Question
The IT Department at Citywide Community College developed a computer security incident response plan that requires users to provide information for each security incident. Louis
The IT Department at Citywide Community College developed a computer security incident response plan that requires users to provide information for each security incident. Louis Hermann, the IT manager, inventoried the major components of the college’s computer systems and created a spreadsheet to track the equipment by manufacturer, model number, and serial number. He decided to confine the list to major computer components, and he does not try to track keyboards, mice, and so forth. Louis then created a spreadsheet to track systems security incident facts including information about the department reporting the incident, target-specific information (host machine name, etc.), source-specific information (source IP address), and information about the type of security incident or attack. Louis has asked you to use the data provided in the CCC Security spreadsheet, Ch10Ex01, to identify (1) the department reporting the highest number of security incidents and (2) the most prevalent type of intrusion. Use the “countif” function to count the number of security incidents in which the computer system was compromised. Use a memo format to submit a summary of your findings to Louis.
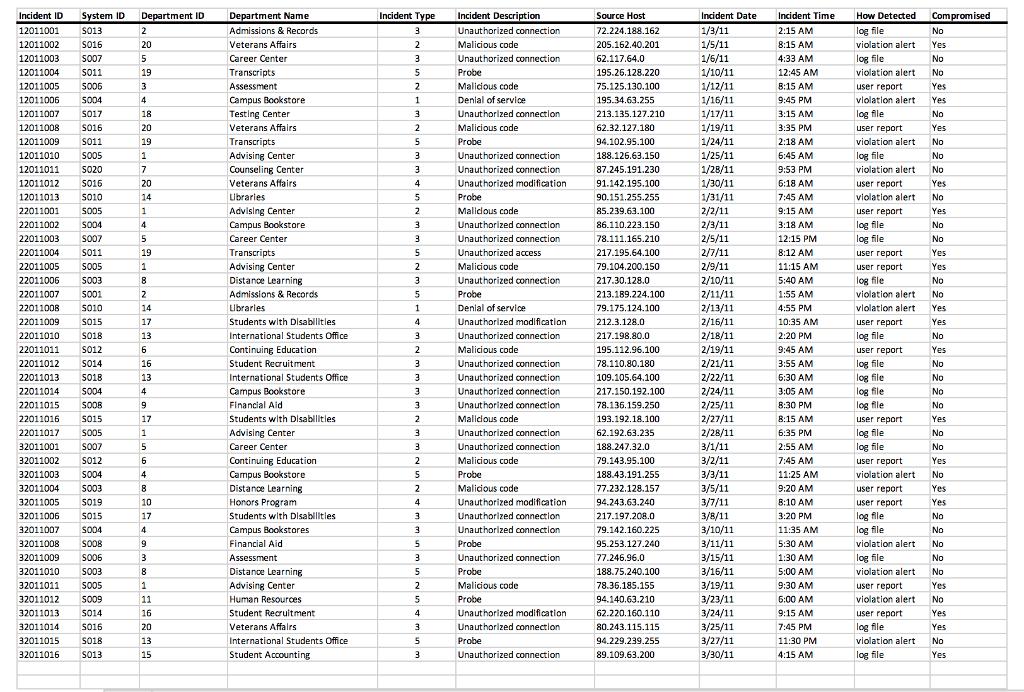
Incident ID System ID Department ID 12011001 S013 12011002 S016 12011003 S007 12011004 S011 12011005 S006 12011006 5004 12011007 S017 12011008 S016 12011009 S011 12011010 SO05 12011011 S020 12011012 S016 12011013 S010 22011001 S005 22011002 5004 22011003 S007 22011004 S011 22011005 S005 22011006 S003 22011007 5001 22011008 22011009 S010 S015 22011010 S018 22011011 S012 22011012 S014 22011013 S018 22011014 S004 22011015 S008 22011016 22011017 32011001 S015 S005 S007 SO12 32011002 5004 32011003 32011004 S003 32011005 S019 32011006 S015 32011007 S004 32011008 S008 32011009 S006 32011010 S003 32011011 5005 32011012 5009 32011013 S014 32011014 S016 32011015 S018 32011016 S013 2 20 5 19 3 4 18 20 19 1 7 20 14 1 4 5 19 1 8 2 14 17 13 6 16 13 4 9 17 1 5 6 4 8 10 17 4 9 3 8 1 11 16 20 13 15 Department Name Admissions & Records Veterans Affairs Career Center Transcripts Assessment Campus Bookstore Testing Center Veterans Affairs Transcripts Advising Center Counseling Center Veterans Affairs Libraries Advising Center Campus Bookstore Career Center Transcripts Advising Center Distance Learning Admissions & Records. Libraries Students with Disabilities. International Students Office Continuing Education Student Recruitment International Students Office Campus Bookstore Financial Aid Students with Disabilities. Advising Center Career Center Continuing Education Campus Bookstore Distance Learning Honors Program Students with Disabilities Campus Bookstores Financial Aid Assessment Distance Learning Advising Center Human Resources Student Recruitment Veterans Affairs International Students Office Student Accounting Incident Type 3 2 3 5 2 1 3 2 5 3 3 4 5 2 3 3 5 2 3 5 1 4 3 2 3 3 3 3 2 3 3 2 5 2 4 3 3 5 3 5 2 5 4 3. 