Question: Match each digital security threat to its definition. To answer, move each threat from the list on the left to its definition on the right.
Match each digital security threat to its definition. To answer, move each threat from the list on the left to its definition on the right.
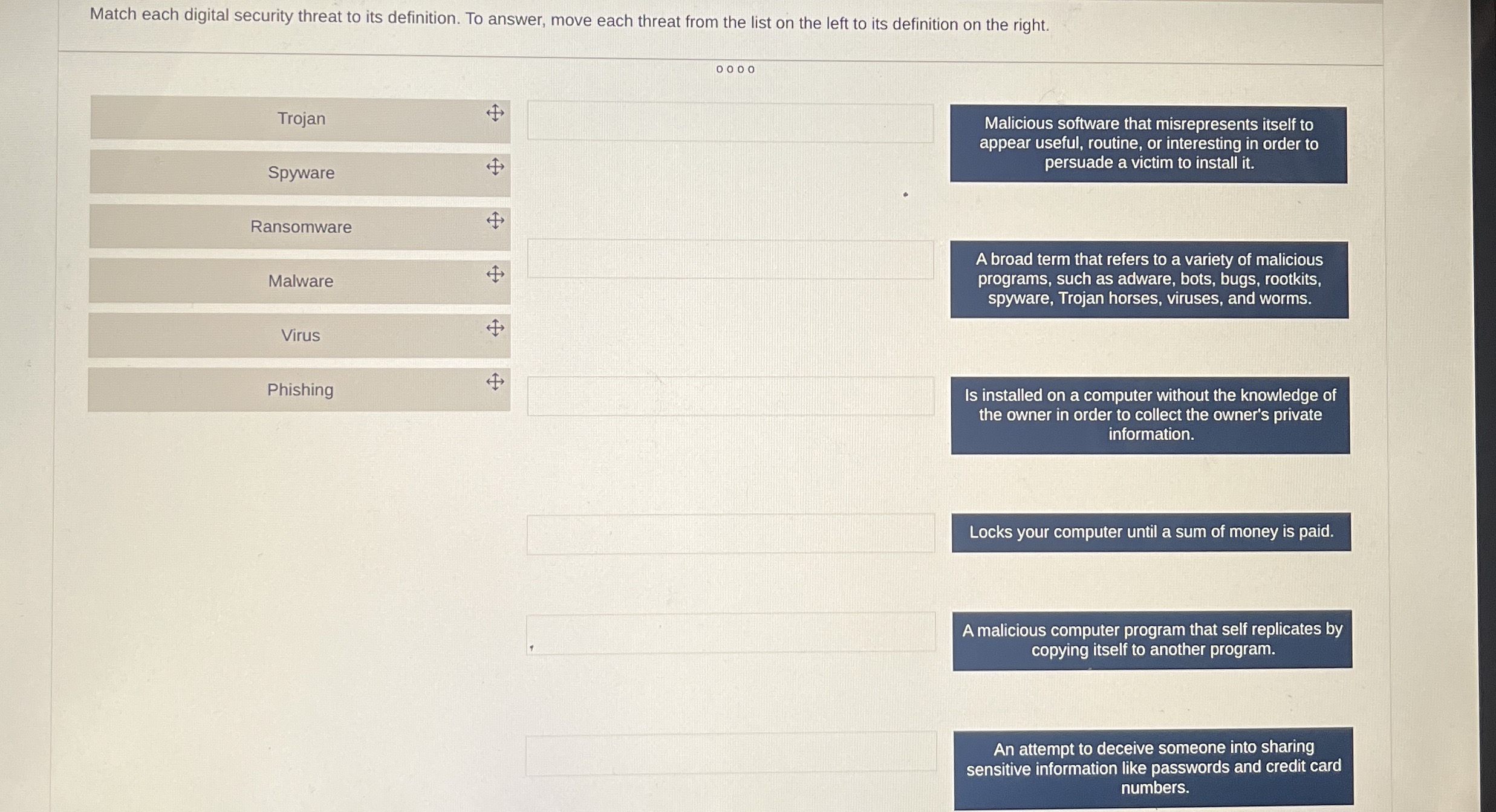
Trojan
Spyware
Ransomware
Malware
Virus
Phishing
Malicious software that misrepresents itself to appear useful, routine, or interesting in order to persuade a victim to install it
A broad term that refers to a variety of malicious programs, such as adware, bots, bugs, rootkits, spyware, Trojan horses, viruses, and worms.
Is installed on a computer without the knowledge of the owner in order to collect the owner's private information.
Locks your computer until a sum of money is paid.
A malicious computer program that self replicates by copying itself to another program.
An attempt to deceive someone into sharing sensitive information like passwords and credit card numbers.
Match each digital security threat to its definition. To answer, move each threat from the list on the left to its definition on the right.
Trojan
Malicious software that misrepresents itself to appear useful, routine, or interesting in order to persuade a victim to install it
Spyware
Ransomware
Malware
Virus
Phishing
Locks your computer until a sum of money is paid.
A malicious computer program that self replicates by copying itself to another program.
An attempt to deceive someone into sharing se
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


