Answered step by step
Verified Expert Solution
Question
1 Approved Answer
For the following Threat Categories, 1) Explain the threat, 2)which type of Control should be put in place for mitigation, 3)classify the controls as Process
For the following Threat Categories, 1) Explain the threat, 2)which type of Control should be put in place for mitigation, 3)classify the controls as Process (Administrative), Product or Physical, 4)State the type of controls whether it will Prevent, Detect, Correct or Compensate.
Threat Categories:
1. Mobile Malware 2. Ransomware attacks 3. Impersonation attacks 4. Phishing attacks assisted with deep fake 5. Cloud Jacking 6. Insider threats 7. IoT-Based Attacks 8. Uneven Cybersecurity Protections 9. Smishing attacks 10. DNS tunelling
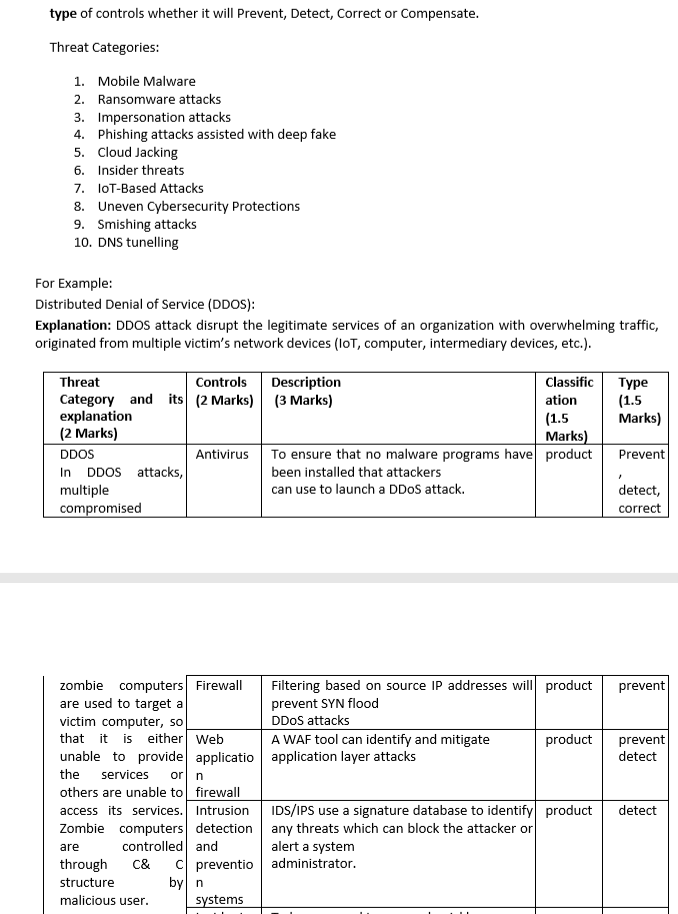
type of controls whether it will Prevent, Detect, Correct or Compensate. Threat Categories: 1. Mobile Malware 2. Ransomware attacks 3. Impersonation attacks 4. Phishing attacks assisted with deep fake 5. Cloud Jacking 6. Insider threats 7. IoT-Based Attacks 8. Uneven Cybersecurity Protections 9. Smishing attacks 10. DNS tunelling For Example: Distributed Denial of Service (DDOS): Explanation: DDOS attack disrupt the legitimate services of an organization with overwhelming traffic, originated from multiple victim's network devices (loT, computer, intermediary devices, etc.). Threat Controls Category and its (2 Marks) explanation (2 Marks) DDOS In DDOS attacks, multiple compromised Antivirus zombie computers Firewall are used to target a victim computer, so that it is either Web unable to provide applicatio the services or n others are unable to firewall access its services. Intrusion Zombie computers detection are controlled and through C& C preventio structure by n malicious user. systems Description (3 Marks) Classific ation (1.5 Marks) To ensure that no malware programs have product been installed that attackers can use to launch a DDoS attack. Filtering based on source IP addresses will product prevent SYN flood DDoS attacks A WAF tool can identify and mitigate application layer attacks product IDS/IPS use a signature database to identify product any threats which can block the attacker or alert a system administrator. Type (1.5 Marks) Prevent detect, correct prevent prevent detect detect
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


