Question
Managing Systems Support and Security Before You Begin - Assignment Specific Your supervisor, Carlie Davis, needs to present management with the total cost of your
Managing Systems Support and Security Before You Begin - Assignment Specific Your supervisor, Carlie Davis, needs to present management with the total cost of your in-house developed SIM system. While developing this budget, you will account for maintenance costs, backup and recovery, and the system's total cost of ownership (TCO). Furthermore, you will outline the security risks for this system. To complete these tasks, you will use the emails, libraries, and your own research. Complete the following: 1. Make a plan for system maintenance including a recommendation to maintain the system using in-house resources or to outsource it including pros and cons of both types of maintenance. 2. Detail the Physical, Network, Application, File, User, and Procedural security risks for the new system. 3. Decide on and justify the system backup method to be used. 4. Calculate the cost feasibility for this new system given the security, training, and maintenance costs, assuming that the system will be developed in-house. ? Assess the system's TCO for the next 5 years.
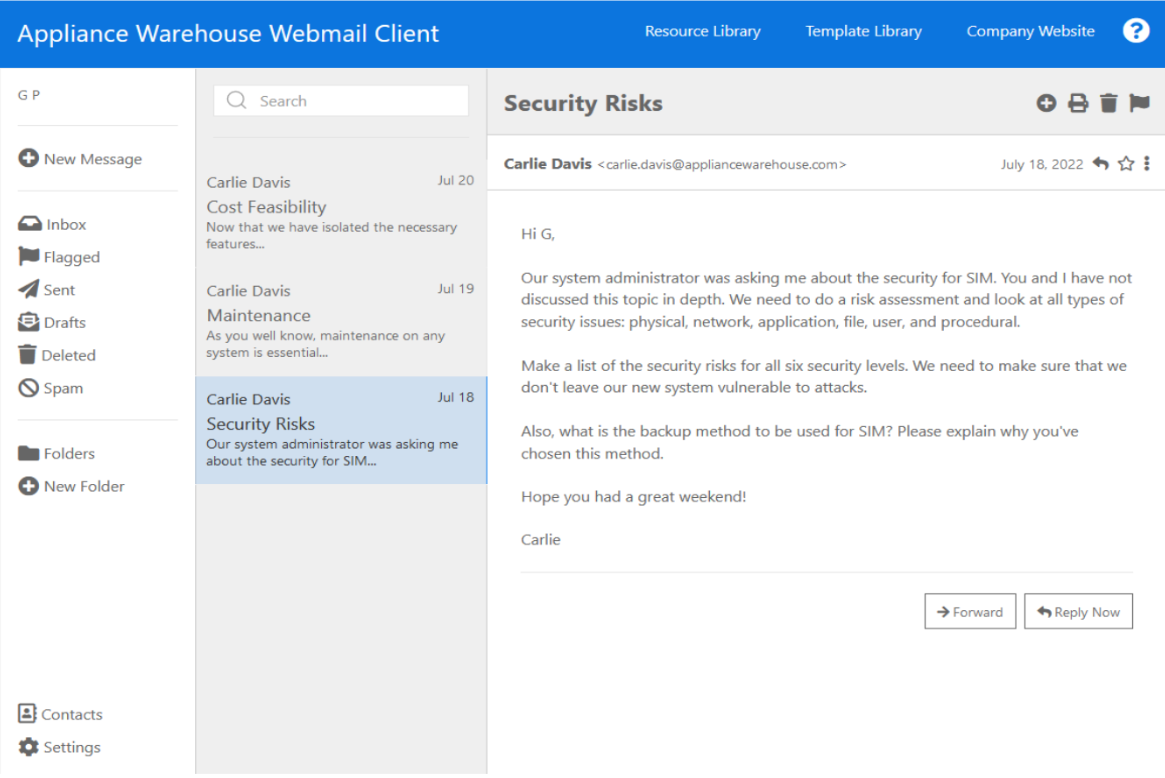
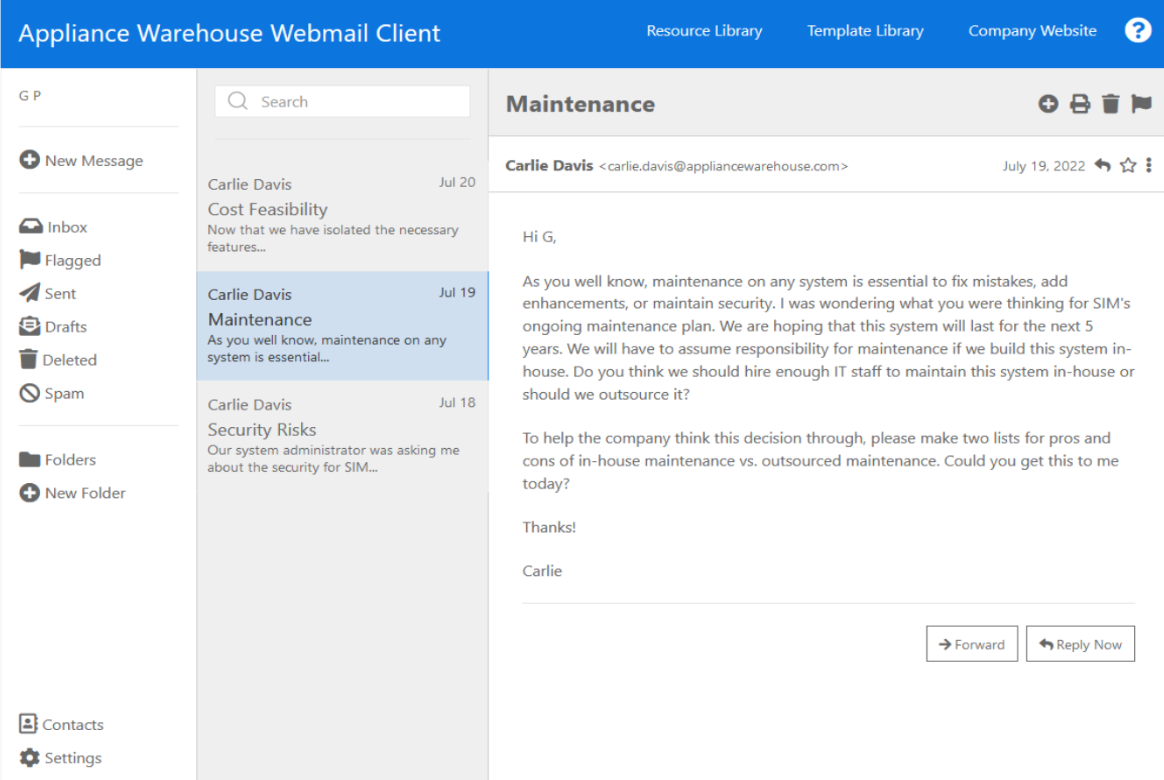
