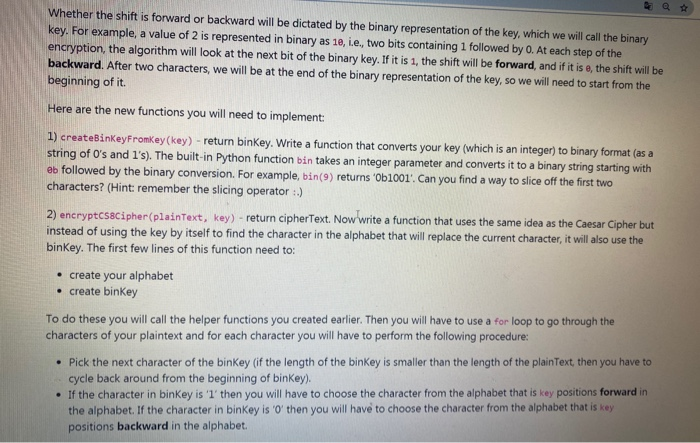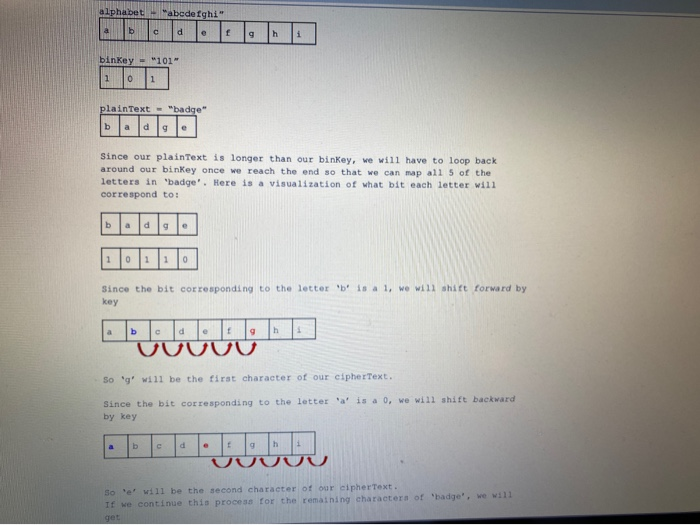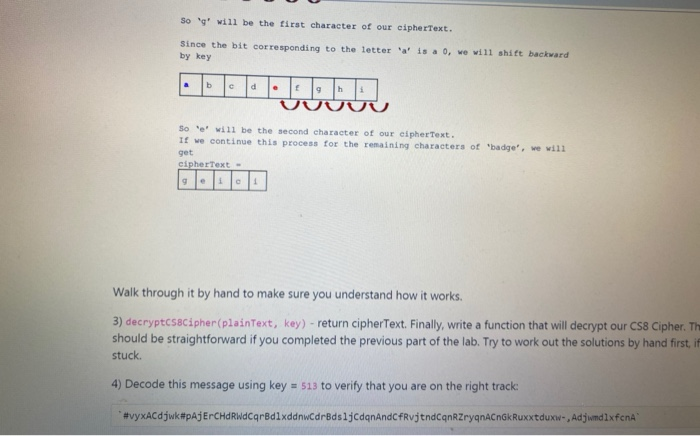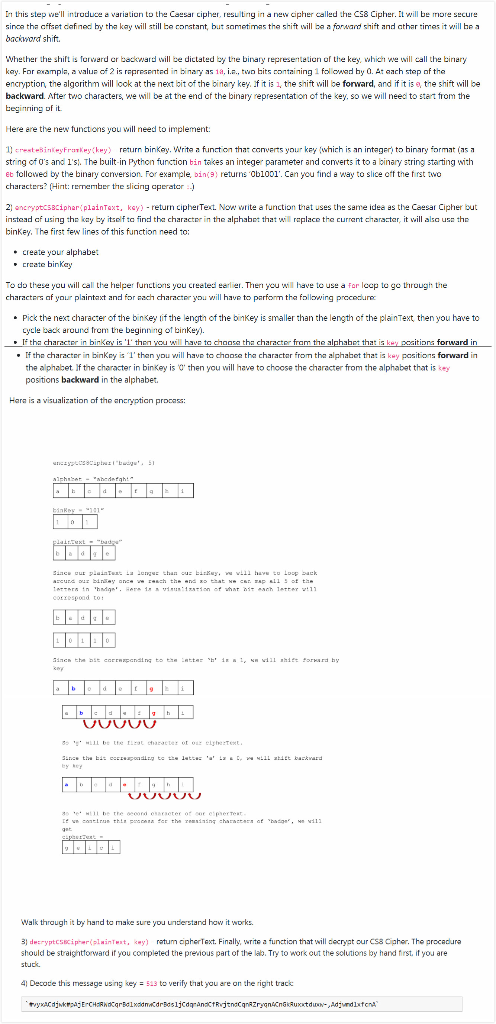
In this step we'll introduce a variation to the Causar cipher, resulting in a new cipher called the CS8Cipher. It will be more secure since the affret cafined by the key will still be constant, but sometimes the shift will be a forward shift and other times it will be a backward shift Whether the shift is forward or backward will be dictated by the binary representation of the key, which we will call the binary kay. For example, a value of 2 is represented in binary as 1a, i..., two bits containing 1 followed by . At anchtop of the encryption, the algorithm will look at the next bit of the binary keyif it is the shift will be forward, and if it is the shift will be backward. After two characters, we will be at the end of the binary representation of the key, so we will need to start from the beginning of it Here are the new functions you will need to implement: Dr inkwyrok wykwy) return binkay. Write a function that converts your key which is an integer to binary format string of 's and I's. The built-in Python function in takes an integer parameter and converts it to a binary string starting with et followed by the binary conversion. For example in returns Ob1001. Can you find a way to slice off the first two characters? (Hint: remember the slicing operator) 2 crocscipher plaintext. ksy) - return cipher Text Now write a function that uses the same idee as the Caesar Cipher but instead of using the key by itself to find the character in the alphabet that will replace the current character it will also use the binkey. The first few lines of this function need to Create your alphabet .create binKey To do these you will call the helper functions you created series. Then you will have to use a Forloop te go through the characters of your plaintext and for each character you will have to perform the following procedure Pick the next character of the binKey if the length of the bankey is smaller than the length of the plaintext, then you have to Cycle back around from the beginning of binkel the character in binkey is 'T' then you will have to choose the character from the alphabet that is key positions forward in the character in bin key is ' then you will have to choose the character from the alphabet that is kay positions forward in the alphabet if the character in binKey is then you will have to choose the character from the alphabet that is le positions backward in the alphabet Harn is a visualization of the encryption process: itu. 51 Since UE tu chan cus bawywe will have to log back w biayonce ve reach the end e Car Epal ETA EN That when ench T 11 COLOCO Since the c onding to teatteri , torby UUUUU Walk through it by hand to make sure you understand how it works. 31 decrypt (wintert, wy) rotum cipherText. Finally, write a function that will decrypt our CS8Cipher. The procedure should be straightforward if you completed the previous part of the lab. Try to work out the solutions by hand first if you are stuck 4 Decode this message using ley 13 to verify that you are on the right track WACOKE CHCarolarija Ant anaryann Auxxt , Adjudixfch Whether the shift is forward or backward will be dictated by the binary representation of the key, which we will call the binary key. For example, a value of 2 is represented in binary as ie, ie, two bits containing 1 followed by 0. At each step of the encryption, the algorithm will look at the next bit of the binary key. If it is 1, the shift will be forward, and if it is e, the shift will be backward. After two characters, we will be at the end of the binary representation of the key, so we will need to start from the beginning of it. Here are the new functions you will need to implement: 1) createBinkeyFromkey (key) - return binKey. Write a function that converts your key (which is an integer) to binary format (as a string of O's and 1's). The built-in Python function bin takes an integer parameter and converts it to a binary string starting with eb followed by the binary conversion. For example, bin(9) returns 'Ob1001. Can you find a way to slice off the first two characters? (Hint: remember the slicing operator :.) 