I have this apcsp lab that involves cipering, and im not familiar with the process that goes along with it, nor do I know how to go about even starting this lab. if anyone could help that would be greatly appreciated. We are using C language currently for our labs.

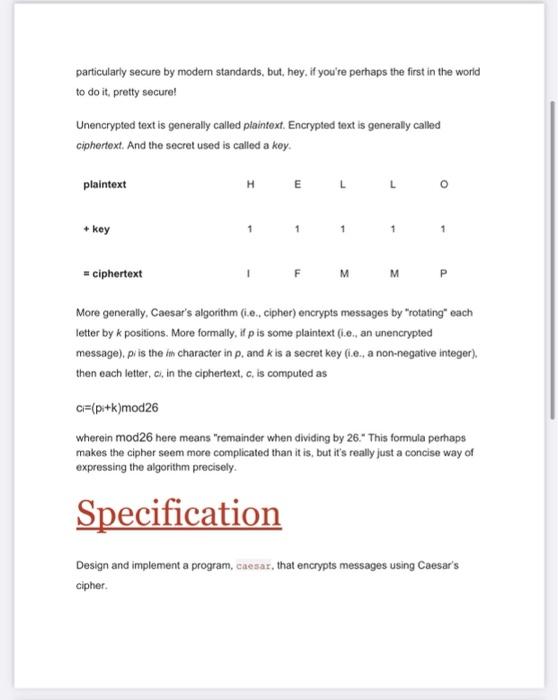
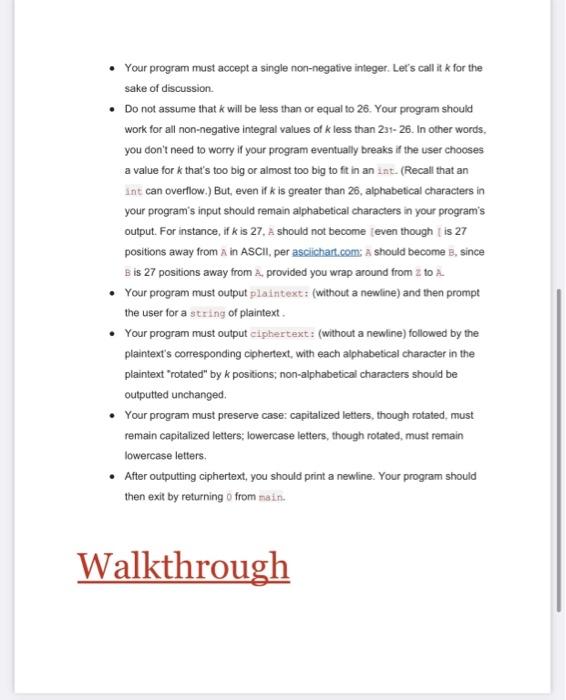
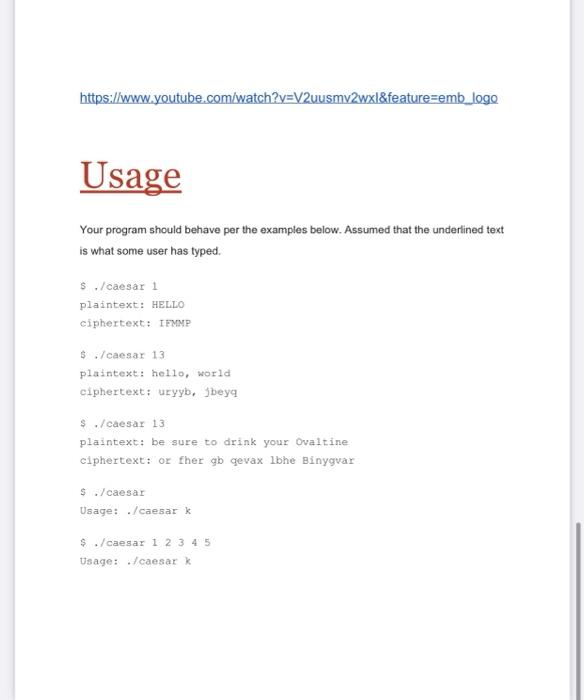
Problem: Caesar Implement a program that encrypts messages using Caesar's cipher, per the below. $ ./caccar 13 plaintext: HELLO ciphertext: URYYB Background Supposedly, Caesar (yes, that Caesar) used to "encrypt" (ie, conceal in a reversible way) confidential messages by shifting each letter therein by some number of places. For instance, he might write A as B, B as C, C as D...., and, wrapping around alphabetically. Z as A. And so, to say HELLO to someone, Caesar might write IFMMP. Upon receiving such messages from Caesar, recipients would have to decrypt" them by shifting letters in the opposite direction by the same number of places. The secrecy of this "cryptosystem" relied on only Caesar and the recipients knowing a secret, the number of places by which Caesar had shifted his letters (0.9., 1). Not particularly secure by modern standards, but, hey, if you're perhaps the first in the world to do it pretty secure! Unencrypted text is generally called plaintext. Encrypted text is generally called ciphertext. And the secret used is called a key plaintext H E key 1 = ciphertext M More generally, Caesar's algorithm (i.e. cipher) encrypts messages by "rotating" each letter by k positions. More formally, if p is some plaintext (1.0., an unencrypted message). pris the character in p. and k is a secret key (.e., a non-negative integer). then each letter, c, in the ciphertext, c, is computed as c={pi+k)mod26 wherein mod26 here means "remainder when dividing by 26." This formula perhaps makes the cipher seem more complicated than it is, but it's really just a concise way of expressing the algorithm precisely. Specification Design and implement a program, caesar, that encrypts messages using Caesar's cipher Your program must accept a single non-negative integer. Let's call it k for the sake of discussion . Do not assume that k will be less than or equal to 26. Your program should work for all non-negative integral values of kless than 231-26. In other words, you don't need to worry if your program eventually breaks if the user chooses a value fork that's too big or almost too big to fit in an int(Recall that an int can overflow.) But, even if k is greater than 26, alphabetical characters in your program's input should remain alphabetical characters in your program's output. For instance, ifk is 27. A should not become even though is 27 positions away from Ain ASCII, per asciichar.com: A should become B, since Bis 27 positions away from A provided you wrap around from z to A Your program must output plaintext: (without a newline) and then prompt the user for a string of plaintext Your program must output ciphertext: (without a newline) followed by the plaintext's corresponding ciphertext, with each alphabetical character in the plaintext rotated" by k positions, non-alphabetical characters should be outputted unchanged Your program must preserve case: capitalized letters, though rotated, must remain capitalized letters; lowercase letters, though rotated, must remain lowercase letters After outputting ciphertext, you should print a newline. Your program should then exit by returning from main. Walkthrough https://www.youtube.com/watch?v=V2uusmy2wxI&feature=emb_logo Usage Your program should behave per the examples below. Assumed that the underlined text is what some user has typed. $ ./ caesar 1 plaintext: HELLO ciphertext: IEMMP $ ./caesar 13 plaintext: hello, world ciphertext: uryyb, beya $ ./caesar 13 plaintext: be sure to drink your Ovaltine ciphertext: or her gb gevax lbhe Binygvar $ ./caesar Usage: ./caesar k $ ./caesar 1 2 3 4 5 Usage: ./caesar Hints The user will enter in plaintext and the shift value K. Once you have both k and some plaintext, p, it's time to encrypt the latter with the former. Recall that you can iterate over the characters in a string, printing each one at a time with code like the below: for (int i = 0, n-istrlen(p); i
<>