Question
In the following questions, explain in detail means with reference to the exact messages exchanged and expected by A, B and a man-in-the-middle M; and,
In the following questions, "explain in detail" means with reference to the exact
messages exchanged and expected by A, B and a man-in-the-middle M; and, where
appropriate, with suitable protocol diagrams involving all three.
(b) Explain in detail how a man-in-the-middle M could successfully attack this
protocol if R were not used or if M could eavesdrop on message 3. [4 marks]
(d) Explain in detail how the man-in-the-middle could still successfully attack this
protocol if the confirmation of step 9 were omitted. [8 marks]
(a) Specify a combinational device MAX with two 4-bit inputs i1, i2 and a 4-bit
output o, such that the value output on o is the input that has the greater
value when interpreted as a binary number. [2 marks]
(c) Write a specification of a device Dmax with a 4-bit input i and a 4-bit output o
such that the value output on o on the n-th cycle is the maximum value input
on i on all cycles up to and including the n-th cycle.
(d) Devise a circuit built out of MAX and REG that implements your specification.
[4 marks]
(e) Outline how to prove that your circuit meets your specification.
(a) Give a brief description of the three segments that make up the Global
Positioning System (GPS), and their main software, hardware and information
components. [5 marks]
(b) What are the main timing observables from the GPS signals, and how can
they be processed to give time, position and velocity? [5 marks]
(c) What data is broadcast in the GPS signals, and how is it used by receivers?
[5 marks]
(d) Explain some of the ways in which an additional communication channel can
be used to assist a GPS receiver, and what advantages the user might observe.
[5 marks]
3 Digital Communication II
(a) Describe the OSI (Open Systems Interconnections) reference model and
discuss examples of the networking functions normally associated with each
component. [14 marks]
(b) What do we mean by layer violation? Discuss some of the reasons that
might lead a pragmatic protocol implementer to engage in layer violation and
illustrate with an example. [6 marks]
4 Distributed Systems
(a) You have been asked to design an event composition and aggregation service
to operate above publish/subscribe middleware to be deployed in various
environmental monitoring scenarios. Your service is to advertise and publish
high-level events of interest to applications. It may subscribe to any published
events in the domain of deployment. Your service may itself be distributed.
Identify a list of technical design issues you would raise with your client prior
to specifying the service in detail. [12 marks]
(b) By means of a diagram illustrate the use of vector clocks to implement the
delivery in causal order of multicast messages among members of a closed,
unstructured process group. Include an explanation of the message delivery
algorithm.
) Annotate the circuit to indicate the widths of the transistors required to
give rise and fall times equal to a minimal, balanced inverter. Assume that
p-channel transistors have γ times the resistance of n-channel transistors when
conducting. [4 marks]
(c) Calculate the logical effort and parasitic delay for the circuit. [4 marks]
(d) Sketch a stick diagram for the circuit, arranged for reasonably compact layout.
Assume two layers of metal with power and ground routed in parallel tracks on
the second layer, and arrange for inputs and the output to be available outside
the power rails. [4 marks]
(e) Estimate the size of your layout, assuming a separation of 8λ between the
centre-lines of parallel metal tracks.
(a) What is the difference between partial and total correctness? Illustrate your
answer using the WHILE-Rule. [4 marks]
(b) What are derived rules? Give an example of a derived rule, together with its
derivation. [4 marks]
(c) If {P} C {Q} is a theorem of Hoare logic and if C is correctly annotated then
will the verification conditions necessarily be provable? Justify your answer.
[4 marks]
(d) Would a Java program that translates Hoare formulae to semantically
equivalent higher-order logic formulae be a deep embedding or a shallow
embedding? Justify your answer. [4 marks]
(e) Describe the meaning of the dynamic logic formulae [c]q and
deterministic commands, describe how partial and total Hoare logic correctness
specifications can be formulated in terms of dynamic logic.
(a) What are the pros and cons of distance vector versus link state routing
protocols? Give examples derived from protocols in use today. [10 marks]
(b) Where are hybrid schemes employed and why? [5 marks]
(c) Again using examples, discuss the issues in extending routing to support
multicast. [5 marks]
4 Distributed Systems
(a) It is proposed that persistent, strongly consistent data replicas should be
maintained by a widely distributed, open, unstructured process group.
(i) Discuss the potential advantages of replication, bearing in mind that
strong consistency is required. [2 marks]
(ii) Describe algorithms for maintaining strong consistency while retaining at
least some of the advantages of replication. Show how your algorithms
are robust with respect to concurrency and failure. [8 marks]
(b) A distributed conference application provides a shared whiteboard. Each
member of the conference has a replica of the whiteboard that is managed
by a member of a closed process group. Discuss one approach by which the
processes can achieve mutually exclusive access to the whiteboard, prior to
propagation of the update to the whole group. [8 marks]
(c) Contrast the styles of replica management required for (a) and (b) above.
[2 marks]
3 (TURN OVER)
CST.2008.8.4
5 Comparative Architectures
(a) Why is it important to concentrate on improving the common case (e.g.
the most commonly used operations and resources) when designing a
microprocessor? [4 marks]
(b) What is the major difference between a very long instruction word (VLIW)
processor and a dynamically-scheduled superscalar processor? What impact
does this have on the complexity of the implementation in each case?
[4 marks]
(c) When designing a VLIW processor, why might variable-length instruction
bundles be preferred over fixed-length instructions? [4 marks]
(d) Some VLIW processors contain additional hardware to permit memory
reference speculation.
(i) What optimisation does memory reference speculation permit?
[4 marks]
(ii) Briefly describe the additional hardware required to support this type of
speculation. [4 marks]
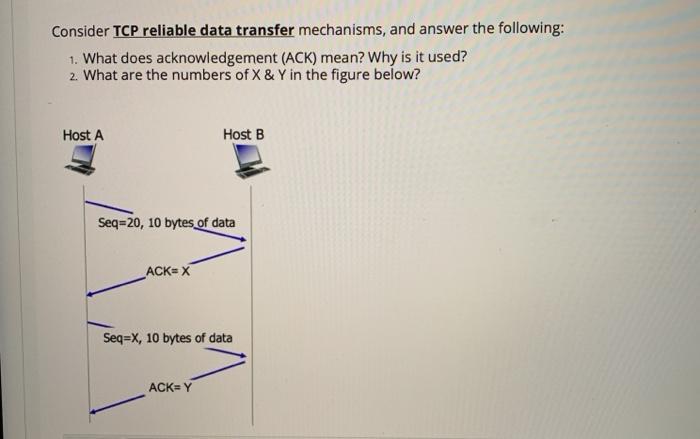
Consider TCP reliable data transfer mechanisms, and answer the following: 1. What does acknowledgement (ACK) mean? Why is it used? 2. What are the numbers of X & Y in the figure below? Host A Seq=20, 10 bytes of data ACK=X Host B Seq=X, 10 bytes of data ACK=Y
Step by Step Solution
There are 3 Steps involved in it
Step: 1
Lets break down and answer the questions in detail First question 1 What does acknowledgement ACK mean Why is it used Acknowledgement ACK in TCP refers to a signal passed between communicating process...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


