Answered step by step
Verified Expert Solution
Question
1 Approved Answer
For the EIGamal cryptosystem, let the public key of Alice be (p, g, h), wherep is a big prime, and g is a generator
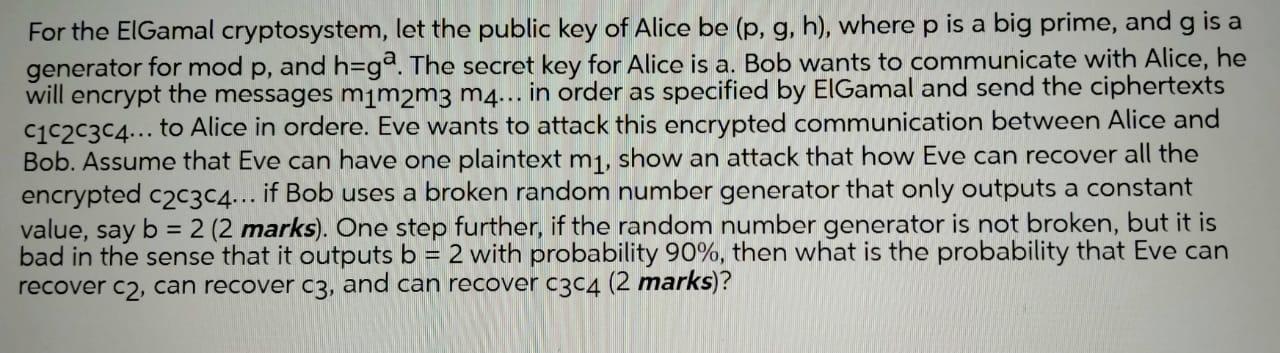
For the EIGamal cryptosystem, let the public key of Alice be (p, g, h), wherep is a big prime, and g is a generator for mod p, and h3g. The secret key for Alice is a. Bob wants to communicate with Alice, he will encrypt the messages mim2m3 m4... in order as specified by EIGamal and send the ciphertexts C1C2C3C4... to Alice in ordere. Eve wants to attack this encrypted communication between Alice and Bob. Assume that Eve can have one plaintext m1, show an attack that how Eve can recover all the encrypted c2c3c4... if Bob uses a broken random number generator that only outputs a constant value, say b = 2 (2 marks). One step further, if the random number generator is not broken, but it is bad in the sense that it outputs b = 2 with probability 90%, then what is the probability that Eve can recover c2, can recover c3, and can recover c3C4 (2 marks)? %3D
Step by Step Solution
★★★★★
3.50 Rating (167 Votes )
There are 3 Steps involved in it
Step: 1
AElGamal Encryption Algorithm ElGamal encryption is an publickey cryptosystem It uses asymmetric key encryption for communicating between two parties ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


