Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Hello I do need help with this Python3 programming, as well as the reflective questions. Thanks a lot. Background In this assignment you will be
Hello 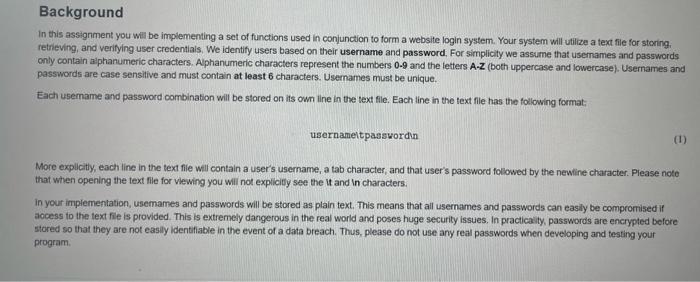
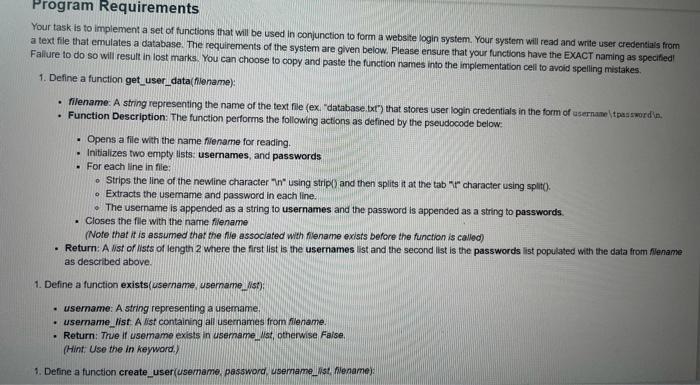
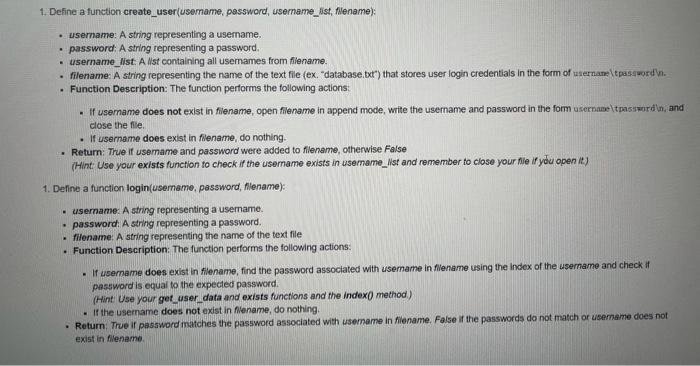
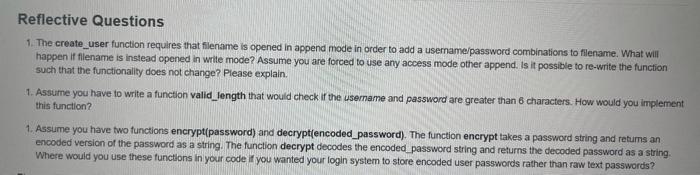
Background In this assignment you will be implementing a set of functions used in conjunction to form a website login system. Your system will utilize a text file for storing, retrieving, and verifying user credentials. We identify users based on their username and password. For simplicity we assume that usernames and passwords only contain alphanumeric characters. Alphanumeric characters represent the numbers 0-9 and the letters A-Z (both uppercase and lowercase). Usernames and passwords are case sensitive and must contain at least 6 characters. Usernames must be unique. Each username and password combination will be stored on its own Ine in the text file. Each line in the text file has the following format: username tpasswordin (1) More explicitly, each line in the text file will contain a user's username a tab character, and that user's password followed by the newline character. Please note that when opening the text file for viewing you will not explicitly see the it and in characters. in your implementation, usemames and passwords will be stored as plain text. This means that all usernames and passwords can easily be compromised if access to the text file is provided. This is extremely dangerous in the real world and poses huge security issues. In practicality, passwords are encrypted before stored so that they are not easily identifiable in the event of a data breach. Thus, please do not use any real passwords when developing and testing your program Program Requirements Your task is to implement a set of functions that will be used in conjunction to form a website login system. Your system will read and write user credentials from a text file that emulates a database. The requirements of the system are given below. Please ensure that your functions have the EXACT naming as specified! Fallure to do so will result in lost marks. You can choose to copy and paste the function names into the implementation cell to avoid spelling mistakes. 1. Define a function get_user_data(filename): filename. A string representing the name of the text file (ex "database txt") that stores user login credentials in the form of username tpasswordin. Function Description: The function performs the following actions as defined by the pseudocode below: Opens a file with the name filename for reading . Initializes two empty lists: usernames, and passwords . For each line in nie: Strips the line of the newline character using stript) and then splits it at the tab " character using split). Extracts the username and password in each line. The username is appended as a string to usernames and the password is appended as a string to passwords. Closes the file with the name filename (Note that it is assumed that the file associated with filename exists before the function is called) Return: As of lists of length 2 where the first list is the usernames list and the second list is the passwords list populated with the data from Alename as described above. 1. Define a function exists( username username st): . usemame: A string representing a usemame. username_list A list containing all usernames from Allename. Return: True if usemame exists in username.Mst, otherwise False (Hint: Use the in keyword.) 1. Define a function create_user(username, password usemame_list filename) . 1. Define a function create_user username, password, username_est, filename): Username: A string representing a username. password: A string representing a password . username_list: A list containing all usernames from filename. filename: A string representing the name of the text file (ex. "database.txt") that stores user login credentials in the form of username tpassword in. Function Description: The function performs the following actions If username does not exist in filename, open filename in append mode, write the username and password in the form username password in, and close the file. . If username does exist in filename, do nothing Return: True if username and password were added to filename, otherwise False (Hint: Use your exists function to check if the username exists in username_Mst and remember to close your fleir you open it) 1. Define a function login(username, password, filename) . username: A string representing a usemame. password: A string representing a password. filename: A string representing the name of the text file Function Description: The function performs the following actions: - If username does exist in filename, find the password associated with username in filename using the Index of the username and check it password is equal to the expected password (Hint: Use your get user data and exists functions and the Index() method) . If the username does not exist in nename, do nothing Return: True if password matches the password associated with username in lename. False if the passwords do not match or username does not exist in filename Reflective Questions 1. The create_user function requires that filename is opened in append mode in order to add a username/password combinations to filename. What will happen if filename is instead opened in write mode? Assume you are forced to use any access mode other append. Is it possible to re-write the function such that the functionality does not change? Please explain. 1. Assume you have to write a function valid_length that would check if the username and password are greater than 6 characters. How would you implement this function? 1. Assume you have two functions encrypt(password) and decrypt(encoded_password). The function encrypt takes a password string and returns an encoded version of the password as a string. The function decrypt decodes the encoded_password string and returns the decoded password as a string Where would you use these functions in your code if you wanted your login system to store encoded user passwords rather than raw text passwords I do need help with this Python3 programming, as well as the reflective questions. Thanks a lot.




Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


