Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I choose this topic: CWE-640: week password recovery mechanism for forgotten password Description: Knowing Security Weaknesses. This activity helps students to become more familiar with
I choose this topic:
CWE-640: week password recovery mechanism for forgotten password
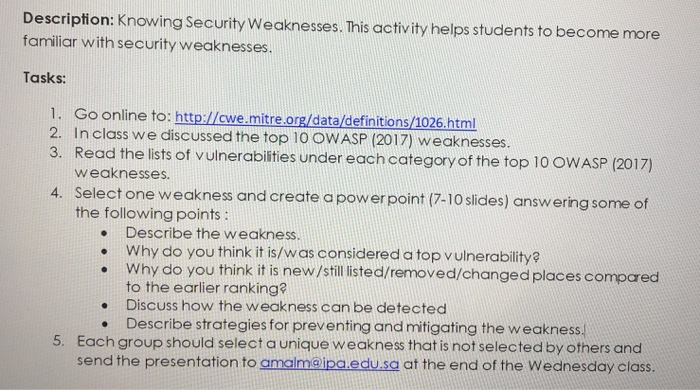
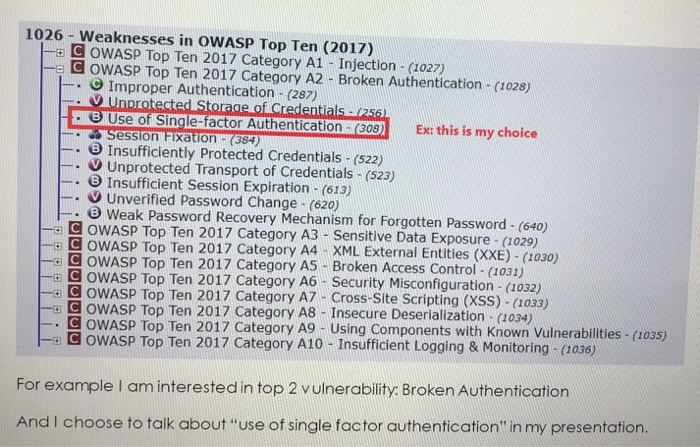
Description: Knowing Security Weaknesses. This activity helps students to become more familiar with security weaknesses. Tasks: 1. Go online to: http://cwe.mitre.org/data/definitions/1026.html 2. In class we discussed the top 10 OWASP (2017) weaknesses. 3. Read the lists of vulnerabilities under each category of the top 10 OWASP (2017) weaknesses. 4. Select one weakness and create a power point (7-10 slides) answering some of the following points: Describe the weakness. Why do you think it is/was considered a top vulnerability? Why do you think it is new/still listed/removed/changed places compared to the earlier ranking? Discuss how the weakness can be detected Describe strategies for preventing and mitigating the weakness. 5. Each group should select a unique weakness that is not selected by others and send the presentation to amalm@ipa.edu.sa at the end of the Wednesday class. 1026 - Weaknesses in OWASP Top Ten (2017) -8 COWASP Top Ten 2017 Category A1 - Injection - (1027) COWASP Top Ten 2017 Category A2 - Broken Authentication - (1028) Improper Authentication - (287) Unprotected Storage of Credentials - (256) B Use of Single-factor Authentication - (308) Session Fixation - (384) Insufficiently Protected Credentials - (522) Unprotected Transport of Credentials - (523) Insufficient Session Expiration - (613) Unverified Password Change - (620) . . . Ex: this is my choice 8 Weak Password Recovery Mechanism for Forgotten Password - (640) OWASP Top Ten 2017 Category A3 - Sensitive Data Exposure - (1029) XML External Entities (XXE) - (1030) Broken Access Control - (1031) E3 COWASP Top Ten 2017 Category A4 COWASP Top Ten 2017 Category A5 D COWASP Top Ten 2017 Category A6- Security Misconfiguration - (1032) O COWASP Top Ten 2017 Category A7- Cross-Site Scripting (XSS) - (1033) Insecure Deserialization - (1034) D OWASP Top Ten 2017 Category A8 OWASP Top Ten 2017 Category A9 Using Components with Known Vulnerabilities - (1035) OWASP Top Ten 2017 Category A10 - Insufficient Logging & Monitoring - (1036) For example I am interested in top 2 vulnerability: Broken Authentication And I choose to talk about use of single factor authentication in my presentation.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


