Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Here we are investigating various ways of how we can use a CPA- secure scheme to build authenticated encryption. Assume Enck (m) : r||FK(r)
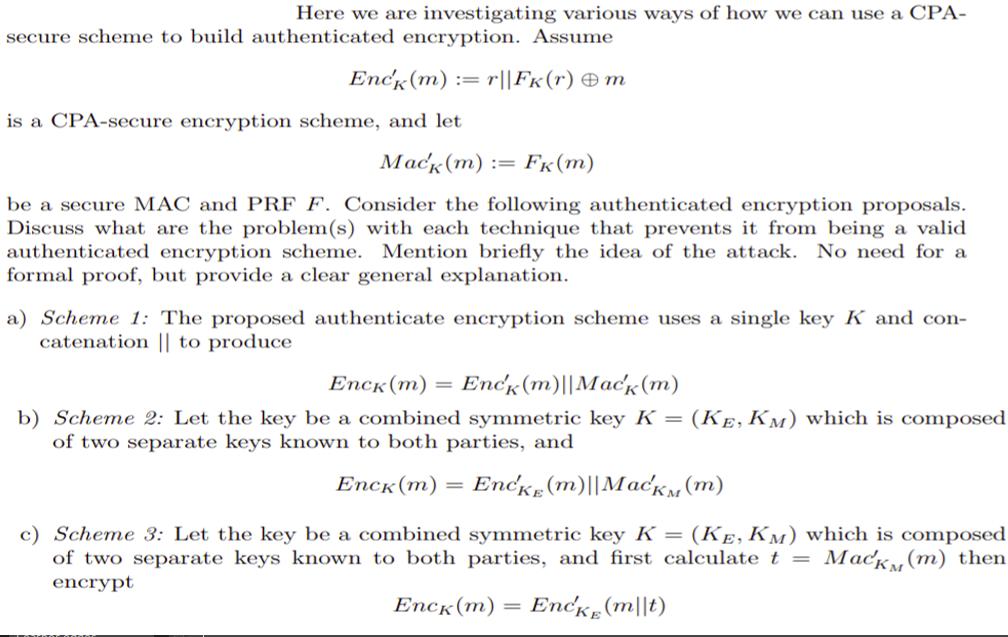
Here we are investigating various ways of how we can use a CPA- secure scheme to build authenticated encryption. Assume Enck (m) : r||FK(r) m is a CPA-secure encryption scheme, and let Mack (m) := Fk (m) be a secure MAC and PRF F. Consider the following authenticated encryption proposals. Discuss what are the problem(s) with each technique that prevents it from being a valid authenticated encryption scheme. Mention briefly the idea of the attack. No need for a formal proof, but provide a clear general explanation. a) Scheme 1: The proposed authenticate encryption scheme uses a single key K and con- catenation || to produce Enck (m) = Enck (m) | Mack (m) b) Scheme 2: Let the key be a combined symmetric key K = (KE, KM) which is composed of two separate keys known to both parties, and Enck (m) Encke (m)||MacKM (m) c) Scheme 3: Let the key be a combined symmetric key K = (KE, KM) which is composed of two separate keys known to both parties, and first calculate t = Mack (m) then encrypt Enck (m) Encke (mt)
Step by Step Solution
★★★★★
3.38 Rating (173 Votes )
There are 3 Steps involved in it
Step: 1
a Scheme 1 The problem with Scheme 1 is that the MAC Mack is computed over the entire ciphertext inc...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


