For this assignment you are required to produce a three-to-five page paper that highlights ethics, regulations and security controls.
On Friday morning, as the Dean of Technology Services, you are called into a meeting to discuss a data security breach involving a list of financial aid students. The Provost, the Dean of Alumni Services and Dean of Financial Aid are also present at the meeting. The data breach concerns a list that contains students full name, social security number, and financial aid eligibility. The following events occurred:
- A staff member in the Alumni Services Office emails the Director of Financial Aid and requests two work-study students. He unknowingly attaches an e-mail distribution list that contains all alumni e-mail IDs.
- The Director of Financial Aid attaches a file, selects Reply All, and sends the e-mail back to the staff member. The file contains a list of 57 students who are eligible for work-study financial aid. This file contains students full name, social security number, and the amount of financial aid.
- The staff member notices that the reply was sent to all alumni. However, he did not see any problems, and went home without notifying anyone.
- Some alumni saw the e-mail, and deleted the e-mail without reading it.
- Some read the e-mail and opened the attachment.
- Several alumni e-mailed college administration during the night to find out why they were on the distribution list.
- One alumnus who works for the Department of Educations Family Policy Compliance Office opened the email and immediately forwarded the email to the Provost, the Dean of Alumni Services, and Dean of Financial Aid. The alumnus is upset that students privacy and confidentiality were compromised and further stated this is in violation of (the regulatory mandate was intentionally omitted here).
After reviewing the scenario, produce a paper that answers both of the following questions:
- Identify and briefly explain the regulatory mandate the scenario is violating. Justify your response by identifying the events (i.e., the number of the event) that are in clear violation of the mandate.
- According to Turban et al. (p. 132), what are some security controls that the organization can implement to avoid a similar incident in the future? Discuss three controls that are most important in your opinion.
Begin your paper with an Introduction that sets the context for your work.
Wrap up the paper with a final paragraph that concludes with your thoughts on the challenges to implementing enterprise systems based on research that you have conducted.
 p.132 attached. Help
p.132 attached. Help
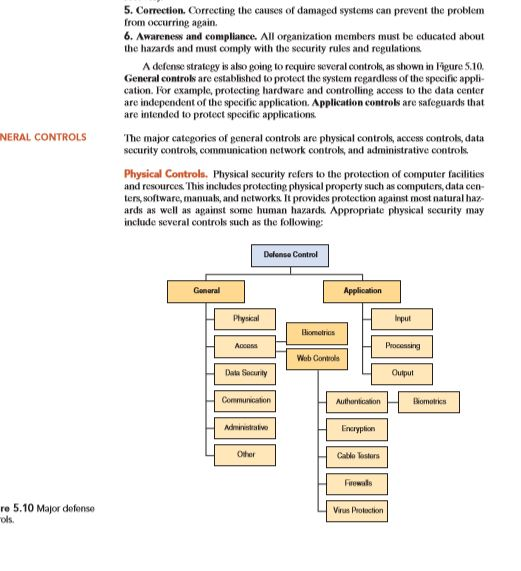
5.4 Information Assurance and Risk Management The objective of IT security management practices is to defend all of the components of an information system, specifically data, software applications, hardware, and net- works. Before they make any decisions concerning defenses, people responsible for security must understand the requirements and operations of the business, which form the basis for a customized defense strategy. In the next section, we describe the major defense strategies. DEFENSE STRATEGY The defense strategy and controls that should be used depend on what needs to be protected and the cost-benefit analysis. That is, companies should neither under-invest nor over-invest. The SEC and FTC impose huge fines for data breaches to deter companies from under-investing in data protection. The following are the major objectives of defense strategies: 1. Prevention and deterrence. Properly designed controls may prevent errors from occurring, deter criminals from attacking the system, and, better yet, deny access to unauthorized people. These are the most desirable controls. 132 Chapter 5 Cyber Security, Compliance, and Business Continuity 2. Detection. Like a fire, the earlier an attack is detected, the easier it is to combat, and the less damage is done. Detection can be performed in many cases by using spe- cial diagnostic software, at a minimal cost. 3. Contain the damage. This objective is to minimize or limit losses once a malfunc- tion has occurred. This process is also called damage control. This can be accom- plished, for example, by including a fault-tolerant system that permits operation in a degraded mode until full recovery is made. If a fault-tolerant system does not exist, a quick and possibly expensive recovery must take place. Users want their systems back in operation as fast as possible. 4. Recovery. A recovery plan explains how to fix a damaged information system as quickly as possible. Replacing rather than repairing components is one route to fast recovery. 5. Correction. Correcting the causes of damaged systems can prevent the problem from occurring again. 