Question: Hardware such as disks, display screens and memory have to be separated and used in the way they were intended. This is an example
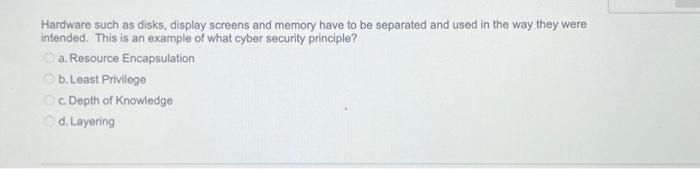
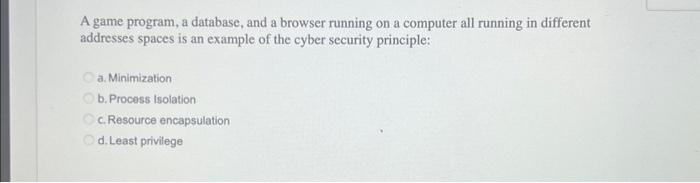
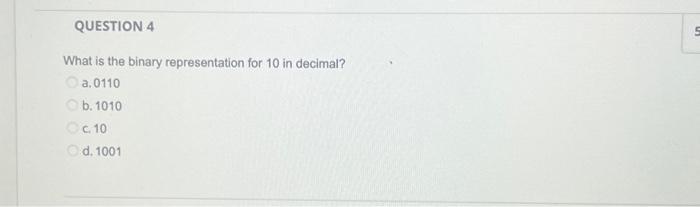
Hardware such as disks, display screens and memory have to be separated and used in the way they were intended. This is an example of what cyber security principle? a. Resource Encapsulation b. Least Privilege Oc. Depth of Knowledge d. Layering A game program, a database, and a browser running on a computer all running in different addresses spaces is an example of the cyber security principle: O a. Minimization b. Process Isolation c. Resource encapsulation d. Least privilege QUESTION 4 What is the binary representation for 10 in decimal? a.0110 b. 1010 c. 10 Od. 1001 5
Step by Step Solution
3.37 Rating (150 Votes )
There are 3 Steps involved in it
1 a Resource Encapsulation Explanation Resource encapsulation is a cyber security principle that inv... View full answer

Get step-by-step solutions from verified subject matter experts


