Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I will gladly appreciate the help. CI2440-Introduction to Computer Securityy Information Stored/Transmitted P4 Lab 2 Confidential Critical 1-Course Gradebook 2-University news 3-Student Attendance 4-List of
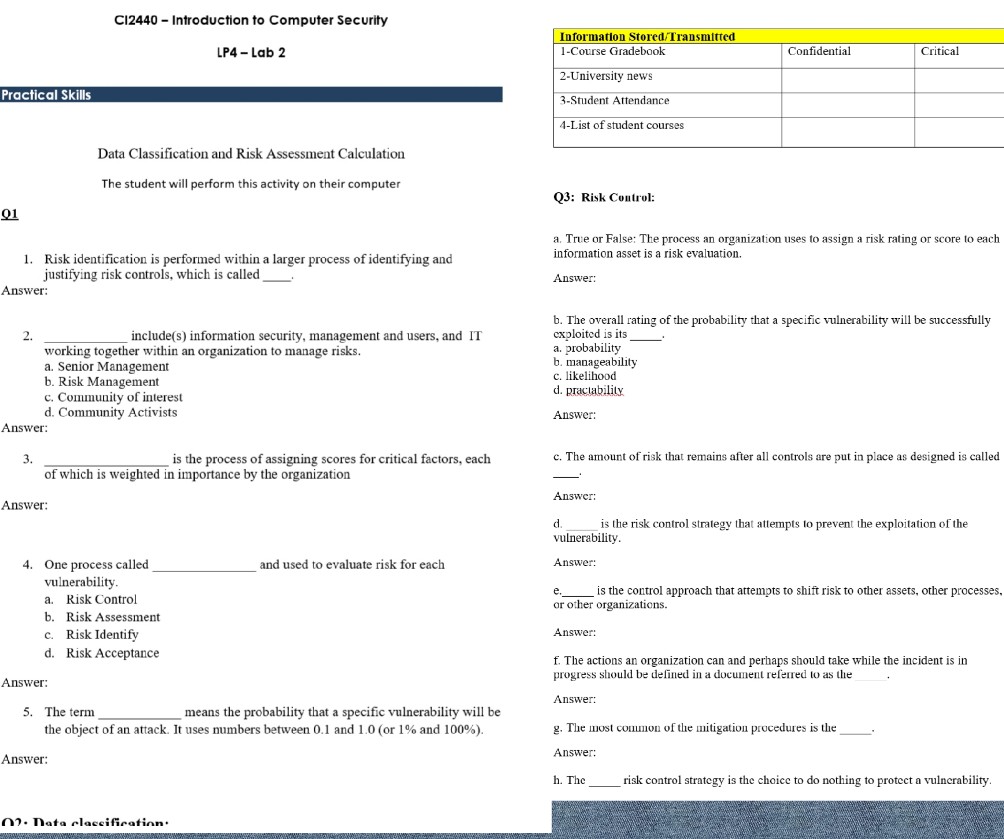
I will gladly appreciate the help.
CI2440-Introduction to Computer Securityy Information Stored/Transmitted P4 Lab 2 Confidential Critical 1-Course Gradebook 2-University news 3-Student Attendance 4-List of student courses Practical Skills Data Classification and Risk Assessment Calculation The student will perform this activity on their computer Q3: Risk Control: 01 risk rating or score to each a. True or False: The process an organizaton uses to assign information asset is a risk evaluation Risk identification is performed within a larger process of identifying and ustifying risk controls, which is called . 1. Answer Answer: b. The overall rating of the probability that a specific vulnerability will be successfully cxploited is its a. probability b. manageability c. likelihood d. praciabilitv 2. include(s) information security, management and users, and IT working together within an organization to manage risks a. Senior Management b. Risk Management C. Community of nlerest d. Community Activists Answer: Answer: is the process of assigning scores for critical factors, each c. The amount of risk that remains after all controls are put in place as designed is called of which is weighted in importance by the organization Answer Answer is the risk control strategy that attempts lo prevent the exploitation of the vulnerability 4. One process called vulnerability a. Risk Control b. Risk Assessment c. Risk Identify d. Risk Acceptance and used to evaluate risk for eaclh Answer is the control approach that attempts to shift risk to other assets, other processes, or other organizations Answer f. The actions an organization can and perhaps should take while the incident is in progress should be delined in a document refered to as the Answer Answer 5. The term means the probability that a specific vulnerability will be the object of an attack. It uses numbers between 0.1 and 1 0 (or 1% and 100%). g. Tlhe most comon of the mitigation procedures is the Answer: Answer h. The risk control strategy is the choice to do nothing to protect vulnerabilityStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


