In addition to the general control IT areas (information systems operations, information security, and change control management), the IT audit team will test certain relevant application controls. Meetings between the IT audit team and appropriate members of the financial audit team will occur to:
- understand how application or automated controls work
- evaluate if they have been adequately designed and implemented
- assess whether they operate effectively
The relevant application controls to be tested are noted below.
| Working Paper Reference # | Relevant Application | Relevant Application Controls See Exhibit 3.5b for a complete listing of the relevant application controls |
| | | |
| | | |
| | | |
Exhibit 3.5b
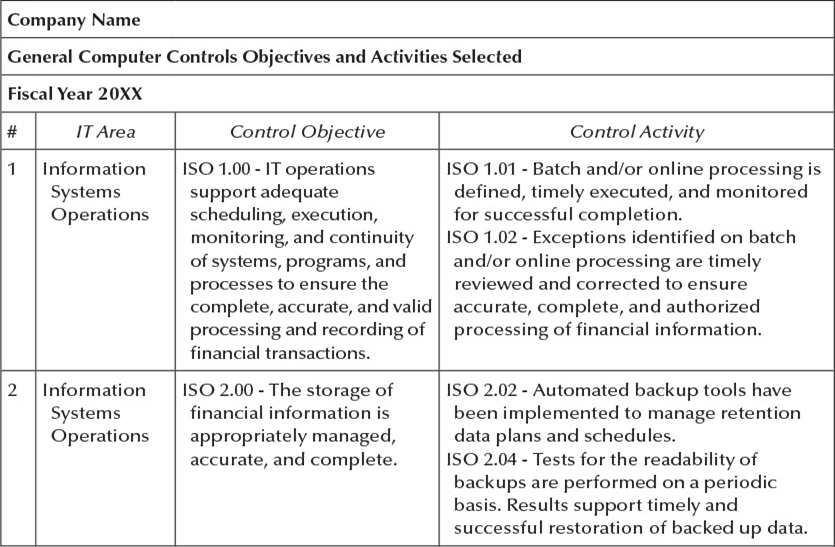
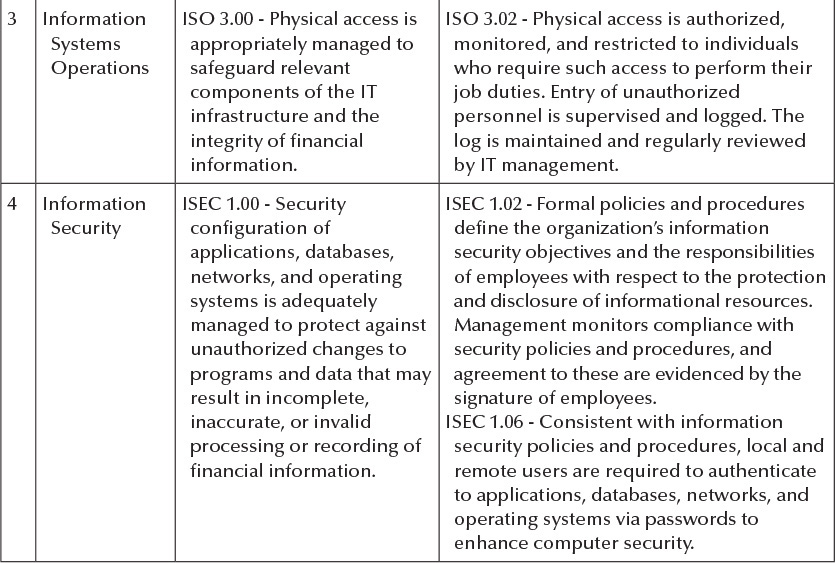
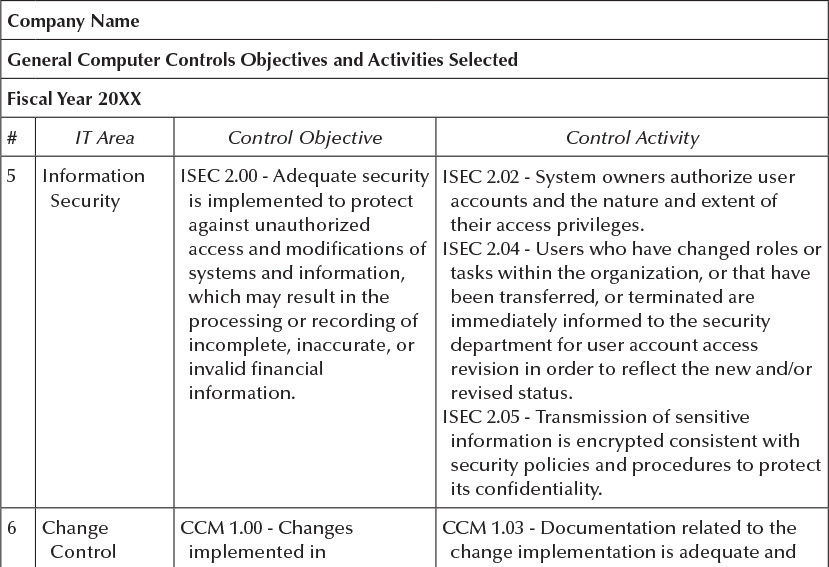
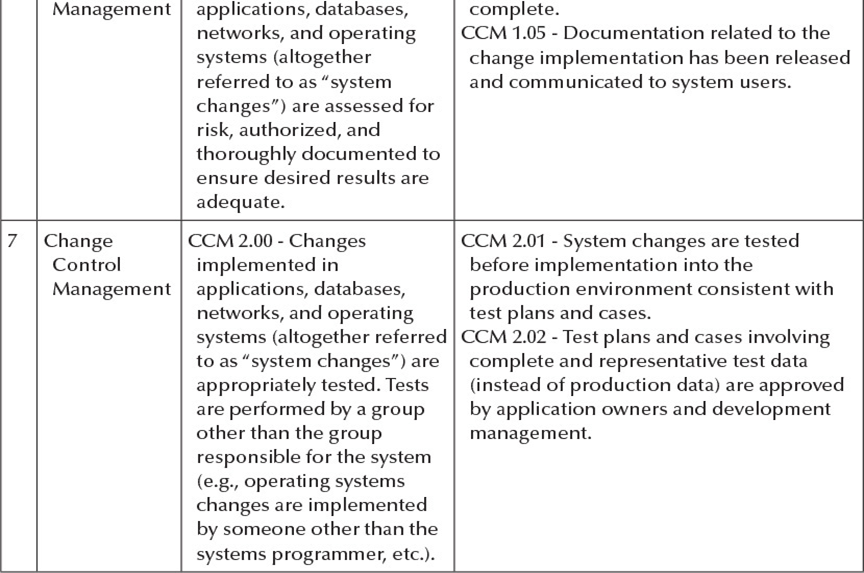
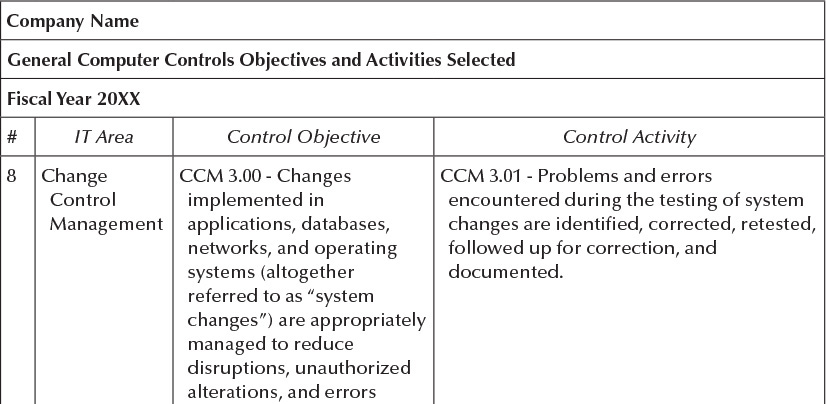
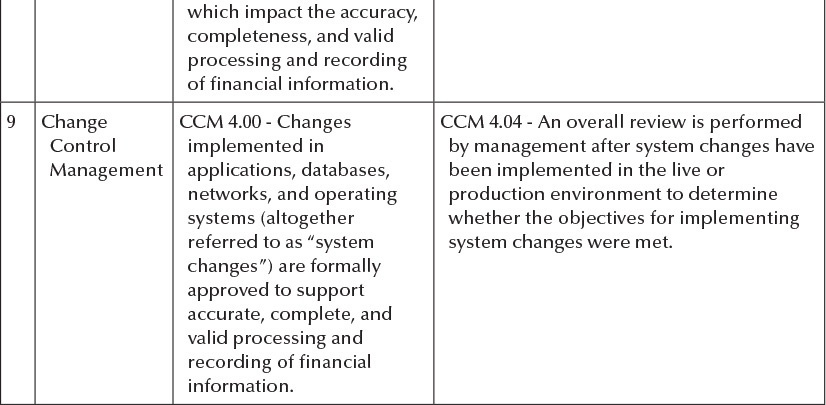
Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX # 1 IT Area Information Systems Operations Control Objective Control Activity ISO 1.00 - IT operations ISO 1.01 - Batch and/or online processing is support adequate defined, timely executed, and monitored scheduling, execution, for successful completion. monitoring, and continuity ISO 1.02 - Exceptions identified on batch of systems, programs, and and/or online processing are timely processes to ensure the reviewed and corrected to ensure complete, accurate, and valid accurate, complete, and authorized processing and recording of processing of financial information. financial transactions. ISO 2.00 - The storage of ISO 2.02 - Automated backup tools have financial information is been implemented to manage retention appropriately managed, data plans and schedules. accurate, and complete. ISO 2.04 - Tests for the readability of backups are performed on a periodic basis. Results support timely and successful restoration of backed up data. 2 Information Systems Operations 3 Information Systems Operations 4 Information Security ISO 3.00 - Physical access is ISO 3.02 - Physical access is authorized, appropriately managed to monitored, and restricted to individuals safeguard relevant who require such access to perform their components of the IT job duties. Entry of unauthorized infrastructure and the personnel is supervised and logged. The integrity of financial log is maintained and regularly reviewed information. by IT management. ISEC 1.00 - Security ISEC 1.02 - Formal policies and procedures configuration of define the organization's information applications, databases, security objectives and the responsibilities networks, and operating employees with respect to the protection systems is adequately and disclosure of informational resources. managed to protect against Management monitors compliance with unauthorized changes to security policies and procedures, and programs and data that may agreement to these are evidenced by the result in incomplete, signature of employees. inaccurate, or invalid ISEC 1.06 - Consistent with information processing or recording of security policies and procedures, local and financial information. remote users are required to authenticate to applications, databases, networks, and operating systems via passwords to enhance computer security. Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX # IT Area 5 Information Security Control Objective Control Activity ISEC 2.00 - Adequate security ISEC 2.02 - System owners authorize user is implemented to protect accounts and the nature and extent of against unauthorized their access privileges. access and modifications of ISEC 2.04 - Users who have changed roles or systems and information, tasks within the organization, or that have which may result in the been transferred, or terminated are processing or recording of immediately informed to the security incomplete, inaccurate, or department for user account access invalid financial revision in order to reflect the new and/or information. revised status. ISEC 2.05 - Transmission of sensitive information is encrypted consistent with security policies and procedures to protect its confidentiality. 6 Change Control CCM 1.00 - Changes implemented in CCM 1.03 - Documentation related to the change implementation is adequate and 7 Management applications, databases, complete. networks, and operating CCM 1.05 - Documentation related to the systems (altogether change implementation has been released referred to as "system and communicated to system users. changes") are assessed for risk, authorized, and thoroughly documented to ensure desired results are adequate. Change CCM 2.00 - Changes CCM 2.01 - System changes are tested Control implemented in before implementation into the Management applications, databases, production environment consistent with networks, and operating test plans and cases. systems (altogether referred CCM 2.02 - Test plans and cases involving to as "system changes") are complete and representative test data appropriately tested. Tests (instead of production data) are approved are performed by a group by application owners and development other than the group management. responsible for the system (e.g., operating systems changes are implemented by someone other than the systems programmer, etc.). Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX Control Activity # IT Area Control Objective 8 Change CCM 3.00 - Changes Control implemented in Management applications, databases, networks, and operating systems (altogether referred to as "system changes") are appropriately managed to reduce disruptions, unauthorized alterations, and errors CCM 3.01 - Problems and errors encountered during the testing of system changes are identified, corrected, retested, followed up for correction, and documented. which impact the accuracy, completeness, and valid processing and recording of financial information. 