Question: Figure. 1 illustrates a simplification of the SSL/TLS session-security protocol; this simpli- fication uses a fixed master key k which is shared in advance between
Figure. 1 illustrates a simplification of the SSL/TLS session-security protocol; this simpli- fication uses a fixed master key k which is shared in advance between the two participants, Client and Server. This simplified version supports transmission of only two messages, a request MC send by the client to the server, and a response MS sent from server. The two messages are protected using a session key k 0 , which the server selects randomly at the beginning of each session, and sends to the client, protected using the fixed shared master key k.
The protocol should protect the confidentiality and integrity (authenticity) of the messages (MC , MS), as well as replay of messages, e.g., client sends MC in one session and server receives MC on two sessions.
1. The field cipher suite contains a list of encryption schemes (ciphers) supported by the client, and the field chosen cipher contains the cipher in this list chosen by the server; this cipher is used in the two subsequent messages (a fixed cipher is used for the first two messages). For simplicity, consider only two ciphers, say E1 and E2, and suppose that both client ans server support both, but that they prefer E2 since E1 is known to be vulnerable. Show how a MitM attacker can cause the parties to use E1 anyway, allowing it to decipher the message MC , MS.
2. Suggest a minor modification to the protocol to prevent such downgrade attacks
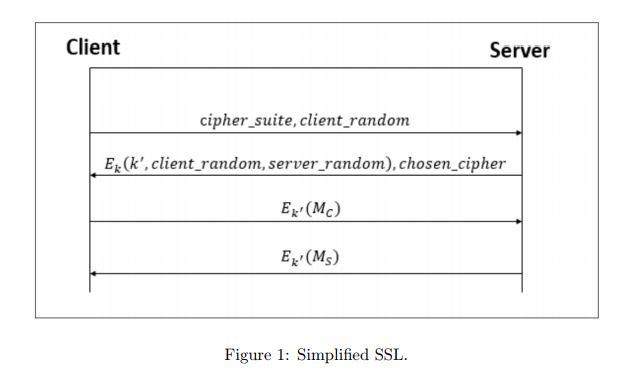
Client Server civher suite.client random E (k',client_random, server random), chosen cipher E (Mc) E (Ms) Figure 1: Simplified SSL
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


