Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Methods (1) - Protected View Saved to this PC erences Mailings Review View Help ntain viruses. Unless you need to edit, it's safer to
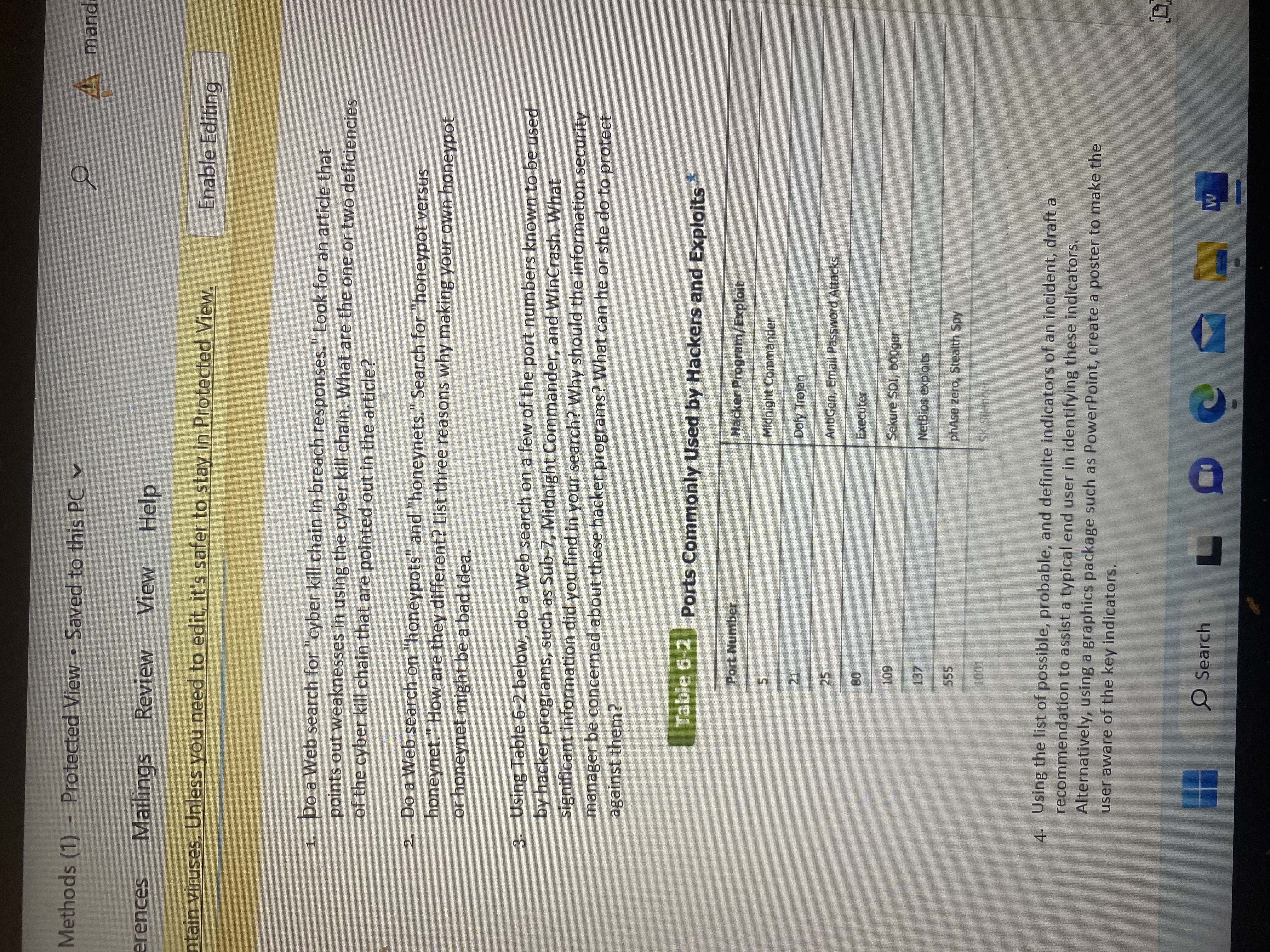
Methods (1) - Protected View Saved to this PC erences Mailings Review View Help ntain viruses. Unless you need to edit, it's safer to stay in Protected View. A mand Enable Editing 1. Do a Web search for "cyber kill chain in breach responses." Look for an article that points out weaknesses in using the cyber kill chain. What are the one or two deficiencies of the cyber kill chain that are pointed out in the article? 2. Do a Web search on "honeypots" and "honeynets." Search for "honeypot versus honeynet." How are they different? List three reasons why making your own honeypot or honeynet might be a bad idea. 3. Using Table 6-2 below, do a Web search on a few of the port numbers known to be used by hacker programs, such as Sub-7, Midnight Commander, and WinCrash. What significant information did you find in your search? Why should the information security manager be concerned about these hacker programs? What can he or she do to protect against them? Table 6-2 Ports Commonly Used by Hackers and Exploits Port Number 5 21 25 80 109 137 555 1001 Hacker Program/Exploit Midnight Commander Doly Trojan AntiGen, Email Password Attacks Executer Sekure SDI, b00ger NetBios exploits phAse zero, Stealth Spy SK Silencer * 4. Using the list of possible, probable, and definite indicators of an incident, draft a recommendation to assist a typical end user in identifying these indicators. Alternatively, using a graphics package such as PowerPoint, create a poster to make the user aware of the key indicators. > Search W D
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


