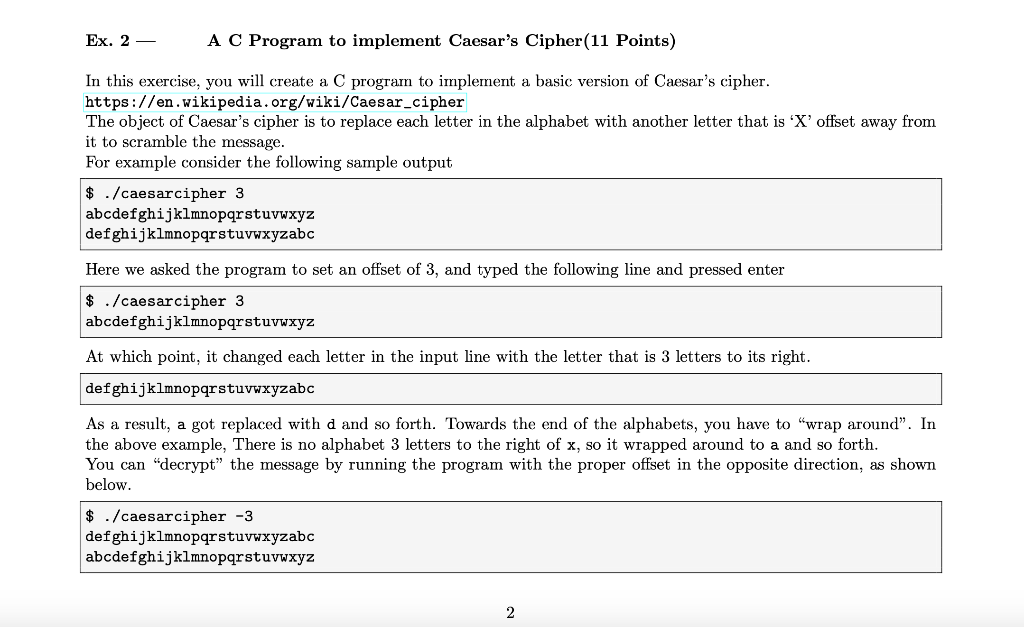
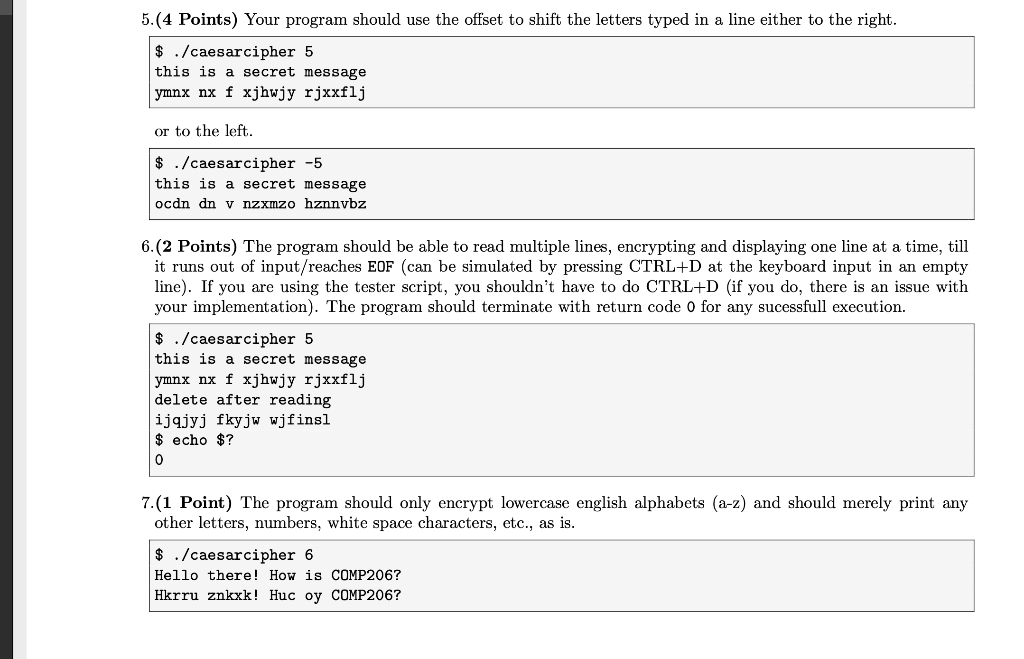
Ex. 2 AC Program to implement Caesar's Cipher(11 Points) In this exercise, you will create a C program to implement a basic version of Caesar's cipher. https://en.wikipedia.org/wiki/Caesar_cipher The object of Caesar's cipher is to replace each letter in the alphabet with another letter that is 'X' offset away from it to scramble the message. For example consider the following sample output $ ./caesarcipher 3 abcdefghijklmnopqrstuvwxyz defghijklmnopqrstuvwxyzabc Here we asked the program to set an offset of 3, and typed the following line and pressed enter $ ./ caesarcipher 3 abcdefghijklmnopqrstuvwxyz At which point, it changed each letter in the input line with the letter that is 3 letters to its right. defghijklmnopqrstuvwxyzabc As a result, a got replaced with d and so forth. Towards the end of the alphabets, you have to "wrap around". In the above example, There is no alphabet 3 letters to the right of x, so it wrapped around to a and so forth. You can "decrypt" the message by running the program with the proper offset in the opposite direction, as shown below. $ ./caesarcipher -3 defghijklmnopqrstuvwxyzabc abcdefghijklmnopqrstuvwxyz Here, we started with program with an offset -3 which asked the program to shift the letters to the left and the entered the original encrypted line. $ ./caesarcipher -3 defghijklmnopqrstuvwxyzabc To which it responded with the decrypted message. abcdefghijklmnopqrstuvwxyz 1. Use vi to create a C program source file caesarcipher.c 2.(1 Point) The program should include a comment section at the beginning that describes its purpose (couple of lines), the author your name), your department, a small "history" section indicating what changes you did on what date. The code should be properly indented for readability as well as contain any additional comments required to understand the program logic. 3.(1 Point) The source code should be compilable by (exactly) using the command gcc -o caesarcipher caesarcipher.c. 4.(2 Points) Your program should accept an integer argument as its option for the user to indicate the offset. If the user does not pass this argument, you should display an error message and terminate with error code 1. $ ./caesarcipher Error: usage is caesarcipherStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


