Question
INFORMATION SECURITY RISK MANAGEMENT Case study 2: Information security investigation and analysis at UUniversity According to several security reports and recent published research, top cyber
INFORMATION SECURITY RISK MANAGEMENT
Case study 2: Information security investigation and analysis at UUniversity
According to several security reports and recent published research, top cyber threats to universities are malware attacks, DoS/DDos attacks, phishing attacks, activity interruption and theft of personal data or intellectual property. In addition, information assets that is of interest for attackers are intellectual property for particular courses and projects as well as research data and results. Personal data of students, including dissertation materials, E-xam results and course grades. Personal data carries high sensitivity due to its link to university reputation and trust. Intellectual property is also of high value as it represents the university competitive advantage and relates to its daily operations.
Looking at UUniversitys information technology context, its web site and e-registration system are hosted on local web servers. This allows UUniversity provide several online services to its students and employees, which include personal data, academic situation, learning resources and study schedule. UUniversity is utilizing cloud services intensively in its activities to minimize equipment and maintenance costs also to provide virtual laboratories and simulation environments to support practical activities. Access to all these online services is based on credentials offering access privileges to online users. Accordingly, credentials issuance, verification and utilization needs careful attention especially for new enrolled students or staff. Also, detailed bounds of cloud service provisioning needs to be considered.
Network administrators at UUniversity utilize Remote Desktop Protocol (RDP), which provides a graphical user interface for remote access connections over the network. This represents a new threat vector of gaining unauthorized access over the network to university assets. In addition, UUniversity increased its dependability on third party applications and software to fulfill teaching requirements. More network accessibility services are offered to UUniversity staff and students, allowing them to bring and connect their own devices to university network without device vulnerability scanning. This will increase the sources of malwares which might be used for unauthorized access to personal and sensitive information. Malwares might also be installed on network connectivity devices, such as switches and routers overwhelming the network and depleting its resources distracting or cutting the access to UUniversity web servers might be distracted.
UUniversity is implementing a defense control strategy in which its running network-level firewalls and network-level antivirus to secure its networking environments from possible threats and attacks. Also, UUniversity employs a Network Access Control (NAC) system to provide access rights to legitimate users only.
Q1) you have been appointed as the new InfoSec Risk manager at UUniversity. You are asked to deliver a detailed risk assessment report to the CISO, to help him understand UUniversitys current Risk situation. Your report should consist of the following working sheets, lists and justifications:
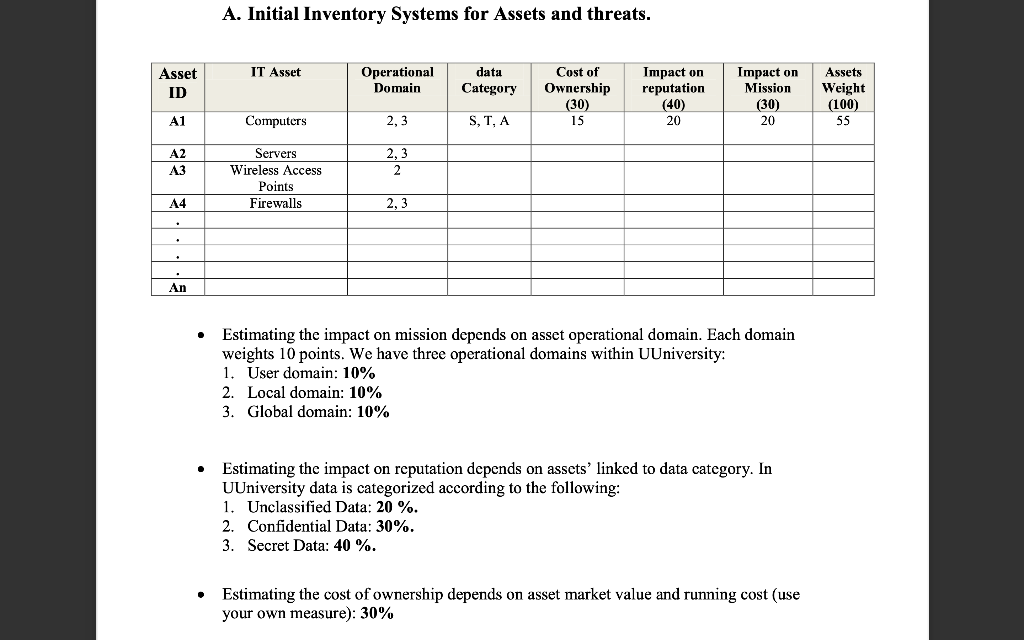
A. Initial Inventory Systems for Assets and threats
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