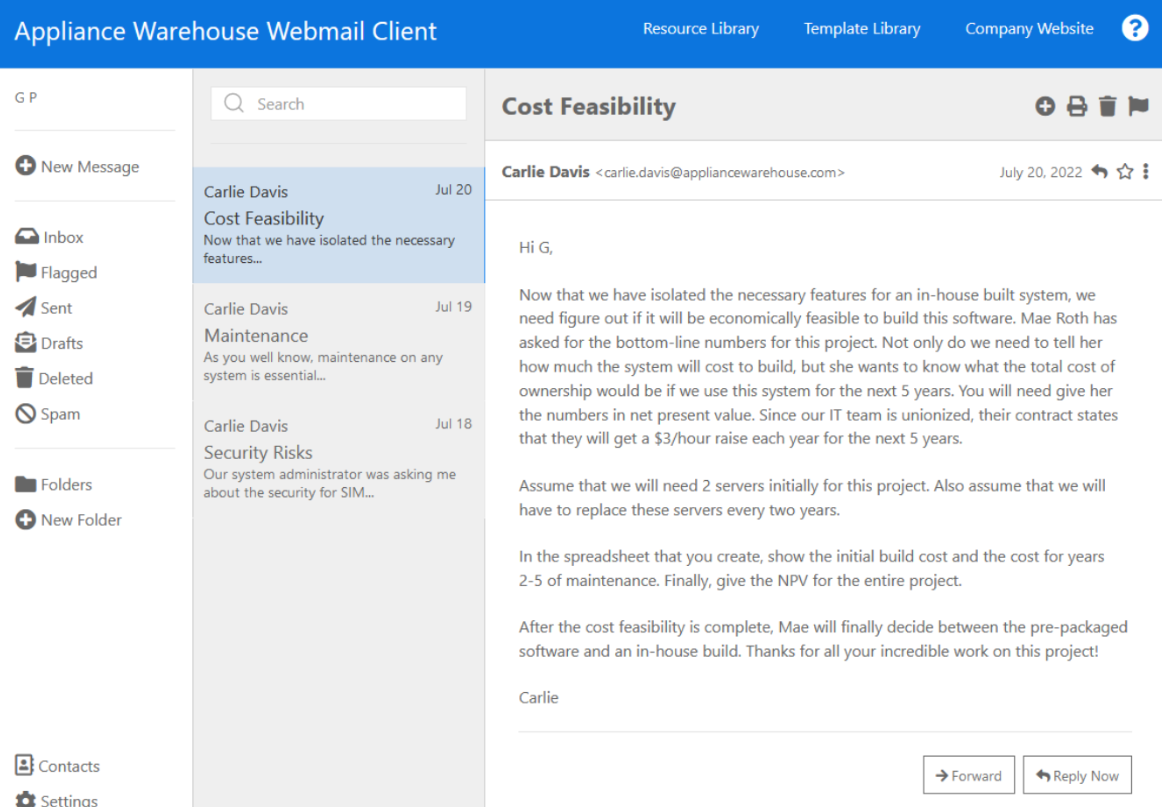
Appliance Warehouse Webmail Client GP + New Message D Inbox Flagged Sent Drafts Deleted Spam Folders + New Folder Contacts Settings Q Search Jul 20 Carlie Davis Cost Feasibility Now that we have isolated the necessary features... Jul 19 Carlie Davis Maintenance As you well know, maintenance on any system is essential... Jul 18 Carlie Davis Security Risks Our system administrator was asking me about the security for SIM... Security Risks Resource Library Hi G, Carlie Davis Template Library Company Website Carlie July 18, 2022: Our system administrator was asking me about the security for SIM. You and I have not discussed this topic in depth. We need to do a risk assessment and look at all types of security issues: physical, network, application, file, user, and procedural. Make a list of the security risks for all six security levels. We need to make sure that we don't leave our new system vulnerable to attacks. Also, what is the backup method to be used for SIM? Please explain why you've chosen this method. Hope you had a great weekend! 2. Forward Reply Now
Step by Step Solution
There are 3 Steps involved in it
Step: 1
Heres how we can address each of the tasks outlined in Carlies emails 1 System Maintenance Plan Reco...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


