Answered step by step
Verified Expert Solution
Question
1 Approved Answer
i need help with these questions A software engineer is developing a chatbot that can discuss political issues with a human. The engineer is concerned

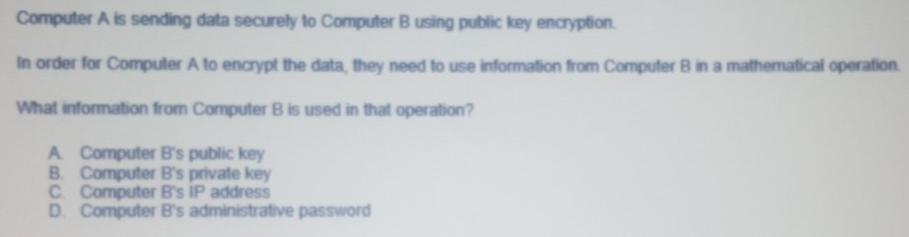

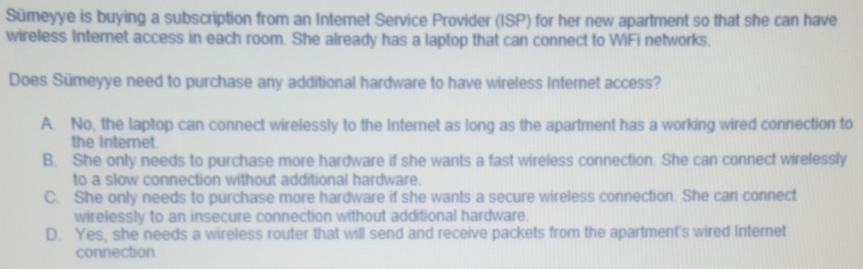
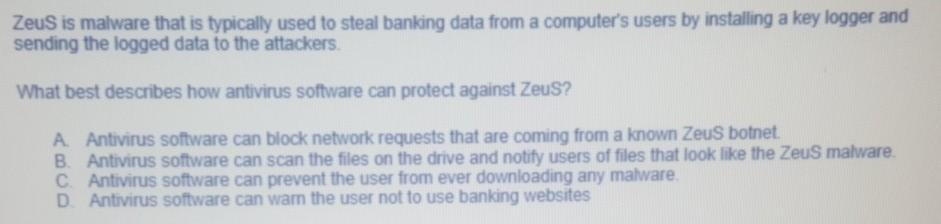
i need help with these questions
A software engineer is developing a chatbot that can discuss political issues with a human. The engineer is concerned that people might try to break into the database to discover the political opinions of the users, so they do not want to store any Pll in the database at all Which of these pieces of information is least likely to be PH? A Last name B. Time zone C Email address D. Social media username Computer Ais sending data securely to Computer B using public key encryption In order for Computer A to encrypt the data, they need to use information from Computer B in a mathematical operation What information from Computer B is used in that operation? A Computer B's public key B. Computer B's private key C Computer B's IP address D. Computer B's administrative password Billy receives a message from a stranger on a social media website that simply says "I know where you live." Billy tried to think about his online activities, and whether or not those activities could have revealed his location Which of these online activities is least likely to have revealed his location to the stranger? A Uploading a photo of their cat sleeping in the garden (with no house visible) B. Granting the social media site access to their geolocation while searching for nearby posts. C. Looking up driving directions to their house on a mapping site over an unsecured HTTP connection D. Reading news sites in a browser with third-party cookies enabled E Uploading a photo of their house, as taken from the street Smeyye is buying a subscription from an Internet Service Provider (ISP) for her new apartment so that she can have wireless Internet access in each room. She already has a laptop that can connect to WiFi networks Does Smeyye need to purchase any additional hardware to have wireless Internet access? A No, the laptop can connect wirelessly to the Internet as long as the apartment has a working wired connection to the Internet B. She only needs to purchase more hardware if she wants a fast wireless connection. She can connect wirelessly to a slow connection without additional hardware CShe only needs to purchase more hardware if she wants a secure wireless connection. She can connect wirelessly to an insecure connection without additional hardware. D. Yes, she needs a wireless router that will send and receive packets from the apartment's wired Internet connection Zeus is malware that is typically used to steal banking data from a computer's users by installing a key logger and sending the logged data to the attackers. What best describes how antivirus software can protect against Zeus? A Antivirus software can block network requests that are coming from a known Zeus botnet. B. Antivirus software can scan the files on the drive and notify users of files that look like the Zeus malware. C. Antivirus software can prevent the user from ever downloading any malware. D. Antivirus software can warn the user not to use banking websitesStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


