Question
In the C language integers are 4 bytes and characters are 1 byte. We are considering a 32-bit system in which registers take up 4
In the C language integers are 4 bytes and characters are 1 byte. We are considering a 32-bit system in which registers take up 4 bytes on the stack. Using this and the knowledge you acquired about stack layout you construct the following rough diagram of the following codes stack. This is the stack as the function is entered before any user input has been taken. The question marks indicate garbage data that has not yet been overwritten.
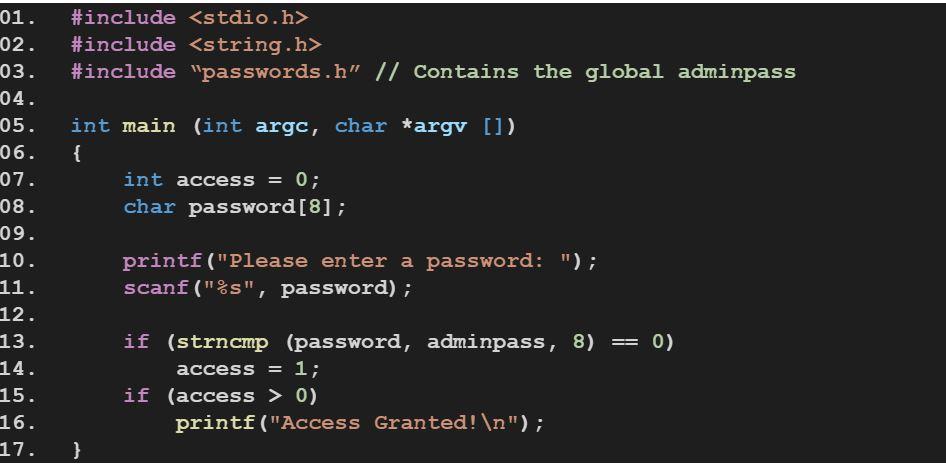
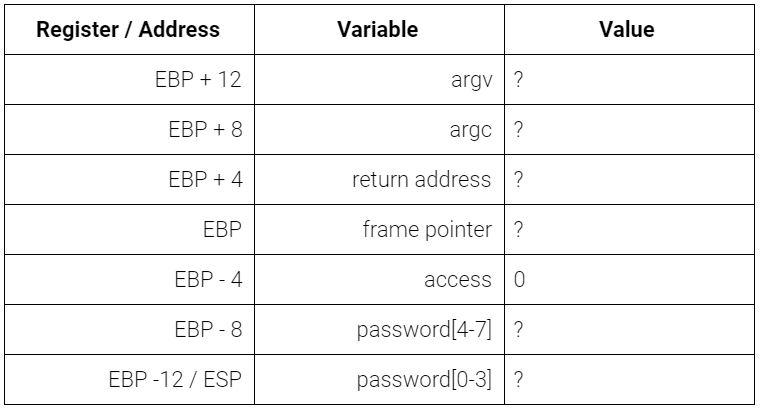
1. We need to begin determining how much data we need in order to overflow. The first step of which is to determine the programmer defined size of our buffer. How many bytes does our buffer hold? Enter the number numerically below: if the buffer holds twenty bytes, you would enter "20" without the quotations. _______________.
2. Now that we know how many bytes of data is required to fill the buffer, we need to determine how many bytes are needed in total to overflow the access variable such that we get the "Access Granted" message. Enter the total number of bytes required to overflow the buffer and access variable. Enter the number numerically below: if the required number of bytes is thirty, you would enter "30" without the quotations: ________________.
3. Now suppose we wanted to overflow into the return address for a more malicious attack. How many bytes of garbage data would we need in total to overflow up to the return address. This is the number of bytes such that any additional bytes would overwrite data in the return address, but does not currently overwrite any data in the return address. In other words, this is the number of bytes to completely overflow the frame pointer from our declared buffer. Enter the total number of bytes required to overflow up to the return address. Enter the number numerically below: if the required number of bytes is forty, you would enter "40" without the quotations: ________________.
4. Finally, we want to overflow the return address with a malicious function call. How many bytes of data do we need in total to completely overflow the return address and no further? This is the total number of bytes from the start of the buffer to the end of the return address. Enter the number numerically below: if the required number of bytes is fifty, you would enter "50" without the quotations: __________________.
5. Putting it all together, which of these formulas correctly illustrates the number of bytes of garbage data required such that the next four bytes will overflow the return address. Do not include these four bytes of data in the calculation.
A. ESP's Address + 4 - Buffer's Address
B. ESP's Address + 4 + Buffer's Address
C. EBP's Address + 4 + Buffer's Address
D. EBP's Address + 4 - Buffer's Address
#includeStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


