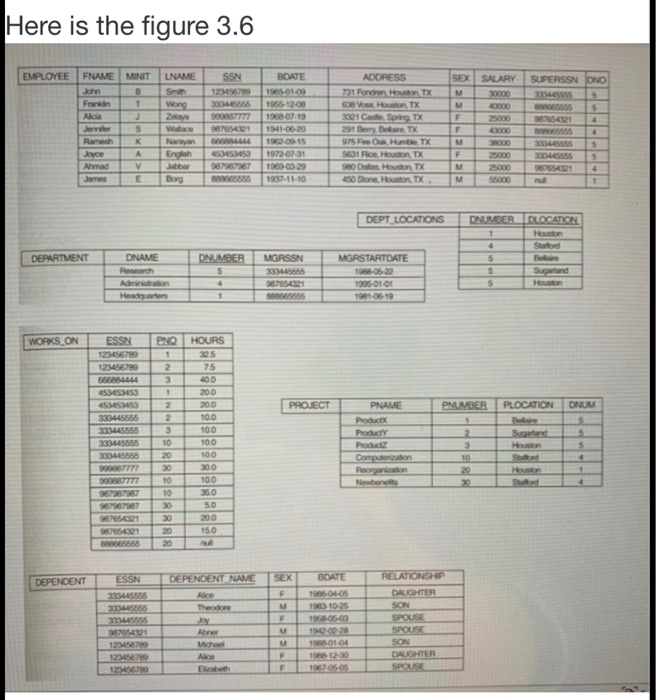
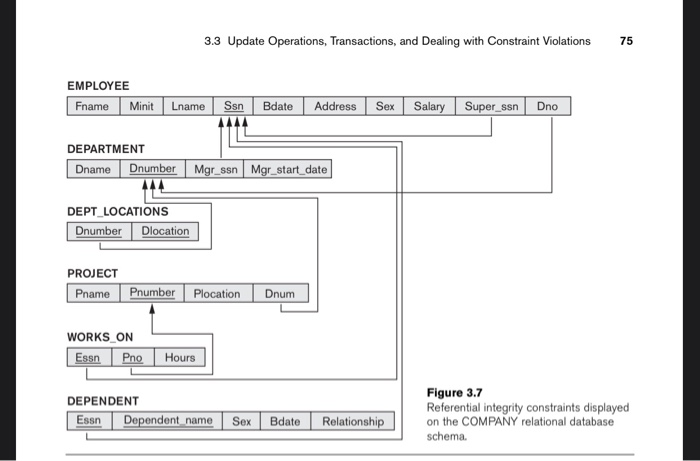
INSTRUCTION ON HOW TO SUBMIT YOUR ASSIGNMENT: 1. Submit a typed paper version of your assignment. 2. Your assignment will be graded based on its documentation, readability, correctness, and simplicity. 1. PROBLEMS: 1. (50 pts = 5 x 10 pts) Consider that the update operations below are applied to the COMPANY relational database schema (Figure 3.7 on p. 75 of the textbook "Fundamentals of Database Systems," 6th Edition) 1 Insert into EMPLOYEE. 2 Insert into EMPLOYEE. 3 Insert into PROJECT. 4 Delete the WORKS ON tuples with Essn = '333445555'. 5 Modify the Mgrssn and Mgrstartdate of the DEPARTMENT tuple with Dnumber = 4 to 123456788' and 2007-10-01', respectively. For each operation, write down (1) EACH of the four integrity constraint violated by the operation (op), if any, and (2) ALL possible different ways, also called actions (Reject, Change the op, Set Default; Set Null, and RECALL: The 4 integrity constraints (ICs) are: Domain constraint, Key constraint, Entity IC, and Referential IC Assignment 3 CS 411-01 Cascade") of enforcing each of the violated constraint. For example, say, if you have one violated (referential integrity) constraint, you write down at maximum, the 5 different actions applying to this violation, explaining how each action is to be applied to this violation i.e., at maximum. 5 explanations, totally) For another example, say, if you have two violated referential integrity) constraints, you write down at maximum, the 4 different actions applying to each of the 2 violations, explaining how each action is to be applied to the respective violation (ie, at maximum. 2 violations possible actions each - 10 explanations, totally). Etc., for three violated constraints, and so on. Notice that there are four relational constraints in the relational data model: domain constraint, key constraint, entity integrity constraint, referential integrity constraint. For each operation, you need to check for violation of each of the four constraints (not all of the constraints will be violated, just some of them but you need to check all of them to be sure which ones are violated, if any, otherwise you may overlook for some of the violations). For that, you need also to use the COMPANY database state in Figure 3.6 on P. 72 of the Elmasri's textbook; this Figure 3.6 is also shown in the lecture notes] (For the format of answering this question, you need to look in the examples of violations of constraints on p. 76, 77, and 78 in the Elmasri's textbook (6/E) and answer here in THE SAME manner and format. Also you may consult the Ch. 3 lecture moles, pages 15-17] 2. (23 pts - 8 pts PKs & 5x 3 - 15 pts FKs) Consider the following six relations for an order processing database application in a company: CUSTOMER (Custt, Cname, City) ORDER (Order!, Odate, Cust!, Ord Ant ORDER ITEN (Ordert. ItenOty) ITEM (Itemt. Unit price) SHIPMENT (Ordert, Warehouse, Ship date) WAREHOUSE (Warehouset, City) Here, Ord Amt refers to total dollar amount of an order; Odate is the date the order was placed Ship date is the date an order is shipped from the warehouse. Assume that an order can be shipped from several warehouses. a. (8 points) Underline the primary keys in each relation. b. (15 points) Specify foreign kos for this schema, stating any assumptions you make. To do this, use the notation SHOWN in the following example: ORDER.Custno CUSTOMER (Here, Custno in the ORDER relation is a foreign key and it refers IMPLICITLY to the primary key Custno in the CUSTOMER relation). 3. (8 points) Write down short answer to the following: 2 When you implement a DB (say COMPANY DB) in SQL you MUST choose only one of these actions for eachik at maximum. since some constraints, when violated, can NOT be fixed with 5 alternative actions, but only with 1 or 2, for example--the entity integrity constraint violation Here is the figure 3.6 EMPLOYEE FNAME MENIT LAMEISSN BOATE ADORESS SUPERSSN ONO SALARY 1000 000 SSS 1985-12-08 01-00 15 1972-0731 1980-0339 RODH SO Shone Houston, TX DEPT LOCATIONS ONUNDER DEPARTMENT DNUMBER IVGRSSN MGRSTARTDATE 1905-01-01 WORKS ON ESSNENO HOURS 1234 12149 400 75 200 PNAVE PNUMBER PLOCATION 200 100 445555 US Sugar 100 100 100 350 ESSNDEPENDENT NAME SEX BOATE RELATIONSHIP DEPENDENT 304 OL-05 11025 18-05-03 DATORER SON SPOUSE SPOUSE SON DAUGHTER SPOUSE WOW 01-04 3.3 Update Operations, Transactions, and Dealing with Constraint Violations 75 EMPLOYEE Frame Minit Lname Bdate Address Sex Salary Super_ssn Dno Ssn TIL DEPARTMENT Dname | Dnumber Mgr_ssn Mgr_start_date DEPT_LOCATIONS Dnumber Dlocation PROJECT Pname Pnumber Plocation Dnum WORKS ON Essn Pro Hours DEPENDENT Essn Dependent name Sex Bdate Figure 3.7 Referential integrity constraints displayed on the COMPANY relational database schema Relationship