2) encryptcsscipher(plaintext, key) - return cipherText. Now write a function that uses the same idea as the Caesar Cipher but instead of using the key by itself to find the character in the alphabet that will replace the current character, it will also use the binKey. The first few lines of this function need to: create your alphabet create binkey To do these you will call the helper functions you created earlier. Then you will have to use a for loop to go through the characters of your plaintext and for each character you will have to perform the following procedure: Pick the next character of the binKey (if the length of the binKey is smaller than the length of the plain Text, then you have to cycle back around from the beginning of binKey). If the character in binkey is I then you will have to choose the character from the alphabet that is key positions forward in the alphabet. If the character in binkey is 'O then you will have to choose the character from the alphabet that is positions backward in the alphabet. phabet Mabcdefghi plain Text "badge" Since our plain Text is longer than our binkey, we will have to loop back around our binkey once we reach the end so that we can map all 5 of the letters in "badge'. Here is a visualization of what bit each letter will correspond to: Since the bit corresponding to the letter 'b' is a 1, we will shift forward by key So 'g' will be the first character of our cipher Text Since the bit corresponding to the letter a' is a 0, we will shift backward by key Soel will be the second character of our cipher Text. If we continue this process for the remaining characters of "badge', we will So 'g' will be the first character of our cipherText. Since the bit corresponding to the letter by key is a 0, we will shift backward So I will be the second character of our cipher Text. If we continue this process for the remaining characters of badge', we will get ciphere Walk through it by hand to make sure you understand how it works. 3) decryptC58Cipher (plaintext, key) - return cipherText. Finally, write a function that will decrypt our CS8Cipher. Th should be straightforward if you completed the previous part of the lab. Try to work out the solutions by hand first.it stuck 4) Decode this message using key = 513 to verify that you are on the right track #vyxAdjwkpAjErCHORWdCardlyddwcdrBdsljcdgnAndCfRvjtndcqnZrygnacnak Ruxxtduxw, Adjwmdlxfcna In this step we'll introduce a variation to the Causar cipher, resulting in a new cipher called the CS8Cipher. It will be more secure since the affret cafined by the key will still be constant, but sometimes the shift will be a forward shift and other times it will be a backward shift Whether the shift is forward or backward will be dictated by the binary representation of the key, which we will call the binary kay. For example, a value of 2 is represented in binary as 1a, i..., two bits containing 1 followed by . At anchtop of the encryption, the algorithm will look at the next bit of the binary keyif it is the shift will be forward, and if it is the shift will be backward. After two characters, we will be at the end of the binary representation of the key, so we will need to start from the beginning of it Here are the new functions you will need to implement: Dr inkwyrok wykwy) return binkay. Write a function that converts your key which is an integer to binary format string of 's and I's. The built-in Python function in takes an integer parameter and converts it to a binary string starting with et followed by the binary conversion. For example in returns Ob1001. Can you find a way to slice off the first two characters? (Hint: remember the slicing operator) 2 crocscipher plaintext. ksy) - return cipher Text Now write a function that uses the same idee as the Caesar Cipher but instead of using the key by itself to find the character in the alphabet that will replace the current character it will also use the binkey. The first few lines of this function need to Create your alphabet .create binKey To do these you will call the helper functions you created series. Then you will have to use a Forloop te go through the characters of your plaintext and for each character you will have to perform the following procedure Pick the next character of the binKey if the length of the bankey is smaller than the length of the plaintext, then you have to Cycle back around from the beginning of binkel the character in binkey is 'T' then you will have to choose the character from the alphabet that is key positions forward in the character in bin key is ' then you will have to choose the character from the alphabet that is kay positions forward in the alphabet if the character in binKey is then you will have to choose the character from the alphabet that is le positions backward in the alphabet Harn is a visualization of the encryption process: itu. 51 Since UE tu chan cus bawywe will have to log back w biayonce ve reach the end e Car Epal ETA EN That when ench T 11 COLOCO Since the c onding to teatteri , torby UUUUU Walk through it by hand to make sure you understand how it works. 