6. Awareness and compliance. All organization members must be educated about the hazards and must comply with the security rules and regulations A defense strategy is also going to require several controls, as shown in Figure 5.10 General controls are established to protect the system repardless of the specific appli cation. For example, protecting hardware and controlling access to the data center are independent of the specific application. Application controls are safeguards that are intended to protect specific applications NERAL CONTROLS The major categories of general controls are physical controls, access controls, data security controls, communication network controls, and administrative controls Physical Controls. Physical security refers to the protection of computer facilities and resources. This includes protecting physical property such as computers, data cen ters, software, manuals, and networks. It provides protection against most natural ha ards as well as against some human hazards. Appropriate pluysical security may include several controls such as the following: Dalense Control General Application Physical Input Homes Processing Web Controls Data Security Output Communication Authention Bomoties Encryption Other ro 5.10 Major defense Virus Protection 5.4 Information Assurance and Risk Management The objective of IT security management practices is to defend all of the components of an information system, specifically data, software applications, hardware, and net- works. Before they make any decisions concerning defenses, people responsible for security must understand the requirements and operations of the business, which form the basis for a customized defense strategy. In the next section, we describe the major defense strategies. DEFENSE STRATEGY The defense strategy and controls that should be used depend on what needs to be protected and the cost-benefit analysis. That is, companies should neither under-invest nor over-invest. The SEC and FTC impose huge fines for data breaches to deter companies from under-investing in data protection. The following are the major objectives of defense strategies: 1. Prevention and deterrence. Properly designed controls may prevent errors from occurring, deter criminals from attacking the system, and, better yet, deny access to unauthorized people. These are the most desirable controls. 132 Chapter 5 Cyber Security, Compliance, and Business Continuity 2. Detection. Like a fire, the earlier an attack is detected, the easier it is to combat, and the less damage is done. Detection can be performed in many cases by using spe- cial diagnostic software, at a minimal cost. 3. Contain the damage. This objective is to minimize or limit losses once a malfunc- tion has occurred. This process is also called damage control. This can be accom- plished, for example, by including a fault-tolerant system that permits operation in a degraded mode until full recovery is made. If a fault-tolerant system does not exist, a quick and possibly expensive recovery must take place. Users want their systems back in operation as fast as possible. 4. Recovery. A recovery plan explains how to fix a damaged information system as quickly as possible. Replacing rather than repairing components is one route to fast recovery. 5. Correction. Correcting the causes of damaged systems can prevent the problem from occurring again. 6. Awareness and compliance. All organization members must be educated about the hazards and must comply with the security rules and regulations A defense strategy is also going to require several controls, as shown in Figure 5.10 General controls are established to protect the system repardless of the specific appli cation. For example, protecting hardware and controlling access to the data center are independent of the specific application. Application controls are safeguards that are intended to protect specific applications NERAL CONTROLS The major categories of general controls are physical controls, access controls, data security controls, communication network controls, and administrative controls Physical Controls. Physical security refers to the protection of computer facilities and resources. This includes protecting physical property such as computers, data cen ters, software, manuals, and networks. It provides protection against most natural ha ards as well as against some human hazards. Appropriate pluysical security may include several controls such as the following: Dalense Control General Application Physical Input Homes Processing Web Controls Data Security Output Communication Authention Bomoties Encryption Other ro 5.10 Major defense Virus Protection

 p.132 attached. Help
p.132 attached. Help





