Question: ith Computer Networking Wireshark Lab: Getting Started Computor Noiwortng A Top down Approact scitorn. Version: 2.0 C 2007 J.F. Kurose, K.W Ross. All Rights Reserved

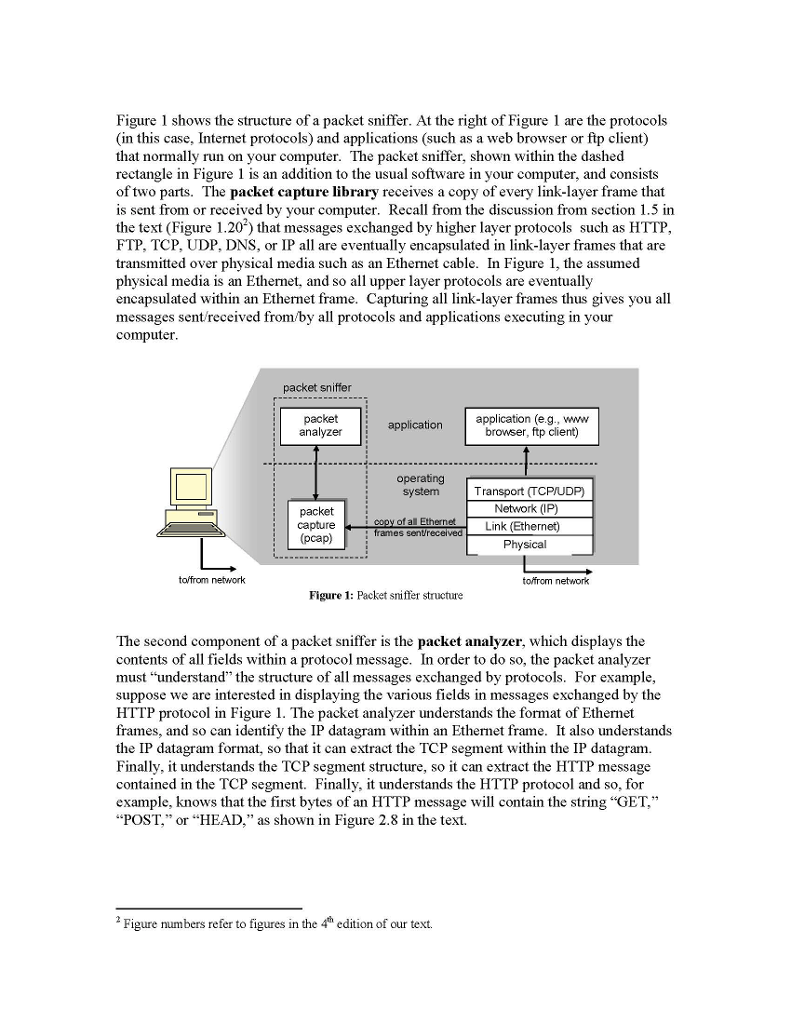



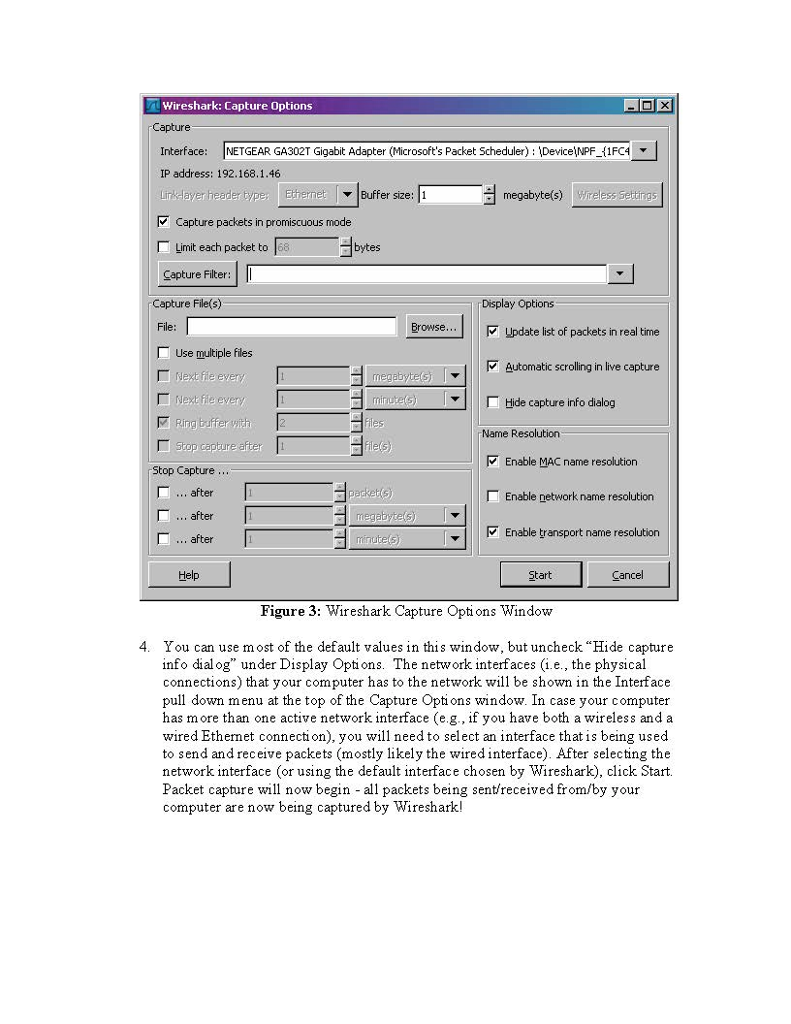
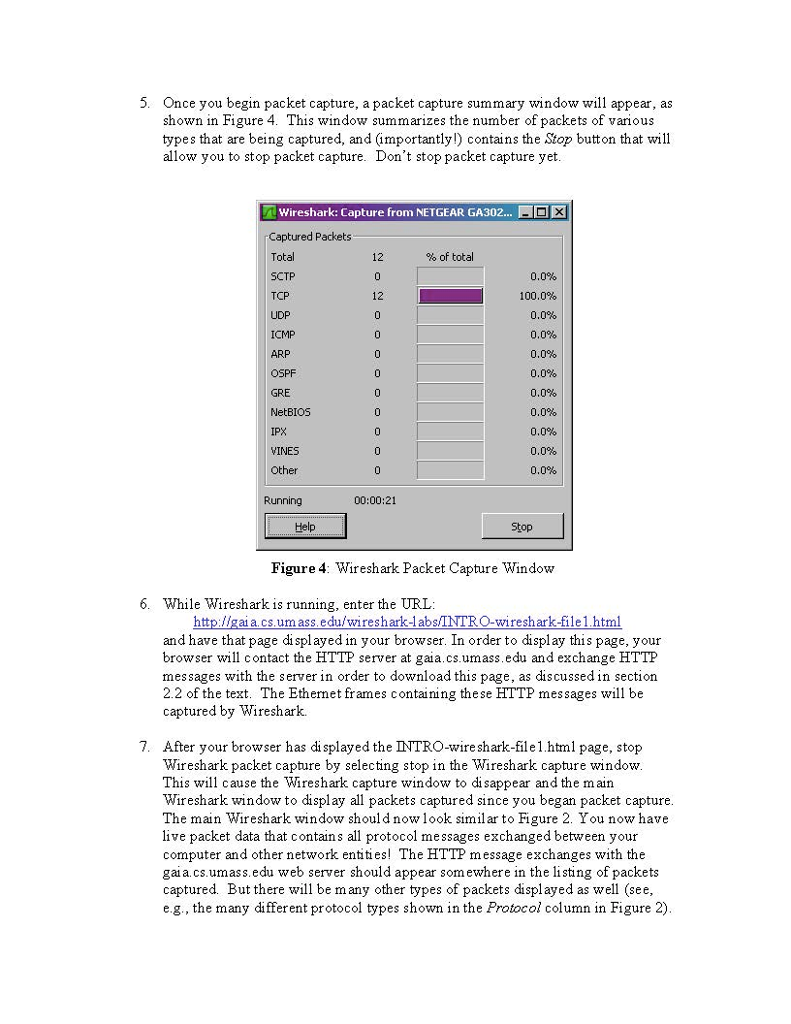

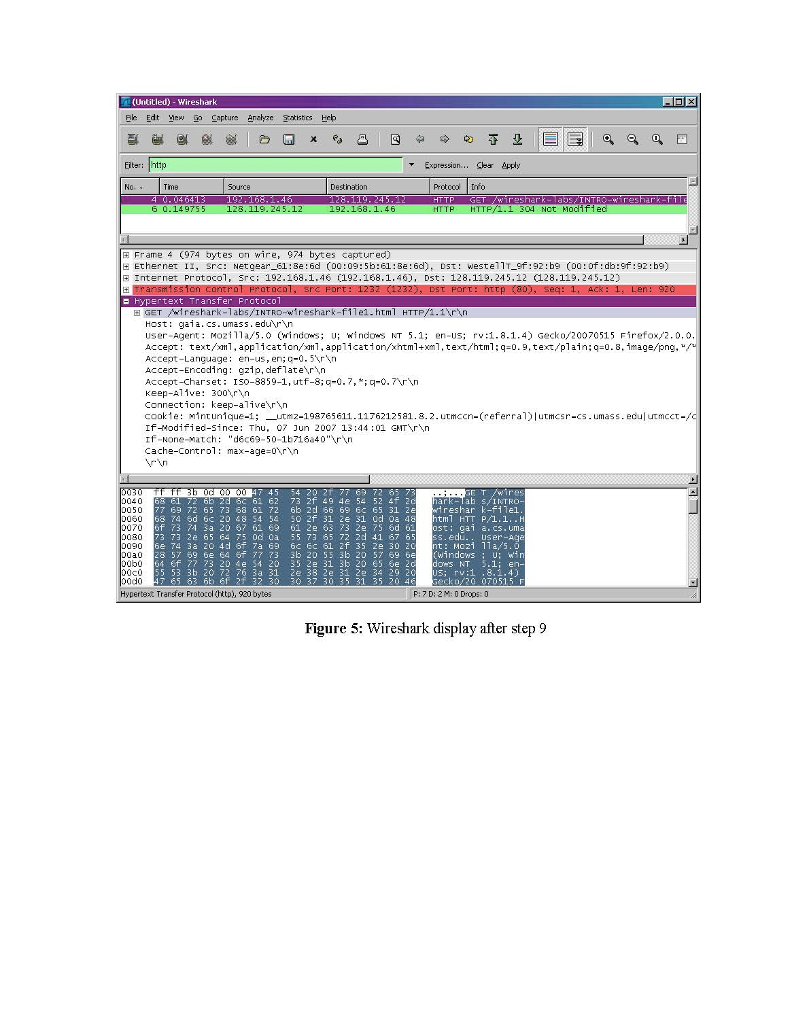

ith Computer Networking Wireshark Lab: Getting Started Computor Noiwortng A Top down Approact scitorn. Version: 2.0 C 2007 J.F. Kurose, K.W Ross. All Rights Reserved "Tell me and Iforget. Show me and Iremember. Involve me and Iunderstand." Chinese proverb One's understanding of network protocols can often be greatly deepened by "seeing protocols in action" and by "playing around with protocols" - observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. This can be done in simulated scenarios or in a "real" network environment such as the Internet. The Java applets that accompany this text take the first approach. In these Wireshark labs', we'll take the latter approach. You'll be ruing various network applications in different scenarios using a computer on your desk, at home, or in a lab. You'll observe the network protocols in your computer in action" interacting and exchanging messages with protocol entities executing elsewhere in the Intemet. Thus, you and your computer will be an integral part of these "live" labs. You'll observe, and you'l1 learn, by doing