5 3 Incident Description Unauthorized connection Malicious code Unauthorized connection Probe Malicious code Denial of service Unauthorized connection Malicious code Probe Unauthorized connection Unauthorized connection Unauthorized modification Probe Malidous code Unauthorized connection. Unauthorized connection Unauthorized access Malicious code Unauthorized connection Probe Denial of service Unauthorized modification. Unauthorized connection Malicious code Unauthorized connection Unauthorized connection. Unauthorized connection Unauthorized connection Malicious code Unauthorized connection Unauthorized connection Malicious code Probe Malicious code Unauthorized modification. Unauthorized connection. Unauthorized connection Probe Unauthorized connection Probe Malicious code Probe Unauthorized modification Unauthorized connection Probe Unauthorized connection Source Host 72.224.188.162 205.162.40.201 62.117.64.0 195.26.128.220 75.125.130.100 195.34.63.255 213.135.127.210 62.32.127.180 94.102.95.100 188.126.63.150 87.245.191.230 91.142.195.100 90.151.255.255 85.239.63.100 86.110.223.150 78.111.165.210 217.195.64.100 79.104.200.150 217.30.128.0 213.189.224.100 79.175.124.100 212.3.128.0 217.198.80.0 195.112.96.100 78.110.80.180 109.105.64.100 217.150.192.100 78.136.159.250 193.192.18.100 62.192.63.235 188.247.32.0 79.143.95.100 188.43.191.255 77.232.128.157 94.243.63.240 217.197.208.0 79.142.160.225 95.253.127.240 77.246.96.0 188.75.240.100 78.36.185.155 94.140.63.210 62.220.160.110 80.243.115.115. 94.229.239.255 89.109.63.200 Incident Date 1/3/11 1/5/11 1/6/11 1/10/11 1/12/11 1/16/11 1/17/11 1/19/11 1/24/11 1/25/11 1/28/11 1/30/11 1/31/11 2/2/11 2/3/11 2/5/11 2/7/11 2/9/11 2/10/11 2/11/11 2/13/11 2/16/11 2/18/11 2/19/11 2/21/11 2/22/11 2/24/11 2/25/11 2/27/11 2/28/11 3/1/11 3/2/11 3/3/11 3/5/11 3/7/11 3/8/11 3/10/11 3/11/11 3/15/11 3/16/11 3/19/11 3/23/11 3/24/11 3/25/11 3/27/11 3/30/11 Incident Time 2:15 AM 8:15 AM 4:33 AM 12:45 AM 8:15 AM 9:45 PM 3:15 AM 3:35 PM 2:18 AM 6:45 AM 9:53 PM 6:18 AM 7:45 AM 9:15 AM 3:18 AM 12:15 PM 8:12 AM 11:15 AM 5:40 AM 1:55 AM 4:55 PM 10:35 AM 2:20 PM 9:45 AM 3:55 AM 6:30 AM 3:05 AM 8:30 PM 8:15 AM 6:35 PM 2:55 AM 7:45 AM 11:25 AM 9:20 AM 8:10 AM 3:20 PM 11:35 AM 5:30 AM 1:30 AM 5:00 AM 9:30 AM 6:00 AM 9:15 AM 7:45 PM 11:30 PM 4:15 AM How Detected log file violation alert log file violation alert user report violation alert log file user report violation alert log file violation alert user report violation alert user report log file log file user report user report log file violation alert violation alert user report log file user report. log file log file log file log file user report log file log file user report violation alert user report user report log file log file violation alert log file violation alert user report violation alert user report log fille violation alert log file Compromised No Yes No No Yes Yes No Yes No No No Yes No Yes No No Yes Yes No No Yes Yes No Yes No No No No Yes No No Yes No Yes Yes No No No No No Yes No Yes Yes No Yes
Step by Step Solution
3.53 Rating (160 Votes )
There are 3 Steps involved in it
Step: 1
MEMO To Louis Hermann IT Manager From Your Name Date Date Subject Summary of Security Incidents Anal...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


