Question: How do most attacks begin? By massive data breaches with leaked information. By gathering information from a company's website. By utilizing third-party websites to
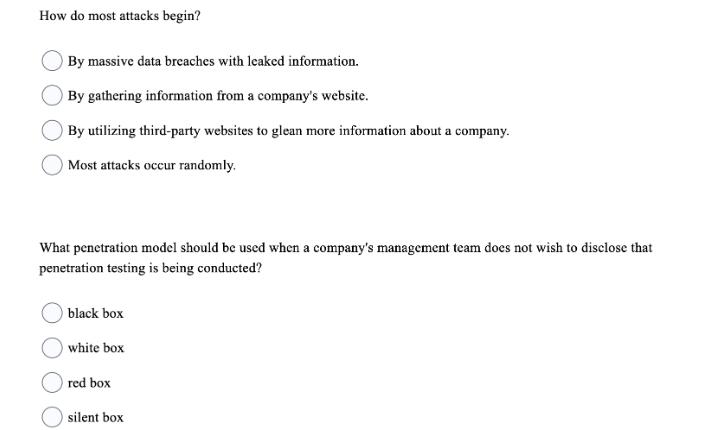
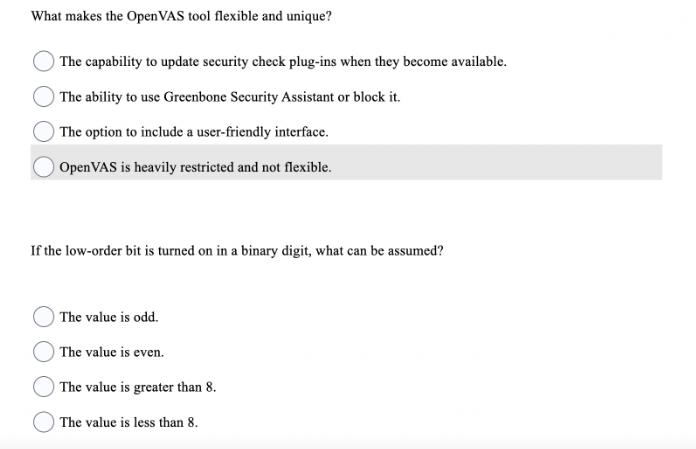
How do most attacks begin? By massive data breaches with leaked information. By gathering information from a company's website. By utilizing third-party websites to glean more information about a company. Most attacks occur randomly. What penetration model should be used when a company's management team does not wish to disclose that penetration testing is being conducted? black box white box red box silent box What makes the OpenVAS tool flexible and unique? The capability to update security check plug-ins when they become available. The ability to use Greenbone Security Assistant or block it. The option to include a user-friendly interface. Open VAS is heavily restricted and not flexible. If the low-order bit is turned on in a binary digit, what can be assumed? The value is odd. The value is even. The value is greater than 8. The value is less than 8.
Step by Step Solution
3.31 Rating (154 Votes )
There are 3 Steps involved in it
The detailed answer for the above question is provided below 1 How do most attacks begin Answer By g... View full answer

Get step-by-step solutions from verified subject matter experts


