Answered step by step
Verified Expert Solution
Question
1 Approved Answer
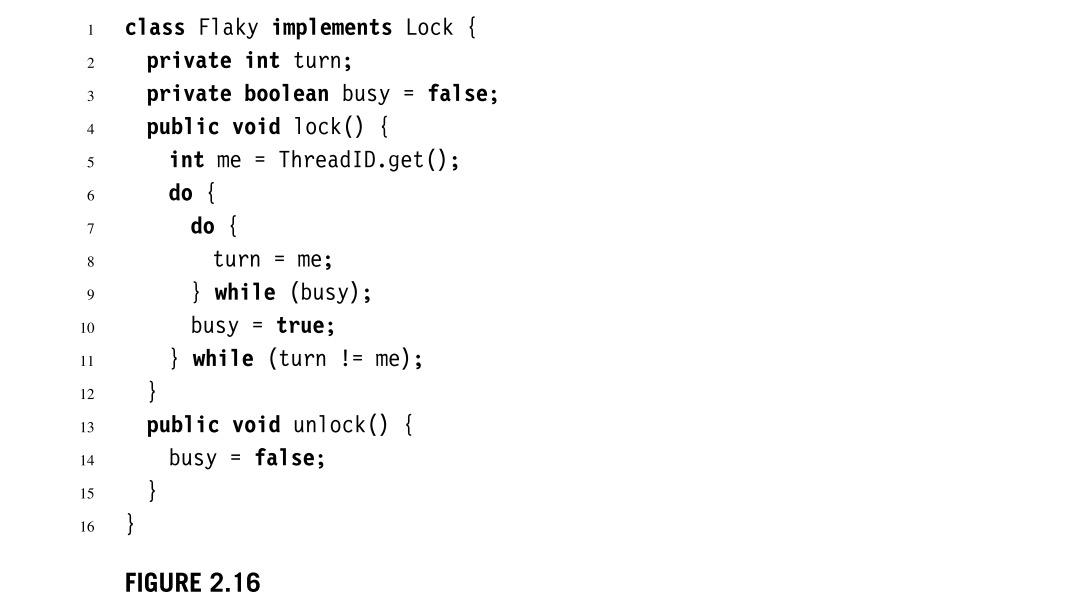
Exercise 2 . 3 . Programmers at the Flaky Computer Corporation designed the protocol shown in Fig. 2 . 1 6 to achieve n -
Exercise Programmers at the Flaky Computer Corporation designed the protocol shown in Fig. to achieve thread mutual exclusion. For each question, either sketch a proof, or display an execution where it fails.
Does this protocol satisfy mutual exclusion?
Is this protocol starvationfree?
Is this protocol deadlockfree?
Is this protocol livelockfree?
class Flaky implements Lock
private int turn;
private boolean busy false;
public void lock
int me ThreadID.get ;
do
do
turn me;
while busy;
busy true;
while turn me;
public void unlock
busy false;
FIGURE
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


