Answered step by step
Verified Expert Solution
Question
1 Approved Answer
i want three msq for this case study LEARNING OBJECTIVES By the end of this chapter, you should be able to: = Describe the threat
i want three msq for this case study 
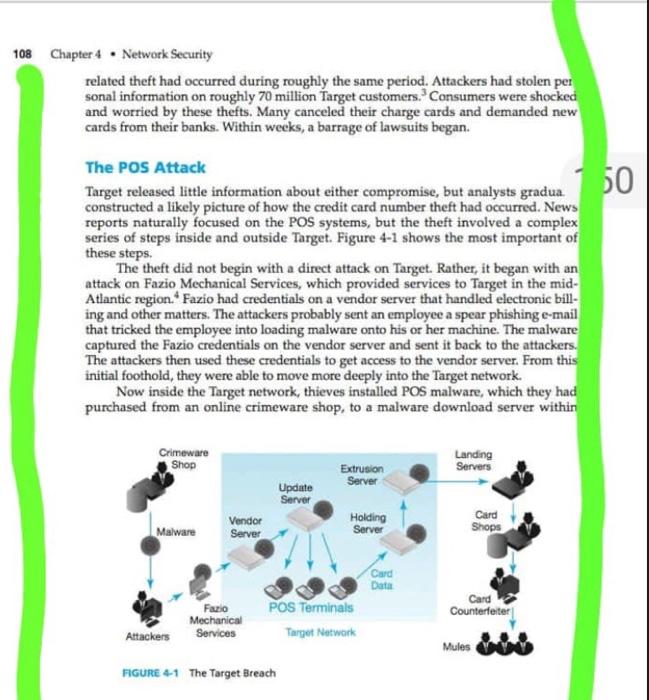


LEARNING OBJECTIVES By the end of this chapter, you should be able to: = Describe the threat environment, including types of attacks and types of attack - Explain how to protect dialogues by cryptography, including encryption for confidentiality, electronic signatures, and host-to-host virtual private networks (VPNs). - Evaluate alternative authentication mechanisms, including passwords, smart cards, biometrics, digital certificate authentication, and two-factor authentication. - Describe firewall protection, including stateful packet inspection, next-generation firewalls, and related intrusion prevention systems. - Describe the role of antivirus protection. THE TARGET BREACH Near the end of the 2013 holiday season, Target announced that thieves had stolen data from 40 million credit cards scanned at Target stores in preceding weeks. 1 The attackers had done this by downloading malware to nearly all point-of-sale (POS) systems in American Target stores. It captured magnetic stripe information and sent it to data thieves.2 Target initially did not reveal the fact that thieves were already committing fraud with the stolen card data. A month later, Target announced that a separate but 'Alastair Jamieson and Erin McClam, "Millions of Target Customers' Credit, Debit Card Accounts May Be Hit by Data Breach, "NBC News, December 19, 2013. hatp// /wwwnbenews.com/business/consumer/ millions-target-customers-credit-debit-card -aceounts-may-be-hit-20 D11775203. 2 Jaikumar Viayan, "Security Firm IDs Malware Used in Target Attack" Computerworld com. httpe//www computerworld. com/s/article/9245491/Security_firm_IDr_malware, used, in_. Target attack 107 Chapter 4 - Network Security related theft had occurred during roughly the same period. Attackers had stolen personal information on roughly 70 million Target customers. 3 Consumers were shocked and worried by these thefts. Many canceled their charge cards and demanded new cards from their banks. Within weeks, a barrage of lawsuits began. apter 4 - Network Security related theft had occurred during roughly the same period. Attackers had stolen per sonal information on roughly 70 million Target customers. 3 Consumers were shocked and worried by these thefts. Many canceled their charge cards and demanded new cards from their banks. Within weeks, a barrage of lawsuits began. The POS Attack Target released little information about either compromise, but analysts gradua. constructed a likely picture of how the credit card number theft had occurred. News reports naturally focused on the POS systems, but the theft involved a complex series of steps inside and outside Target. Figure 4-1 shows the most important of these steps. The theft did not begin with a direct attack on Target. Rather, it began with an attack on Fazio Mechanical Services, which provided services to Target in the midAtlantic region. 4 Fazio had credentials on a vendor server that handled electronic billing and other matters. The attackers probably sent an employee a spear phishing e-mail that tricked the employee into loading malware onto his or her machine. The malware captured the Fazio credentials on the vendor server and sent it back to the attackers. The attackers then used these credentials to get access to the vendor server. From this initial foothold, they were able to move more deeply into the Target network. Now inside the Target network, thieves installed POS malware, which they had purchased from an online crimeware shop, to a malware download server within attackers outside the Target network. 15 This extrusion server pulled batches of card data sets from the holding server and transmitted them to landing servers in Russip Brazil, Miami, and other locations. 16 The thieves could not conceal the Internet p tocol (IP) addresses of the landing servers, so they probably moved the data quici to other servers. Now the attackers monetized their stolen data. They wholesaled batches of data to online cand shops that then sold the data to counterfeiters. These card shops held stripe information in a searchable database. This allowed counterfeiters to purchase card stripe information selectively. For example, thieves know that using a credit card in a city that is not the owner's may result in a credit freeze. Consequently, card shops allowed customers to search by zip code. Counterfeiters also refined their purchases in other ways, based on such factors as whether the card had a high debt limit. Based on the characteristics of each card, counterfeiters paid from $20 to more than $100 per card. The first customers received a money-back guarantee that 100% of the card data was useable. 17 Over time, the guaranteed percentage fell, and prices declined. The counterfeiters used the card data to create fake credit cards that looked legitimate down to the graphics used by individual banks. They then copied data from a single legitimate card onto the magnetic stripe of each counterfeit card. This allowed them to purchase high-end merchandise and then sell the merchandise to traditional fences. However, the counterfeiters did not make the purchases themselves. Instead, they hired a small corps of "mules" to make the actual purchases or take cash out of ATMs. One thing is missing from the figure. The attacks needed to transmit control messages frequently into the Target network in order to compromise servers and take actions to direct actions on these servers during the attack. All of these messages had to go through Target's firewalls. Showing this information in Figure 4-1 would create an unintelligible spiderweb of arrows. However, it was critical for the attackers to maintain a hole in the victim's firewalls during the entire attack process. Test Your Understanding 1. a) How did the attackers gain access to Target's network? b) List the internal Target servers the attackers compromised. c) How did the attackers exfiltrate the card data? d) List the criminal groups, besides the main attackers, who were involved in the overall process. e) What benefit did the attackers seek to obtain from their actions? f ) Critique (positively or negatively) the fact that Target knew that fraud was already occurring with the stolen card data but did not reveal this when it announced the breach. THE TARGET BREACH Near the end of the 2013 holiday season, Target announced that thieves had stolen data from 40 million credit cards scanned at Target stores in preceding weeks. 1 The attackers had done this by downloading malware to nearly all point-of-sale (POS) systems in American Target stores. It captured magnetic stripe information and sent it to data thieves. 2 Target initially did not reveal the fact that thieves were already committing fraud with the stolen card data. A month later, Target announced that a separate but 1 Alastair Jamieson and Erin McClam, 'Millions of Target Customers' Credit, Debit Card Accounts May Be Hit by Data Breach, NBC. News, December 19, 2013. hitp://www.nbenews.com/business/consumer/ millions-target-customers-credit-debit-cand-accounts-may-be-hit-22D11775203 "Jaikumar Vijayan, "Security Firm IDs Malware Used in Target Attack," Computerworld com. http://www computerworld.com/s/article/9245491/Security_firm_ID. malware, used in_Target attack 



Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


