Question: Learn about the Oracle database security model Learn about backup/recovery for Oracle Databases Steps: Answer the following questions about an Oracle Database. Make sure you
Learn about the Oracle database security model
- Learn about backup/recovery for Oracle Databases
Steps:
Answer the following questions about an Oracle Database. Make sure you cite any references you use:
How does an Oracle Database use read locks and write locks?
What, if any, levels of transaction isolation are available in an Oracle Database?
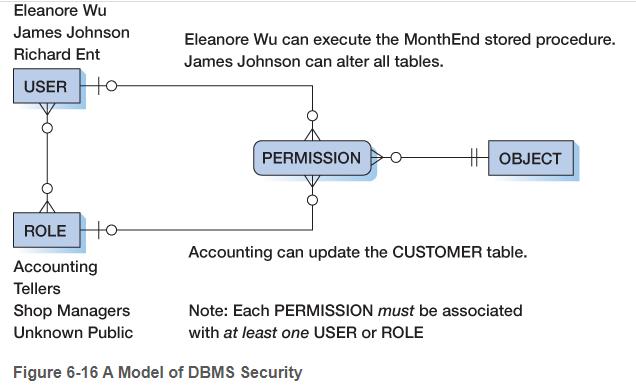
How does the security model for Oracle Database differ from that shown below:
- Summarize the backup capabilities of an Oracle Database.
Summarize the recovery capabilities of an Oracle Database.
Eleanore Wu James Johnson Richard Ent USER to to ROLE Accounting Tellers Shop Managers Unknown Public Eleanore Wu can execute the Month End stored procedure. James Johnson can alter all tables. PERMISSION OBJECT Accounting can update the CUSTOMER table. Note: Each PERMISSION must be associated with at least one USER or ROLE Figure 6-16 A Model of DBMS Security
Step by Step Solution
3.51 Rating (151 Votes )
There are 3 Steps involved in it
How does an Oracle Database use read locks and write locks In Oracle Databases locking is primarily used to ensure data integrity and concurrency control ... View full answer

Get step-by-step solutions from verified subject matter experts


