Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Inspect the email below. Do you think it's real or a phish? Answer with elaborating on the following two questions: 1. Why do you
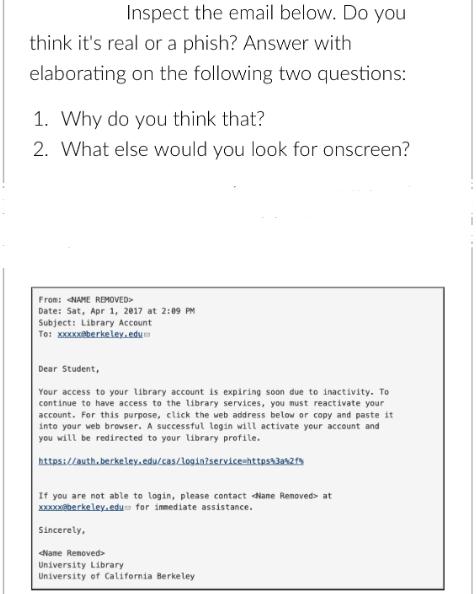
Inspect the email below. Do you think it's real or a phish? Answer with elaborating on the following two questions: 1. Why do you think that? 2. What else would you look for onscreen? From: NAME REMOVED> Date: Sat, Apr 1, 2017 at 2:09 PM Subject: Library Account To: xxxxx@berkeley.edu Dear Student, Your access to your library account is expiring soon due to inactivity. To continue to have access to the library services, you must reactivate your account. For this purpose, click the web address below or copy and paste it into your web browser. A successful login will activate your account and you will be redirected to your library profile. https://auth.berkeley.edu/cas/login?service=https%3a%2f If you are not able to login, please contact Name Renoved> at xxxxx@berkeley.edu for immediate assistance. Sincerely, < University Library University of California Berkeley
Step by Step Solution
★★★★★
3.36 Rating (152 Votes )
There are 3 Steps involved in it
Step: 1
Step 1 Review the Senders Email Address Examine the senders email address In this case its mentioned as AME REMOVED Explanation Legitimate institutions usually have official and recognizable domain names for their email addresses The use of an ambiguous or unusual email address can be a red flag Step 2 Check the URL in the Email Look at the URL provided in the email In this case its httpsauthberkeleyeducasloginservicehtt32 Explanation Hover your mouse pointer over the link without clicking it to view the actual URL it leads to Legitimate organizations should have URLs that match their official domain In this case authberkeleyedu may seem legitimate but the servicehtt32 portion is suspicious and does not appear to be a standard login URL Step 3 Evaluate the Language and Tone Analyze the language used in the email This email contains phrases like Your access is expiring soon due to inactivity and immediate assistance Explanation Phishing emails often use urgent or threatening language to create a sense of urgency pressuring recipients into taking immediate action without thinking Step 4 Examine the Request for Information Note that the email is asking you to click a link and enter your login information Explanation Legitimate organizations especially libraries or universities typically do not request sensitive information such as login credentials via email This is a common tactic used in phishing attempts Step 5 Look for Personalization Observe how the email begins with a generic greeting Dear Student without addressing you by your name Explanation Legitimate institutions usually have your personal information and would address you by name in their communications Generic greetings are a common sign of phishing Step 6 Verify the Senders Authenticity If you suspect an emails legitimacy verify the senders authenticity In this case contact the library or institution ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


