Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Let the encrypt function of standard DES be C = E(P, K) where C is the ciphertext, P is the plaintext, and K is
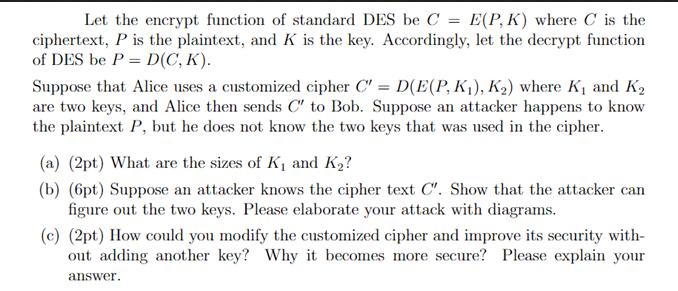
Let the encrypt function of standard DES be C = E(P, K) where C is the ciphertext, P is the plaintext, and K is the key. Accordingly, let the decrypt function of DES be P = D(C, K). Suppose that Alice uses a customized cipher C" = D(E(P, K), K) where K and K are two keys, and Alice then sends C" to Bob. Suppose an attacker happens to know the plaintext P, but he does not know the two keys that was used in the cipher. (a) (2pt) What are the sizes of K and K? (b) (6pt) Suppose an attacker knows the cipher text C'. Show that the attacker can figure out the two keys. Please elaborate your attack with diagrams. (c) (2pt) How could you modify the customized cipher and improve its security with- out adding another key? Why it becomes more secure? Please explain your answer.
Step by Step Solution
There are 3 Steps involved in it
Step: 1
a Sizes of K and K The sizes of K and K are both the same as the block size of the DES algorithm DES ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


