Exponential fun
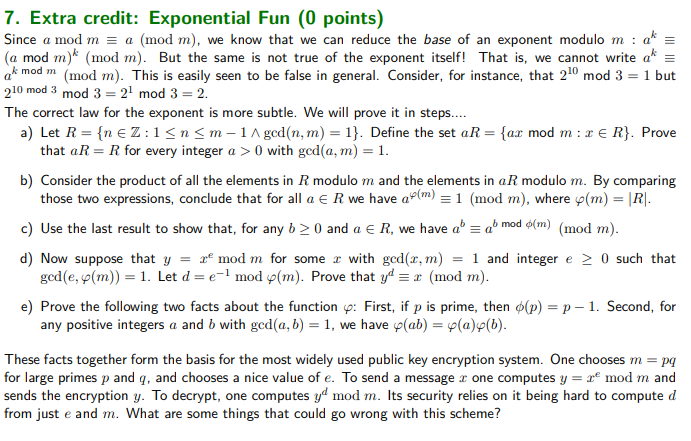
7. Extra credit: Exponential Fun (0 points) Since a mod m = a (mod m), we know that we can reduce the base of an exponent modulo m : ak = (a mod m (mod m). But the same is not true of the exponent itself! That is, we cannot write a = ak mod m (mod m). This is easily seen to be false in general. Consider, for instance, that 210 mod 3 = 1 but 210 mod 3 mod 3= 21 mod 3 = 2. The correct law for the exponent is more subtle. We will prove it in steps.... a) Let R = {n EZ:1
0 with ged(a,m) = 1. b) Consider the product of all the elements in R modulo m and the elements in aR modulo m. By comparing those two expressions, conclude that for all a R we have a'lm) = 1 (mod m), where y(m) = R. c) Use the last result to show that, for any b>0 and a R, we have a = amodom) (mod m). d) Now suppose that y = r mod m for some = with ged(2,m) = 1 and integer e > 0 such that ged(e,v(m)) = 1. Let d=e-1 mod p(m). Prove that yd = x (mod m). (p) = p - 1. Second, for e) Prove the following two facts about the function 4: First, if p is prime, then any positive integers a and b with ged(a,b) = 1, we have y(ab) = f(a) (b). These facts together form the basis for the most widely used public key encryption system. One chooses m = pq for large primes p and q, and chooses a nice value of e. To send a message one computes y = r mod m and sends the encryption y. To decrypt, one computes y mod m. Its security relies on it being hard to computed from just e and m. What are some things that could go wrong with this scheme? 7. Extra credit: Exponential Fun (0 points) Since a mod m = a (mod m), we know that we can reduce the base of an exponent modulo m : ak = (a mod m (mod m). But the same is not true of the exponent itself! That is, we cannot write a = ak mod m (mod m). This is easily seen to be false in general. Consider, for instance, that 210 mod 3 = 1 but 210 mod 3 mod 3= 21 mod 3 = 2. The correct law for the exponent is more subtle. We will prove it in steps.... a) Let R = {n EZ:1 0 with ged(a,m) = 1. b) Consider the product of all the elements in R modulo m and the elements in aR modulo m. By comparing those two expressions, conclude that for all a R we have a'lm) = 1 (mod m), where y(m) = R. c) Use the last result to show that, for any b>0 and a R, we have a = amodom) (mod m). d) Now suppose that y = r mod m for some = with ged(2,m) = 1 and integer e > 0 such that ged(e,v(m)) = 1. Let d=e-1 mod p(m). Prove that yd = x (mod m). (p) = p - 1. Second, for e) Prove the following two facts about the function 4: First, if p is prime, then any positive integers a and b with ged(a,b) = 1, we have y(ab) = f(a) (b). These facts together form the basis for the most widely used public key encryption system. One chooses m = pq for large primes p and q, and chooses a nice value of e. To send a message one computes y = r mod m and sends the encryption y. To decrypt, one computes y mod m. Its security relies on it being hard to computed from just e and m. What are some things that could go wrong with this scheme<><>







