Question: Let's examine the 32-bit hexadecimal value Oxacfe2b7a a) Provide the binary representation of this number in little endian format. Please label and number the

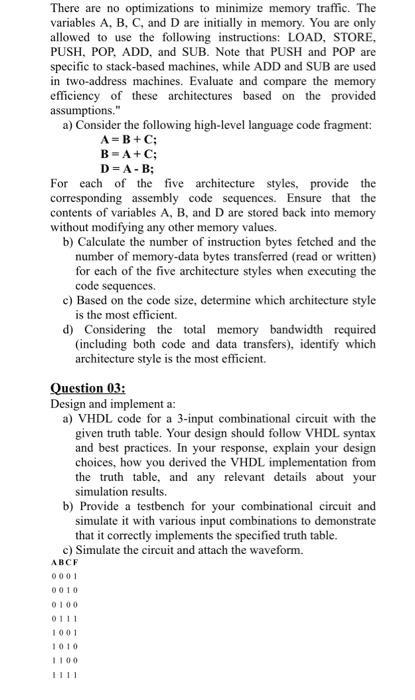
Let's examine the 32-bit hexadecimal value Oxacfe2b7a a) Provide the binary representation of this number in little endian format. Please label and number the bytes, starting from the lowest (0) to the highest (3). b) Share the binary representation of this number in big endian format. Once again, indicate the bytes by numbering them, beginning with the lowest (0) and ending with the highest (3)." Question 02: Investigate and compare the memory efficiency of five distinct instruction set architectures when executing the provided code sequence. Each architecture has a different approach to memory usage: a) Zero-Address Machine (Stack-Based): This architecture relies on a stack for all operations. It supports PUSH (to push values from memory onto the stack), POP (to pop values from the stack and store them in memory), and binary operations (OP) that work on stack values without storing intermediate results back to memory. b) One-Address Machine (Accumulator-Based): In this architecture, an accumulator is used for computations. It supports LOAD (to load values from memory into the accumulator), STORE (to store the accumulator value in memory), and binary operations (OP) that operate between memory and the accumulator. c) Two-Address Machine: This architecture accepts two operands, performs an operation, and stores the result back into one of the source operands. It supports binary operations (OP) between two memory locations. d) Three-Address Machine (Memory-Memory): This variant of the three-address machine allows operations between three memory locations. It supports binary operations (OP) that take values from two memory locations, perform the operation, and store the result in a third memory location. e) Three-Address Load-Store Machine: In this three- address architecture, operations are performed between registers. Values are loaded into registers from memory. and results are stored back into registers. It supports binary operations (OP) between registers and LOAD/STORE operations to move data between registers and memory. To evaluate memory efficiency, make these assumptions for all architectures: Opcode size: 1 byte (8 bits) Register operand size: 1 byte (8 bits) Memory address size: 2 bytes (16 bits) Data value size: 4 bytes (32 bits) All instructions have integral lengths in bytes There are no optimizations to minimize memory traffic. The variables A, B, C, and D are initially in memory. You are only allowed to use the following instructions: LOAD, STORE, PUSH, POP, ADD, and SUB. Note that PUSH and POP are specific to stack-based machines, while ADD and SUB are used in two-address machines. Evaluate and compare the memory efficiency of these architectures based on the provided assumptions." a) Consider the following high-level language code fragment: A=B+C; B=A+C; D=A-B; For each of the five architecture styles, provide the corresponding assembly code sequences. Ensure that the contents of variables A, B, and D are stored back into memory without modifying any other memory values. b) Calculate the number of instruction bytes fetched and the number of memory-data bytes transferred (read or written) for each of the five architecture styles when executing the code sequences. c) Based on the code size, determine which architecture style is the most efficient. d) Considering the total memory bandwidth required (including both code and data transfers), identify which architecture style is the most efficient. Question 03: Design and implement a: a) VHDL code for a 3-input combinational circuit with the given truth table. Your design should follow VHDL syntax and best practices. In your response, explain your design choices, how you derived the VHDL implementation from the truth table, and any relevant details about your simulation results. b) Provide a testbench for your combinational circuit and simulate it with various input combinations to demonstrate that it correctly implements the specified truth table. c) Simulate the circuit and attach the waveform. ABCF 0001 0010 0100 0111 1001 1010
Step by Step Solution
3.53 Rating (153 Votes )
There are 3 Steps involved in it
a The binary representation of the 32bit hexadecimal value 0xacfe2b7a in littleendian format ... View full answer

Get step-by-step solutions from verified subject matter experts