The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures ("sniffs") messages being sent received from/by your computer, it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sni ffer receives a copy of packets that are sent received fron/by application and protocols executing on your Imachine Earlier versions of these labs used the Ethereal packet analyzer. In May 2006, the developer of Ethereal oined a new compairy, nctwork protocol analyzcr, a sucsor to EthcrcalB. Since Ethcrcal is no longer being activcly maintained or developed, we have ths switched these labs over to Wireshark with the 4 edition of our text and had to leave the Ethereal& trademarks behind. He then created the Wireshardk ith Computer Networking Wireshark Lab: Getting Started Computor Noiwortng A Top down Approact scitorn. Version: 2.0 C 2007 J.F. Kurose, K.W Ross. All Rights Reserved "Tell me and Iforget. Show me and Iremember. Involve me and Iunderstand." Chinese proverb One's understanding of network protocols can often be greatly deepened by "seeing protocols in action" and by "playing around with protocols" - observing the sequence of messages exchanged between two protocol entities, delving down into the details of protocol operation, and causing protocols to perform certain actions and then observing these actions and their consequences. This can be done in simulated scenarios or in a "real" network environment such as the Internet. The Java applets that accompany this text take the first approach. In these Wireshark labs', we'll take the latter approach. You'll be ruing various network applications in different scenarios using a computer on your desk, at home, or in a lab. You'll observe the network protocols in your computer in action" interacting and exchanging messages with protocol entities executing elsewhere in the Intemet. Thus, you and your computer will be an integral part of these "live" labs. You'll observe, and you'l1 learn, by doing The basic tool for observing the messages exchanged between executing protocol entities is called a packet sniffer. As the name suggests, a packet sniffer captures ("sniffs") messages being sent received from/by your computer, it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself. Similarly, received packets are never explicitly addressed to the packet sniffer. Instead, a packet sni ffer receives a copy of packets that are sent received fron/by application and protocols executing on your Imachine Earlier versions of these labs used the Ethereal packet analyzer. In May 2006, the developer of Ethereal oined a new compairy, nctwork protocol analyzcr, a sucsor to EthcrcalB. Since Ethcrcal is no longer being activcly maintained or developed, we have ths switched these labs over to Wireshark with the 4 edition of our text and had to leave the Ethereal& trademarks behind. He then created the Wireshardk
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