31 decrypt (wintert, wy) rotum cipherText. Finally, write a function that will decrypt our CS8Cipher. The procedure should be straightforward if you completed the previous part of the lab. Try to work out the solutions by hand first if you are stuck 4 Decode this message using ley 13 to verify that you are on the right track WACOKE CHCarolarija Ant anaryann Auxxt , Adjudixfch Whether the shift is forward or backward will be dictated by the binary representation of the key, which we will call the binary key. For example, a value of 2 is represented in binary as ie, ie, two bits containing 1 followed by 0. At each step of the encryption, the algorithm will look at the next bit of the binary key. If it is 1, the shift will be forward, and if it is e, the shift will be backward. After two characters, we will be at the end of the binary representation of the key, so we will need to start from the beginning of it. Here are the new functions you will need to implement: 1) createBinkeyFromkey (key) - return binKey. Write a function that converts your key (which is an integer) to binary format (as a string of O's and 1's). The built-in Python function bin takes an integer parameter and converts it to a binary string starting with eb followed by the binary conversion. For example, bin(9) returns 'Ob1001. Can you find a way to slice off the first two characters? (Hint: remember the slicing operator :.) 2) encryptcsscipher(plaintext, key) - return cipherText. Now write a function that uses the same idea as the Caesar Cipher but instead of using the key by itself to find the character in the alphabet that will replace the current character, it will also use the binKey. The first few lines of this function need to: create your alphabet create binkey To do these you will call the helper functions you created earlier. Then you will have to use a for loop to go through the characters of your plaintext and for each character you will have to perform the following procedure: Pick the next character of the binKey (if the length of the binKey is smaller than the length of the plain Text, then you have to cycle back around from the beginning of binKey). If the character in binkey is I then you will have to choose the character from the alphabet that is key positions forward in the alphabet. If the character in binkey is 'O then you will have to choose the character from the alphabet that is positions backward in the alphabet. phabet Mabcdefghi plain Text "badge" Since our plain Text is longer than our binkey, we will have to loop back around our binkey once we reach the end so that we can map all 5 of the letters in "badge'. Here is a visualization of what bit each letter will correspond to: Since the bit corresponding to the letter 'b' is a 1, we will shift forward by key So 'g' will be the first character of our cipher Text Since the bit corresponding to the letter a' is a 0, we will shift backward by key Soel will be the second character of our cipher Text. If we continue this process for the remaining characters of "badge', we will So 'g' will be the first character of our cipherText. Since the bit corresponding to the letter by key is a 0, we will shift backward So I will be the second character of our cipher Text. If we continue this process for the remaining characters of badge', we will get ciphere Walk through it by hand to make sure you understand how it works. 3) decryptC58Cipher (plaintext, key) - return cipherText. Finally, write a function that will decrypt our CS8Cipher. Th should be straightforward if you completed the previous part of the lab. Try to work out the solutions by hand first.it stuck 4) Decode this message using key = 513 to verify that you are on the right track #vyxAdjwkpAjErCHORWdCardlyddwcdrBdsljcdgnAndCfRvjtndcqnZrygnacnak Ruxxtduxw, Adjwmdlxfcna