9 Change CCM 4.00 - Changes Control implemented in Management applications, databases, networks, and operating systems (altogether referred to as "system changes") are formally approved to support accurate, complete, and valid processing and recording of financial information. CCM 4.04 - An overall review is performed by management after system changes have been implemented in the live or production environment to determine whether the objectives for implementing system changes were met. Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX # 1 IT Area Information Systems Operations Control Objective Control Activity ISO 1.00 - IT operations ISO 1.01 - Batch and/or online processing is support adequate defined, timely executed, and monitored scheduling, execution, for successful completion. monitoring, and continuity ISO 1.02 - Exceptions identified on batch of systems, programs, and and/or online processing are timely processes to ensure the reviewed and corrected to ensure complete, accurate, and valid accurate, complete, and authorized processing and recording of processing of financial information. financial transactions. ISO 2.00 - The storage of ISO 2.02 - Automated backup tools have financial information is been implemented to manage retention appropriately managed, data plans and schedules. accurate, and complete. ISO 2.04 - Tests for the readability of backups are performed on a periodic basis. Results support timely and successful restoration of backed up data. 2 Information Systems Operations 3 Information Systems Operations 4 Information Security ISO 3.00 - Physical access is ISO 3.02 - Physical access is authorized, appropriately managed to monitored, and restricted to individuals safeguard relevant who require such access to perform their components of the IT job duties. Entry of unauthorized infrastructure and the personnel is supervised and logged. The integrity of financial log is maintained and regularly reviewed information. by IT management. ISEC 1.00 - Security ISEC 1.02 - Formal policies and procedures configuration of define the organization's information applications, databases, security objectives and the responsibilities networks, and operating employees with respect to the protection systems is adequately and disclosure of informational resources. managed to protect against Management monitors compliance with unauthorized changes to security policies and procedures, and programs and data that may agreement to these are evidenced by the result in incomplete, signature of employees. inaccurate, or invalid ISEC 1.06 - Consistent with information processing or recording of security policies and procedures, local and financial information. remote users are required to authenticate to applications, databases, networks, and operating systems via passwords to enhance computer security. Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX # IT Area 5 Information Security Control Objective Control Activity ISEC 2.00 - Adequate security ISEC 2.02 - System owners authorize user is implemented to protect accounts and the nature and extent of against unauthorized their access privileges. access and modifications of ISEC 2.04 - Users who have changed roles or systems and information, tasks within the organization, or that have which may result in the been transferred, or terminated are processing or recording of immediately informed to the security incomplete, inaccurate, or department for user account access invalid financial revision in order to reflect the new and/or information. revised status. ISEC 2.05 - Transmission of sensitive information is encrypted consistent with security policies and procedures to protect its confidentiality. 6 Change Control CCM 1.00 - Changes implemented in CCM 1.03 - Documentation related to the change implementation is adequate and 7 Management applications, databases, complete. networks, and operating CCM 1.05 - Documentation related to the systems (altogether change implementation has been released referred to as "system and communicated to system users. changes") are assessed for risk, authorized, and thoroughly documented to ensure desired results are adequate. Change CCM 2.00 - Changes CCM 2.01 - System changes are tested Control implemented in before implementation into the Management applications, databases, production environment consistent with networks, and operating test plans and cases. systems (altogether referred CCM 2.02 - Test plans and cases involving to as "system changes") are complete and representative test data appropriately tested. Tests (instead of production data) are approved are performed by a group by application owners and development other than the group management. responsible for the system (e.g., operating systems changes are implemented by someone other than the systems programmer, etc.). Company Name General Computer Controls Objectives and Activities Selected Fiscal Year 20XX Control Activity # IT Area Control Objective 8 Change CCM 3.00 - Changes Control implemented in Management applications, databases, networks, and operating systems (altogether referred to as "system changes") are appropriately managed to reduce disruptions, unauthorized alterations, and errors CCM 3.01 - Problems and errors encountered during the testing of system changes are identified, corrected, retested, followed up for correction, and documented. which impact the accuracy, completeness, and valid processing and recording of financial information. 9 Change CCM 4.00 - Changes Control implemented in Management applications, databases, networks, and operating systems (altogether referred to as "system changes") are formally approved to support accurate, complete, and valid processing and recording of financial information. CCM 4.04 - An overall review is performed by management after system changes have been implemented in the live or production environment to determine whether the objectives for implementing system changes were met












