Question
In the protocol below, the Reader stores ALL possible combinations of Challenge-Response pairs for every tag it needs to authenticate. During authentication, the Reader broadcasts
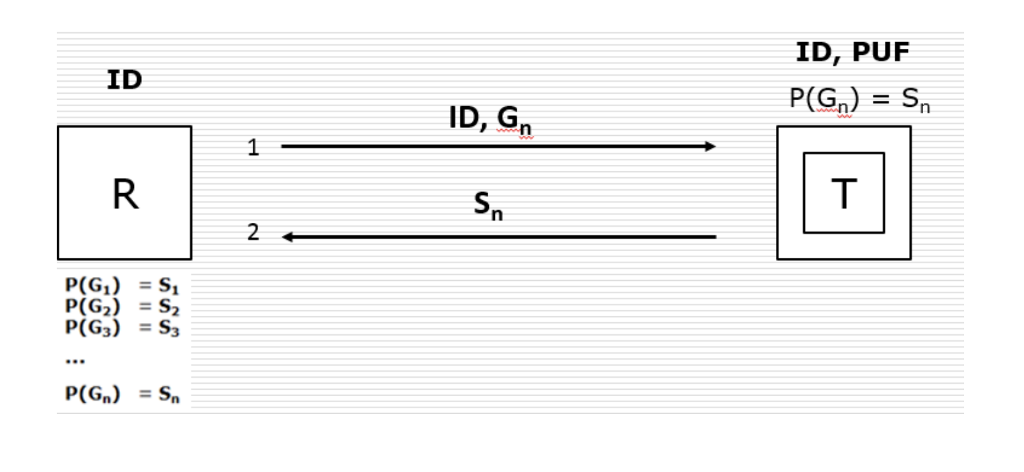
In the protocol below, the Reader stores ALL possible combinations of Challenge-Response pairs for every tag it needs to authenticate. During authentication, the Reader broadcasts the ID of the tag, and a greeting (Gn). Every tag may see this message, but only the one with the right ID will process the message. The right tag with the ID in the message will then feed the greeting to its PUF and compute the response Sn. The response is then sent to the Reader. This should be clear from the Figure below. For the next round of authenticating the same Tag, the process repeats with a new Greeting (Gn+1). Since the Reader has the responses, authentication is straightforward.
From the protocol, and class, it should be clear that eavesdropping attacks are ineffective in this protocol, since the attacker will be able to snoop on challenge response pairs for one round. But this pair will not be used again, attackers gain no practical advantage. Also, since the PUF is not clonable, attackers will not be able to generate the response expected. This much should be clear.
Give one or two reasons as to why you will NOT recommend this protocol if you are in-charge of securing RFID tags. Do not mention Replay Attacks and Jamming attacks.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


