Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I want to solve these two questions.. You can use this page of the article for question 3 in particular.. I want their confirmed answer
I want to solve these two questions.. You can use this page of the article for question 3 in particular.. I want their confirmed answer

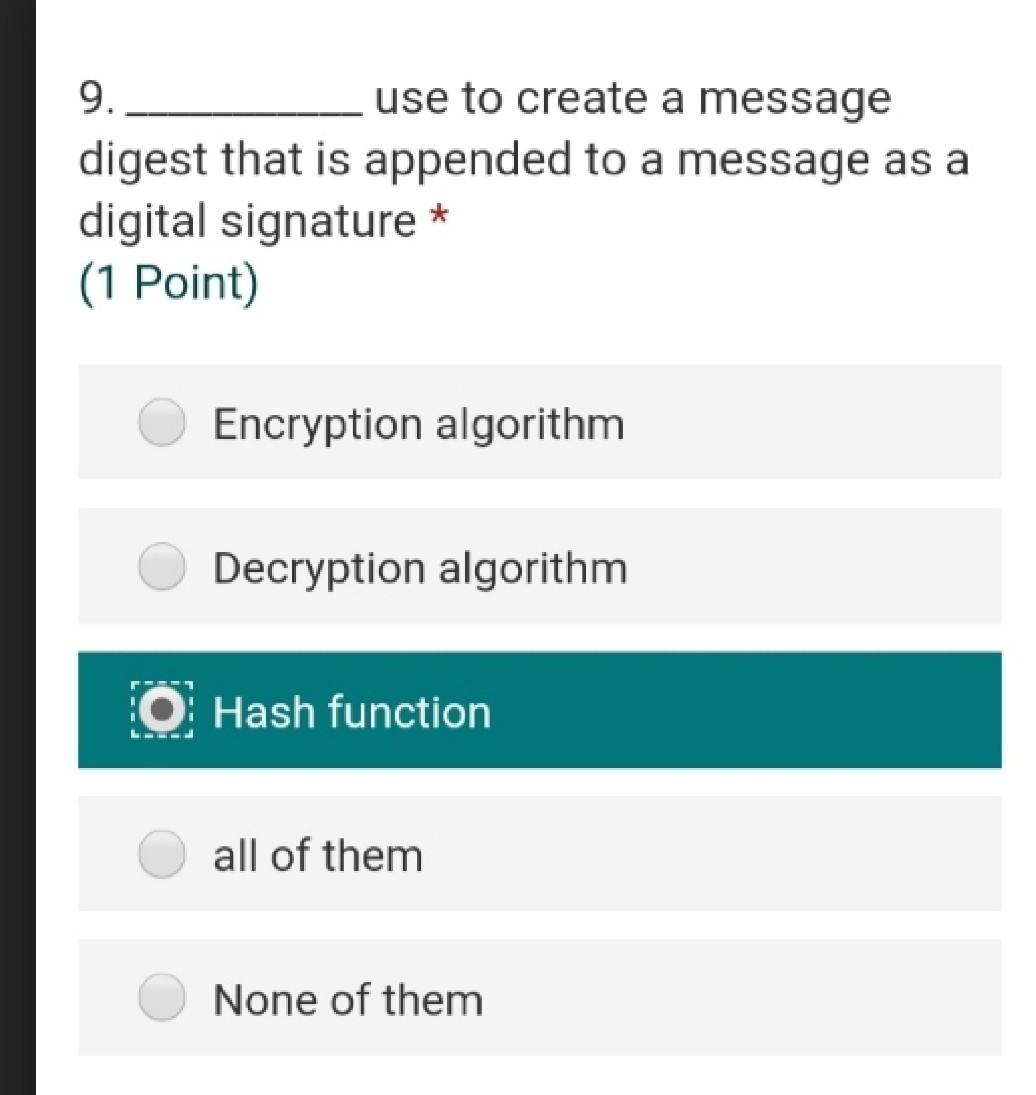
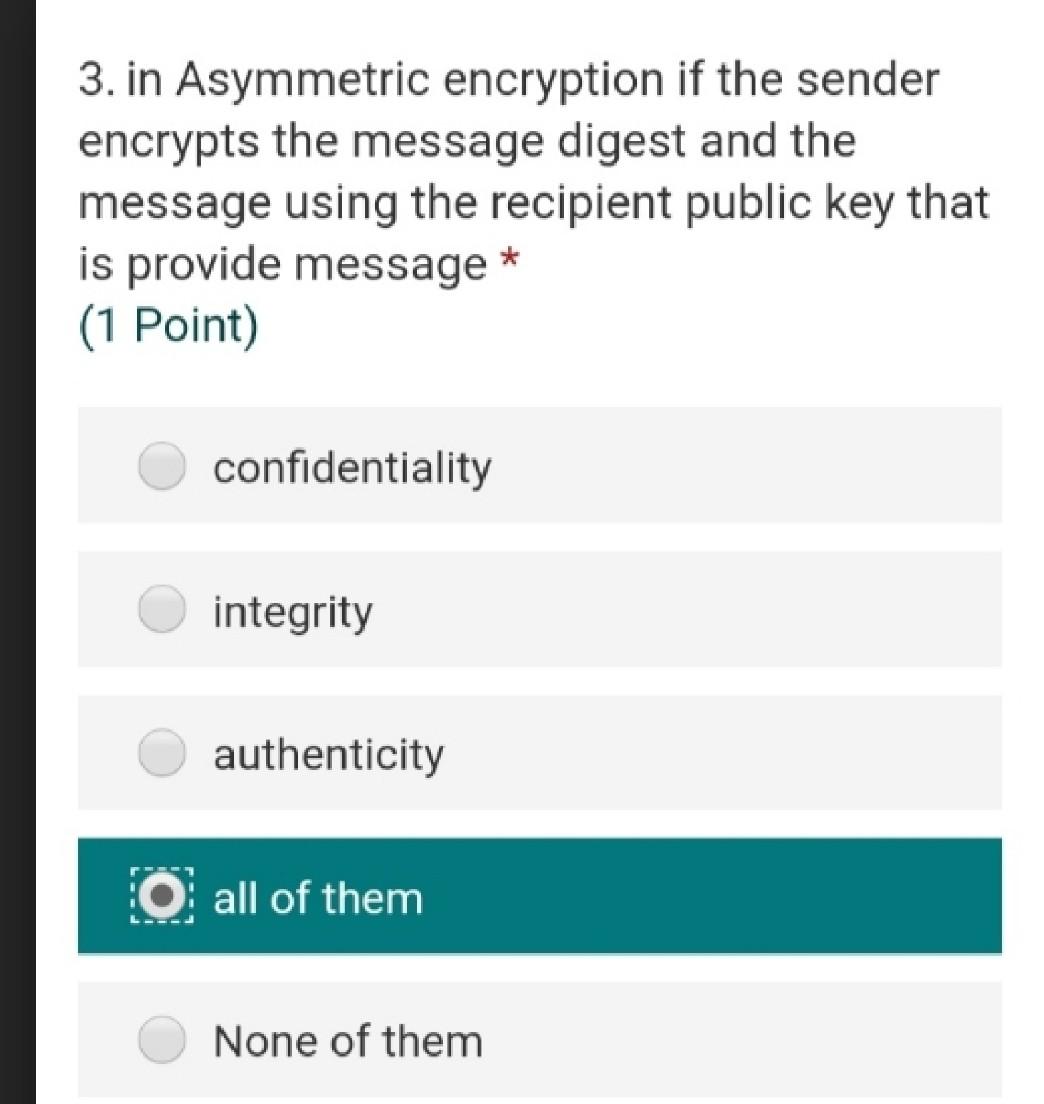
Internet Plaintext Ciphertext Plaintext Encryption Algorithm Decryption Algorithm Asymmetric encryption, commonly known as public key encryption, uses different keys, a public key known by all and a private key known by only the sender and the receiver. Both the sender and the receiver each has a pair of these keys, one public and one private. To encrypt a message, from sender A to receiver B, as shown in Figure 2, both A and B must create their own pairs of keys. Then A and B exchange their public keysanybody can acquire them. When A is to send a message M to B, A uses B's public key to encrypt M. On receipt of M, B then uses his or her private key to decrypt the message M. A hash function takes an input message M and creates a code from it. The code commonly referred to as a hash or a message digest, will be discussed more in the next section. A one-way hash function is used to create a digital signature of the messagejust like a human fingerprint. The hash function is therefore used to provide the message's integrity and authenticity. 9. use to create a message digest that is appended to a message as a digital signature * (1 Point) Encryption algorithm Decryption algorithm O Hash function all of them None of them 3. in Asymmetric encryption if the sender encrypts the message digest and the message using the recipient public key that is provide message (1 Point) confidentiality integrity authenticity O all of them None of them
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


