Question: In this programming assignment, you will implement Vigenere encryption and decryption with Cipher Block Chaining (CBC). The original form of Vigenere cipher has been introduced
In this programming assignment, you will implement Vigenere encryption and decryption with Cipher Block Chaining (CBC). The original form of Vigenere cipher has been introduced in L6: Symmetric Encryption (slide No. 15-18). CBC mode has been introduced in L8: Modes of Operation (slide No. 15-19). In the lecture of Modes of Operation, we used Vigenere block cipher as an example to show how to apply the modes of operation to ciphers. The description of Vigenere block cipher is in slide No. 7 of L8: Modes of Operation. Comparing with original form of Vigenere cipher, the Vigenere block cipher defines a block size that is equal to length of Vigenere key. According to the slide No. 18 of L8: Modes of Operation, for CBC mode an IV (Initial Vector) is also needed as input. So, the inputs to the encryption algorithm include Vigenere key, IV and plaintext and the inputs to the decryption algorithm include Vigenere key, IV and cyphertext. In the lecture slides, we have focused on the encryption part. But in this assignment, you will implement both encryption and decryption algorithms. Therefore, you will create two programs or source files: one for the encryption (or encipher) and one for the decryption (or decipher). The encipher program will be run first. When encrypting, the encipher program will take inputs including plaintext, key and IV. The encipher encrypts the plaintext with the key & IV, and generate a file to store the ciphertext. Then when the decipher program is run, the ciphertext file will be used as input along with key & IV. The decipher program decrypts the ciphertext to recover the plaintext.
2. Basic Encryption and Decryption Schemes
In the slides of L8: Modes of Operation, we have mentioned that Vigenere block cipher is a character cipher. Instead of using the XOR defined in CBC mode, we used plus (+) in Vigenere with CBC (slide No. 18 of L8: Modes of Operation). Therefore, the encryption of Vigenere with CBC can be expressed as:
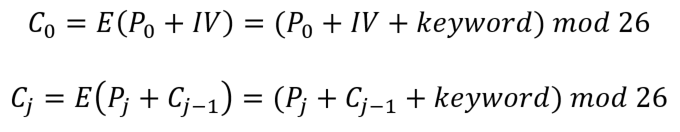
Since we have modified the CBC operation for Vigenere character cipher, we have to adapt the CBC decryption too. Once one already establishes the encryption algorithm (or encipher). The general rule for the decryption algorithm (or decipher) is to run the encryption in reverse. Following this rule, we can express the decryption of Vigenere with CBC as:
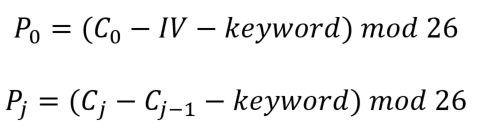
Note: the result of can be negative but modular value should not be negative. Since we have adapted both encryption and decryption of original CBC. The mathematical notations shown above may not match the CBC diagram (Slide No. 16 of L8: Modes of Operation), which uses XOR operation.
3. Implementation
3.1. Preprocessing
The plaintext input to the Vigenere CBC encipher should come from a text file. You may use any text file that is less than 4 Kilobytes in size. You can generate your text file by simply copying and pasting any text content. However, the normal text file contains upper case and lower case alphabetic characters, numbers, punctuations and other special characters including space and line feed etc.. These are way more than 26 letters defined in Vigenere cipher. So you have to preprocess the text file to eliminate all the special characters, numbers, white space and punctuations, as well as convert all upper case letters into lower case letters. The result of preprocessing should be a string of lower case letters. (as shown Figure 1) Then the encipher will use these letter sequences as the plaintext input.

Figure 1: Plaintext after Preprocessing
3.2 Inputs
In addition to the letter sequence you generated from the preprocessing. The Vigenere CBC encipher needs a key and an IV. For this assignment, you would allow the user to enter a key (key length ranges from 2 to 10) and an IV with the same length as key. You may want to mandate that the length of IV should be the same as the key. Inputs to the Vigenere CBC decipher should be the same key and IV, as well as the ciphertext. The ciphertext sequence should be generated by the Vigenere CBC encipher.
The easy way to allow the users input is using the command line arguments. For example, assuming the executable of your Vigenere CBC encipher is called V_encipher, plaintext file is called sample.txt, the key is rock and the IV is dark. The Unix command line to run the encipher would look like this:
./V_encipher sample.txt rock dark
Assuming your encipher would save the ciphertext to a file ciphertext.txt and your decipher executable is called V_decipher (the key and the IV are same as the above), the Unix command line to run the decipher would look like this:
./V_decipher ciphertext.txt rock dark
3.3. Outputs
As mentioned above, you would create two programs: one for the encipher (including the preprocessing) and one for the decipher. The outputs of the encipher program should include the following:
Original text file name
Key
IV
Block size
Plaintext (after preprocessing) printed on the screen
Number of characters in plaintext (before padding)
Ciphertext printed on the screen
Name of ciphertext file (ciphertext saved to a file)
Number of padding characters
The ciphertext file will be used as one of the inputs to the decipher. The outputs of the decipher program should include the following:
Ciphertext file name
Number of characters in ciphertext
Recovered plaintext printed on the screen
Co = E (Po + IV) = (Po + IV + keyword) mod 26 Gj = E (P, + Cj-1)-(P, + Cj-1-keyword) mod 26 Co = E (Po + IV) = (Po + IV + keyword) mod 26 Gj = E (P, + Cj-1)-(P, + Cj-1-keyword) mod 26
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


