Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Module 2 . Pipeline Enhancement In this project, you are provided with an architecture presented in a PowerPoint file format ( m 2 _ pipeline.pptx
Module Pipeline Enhancement
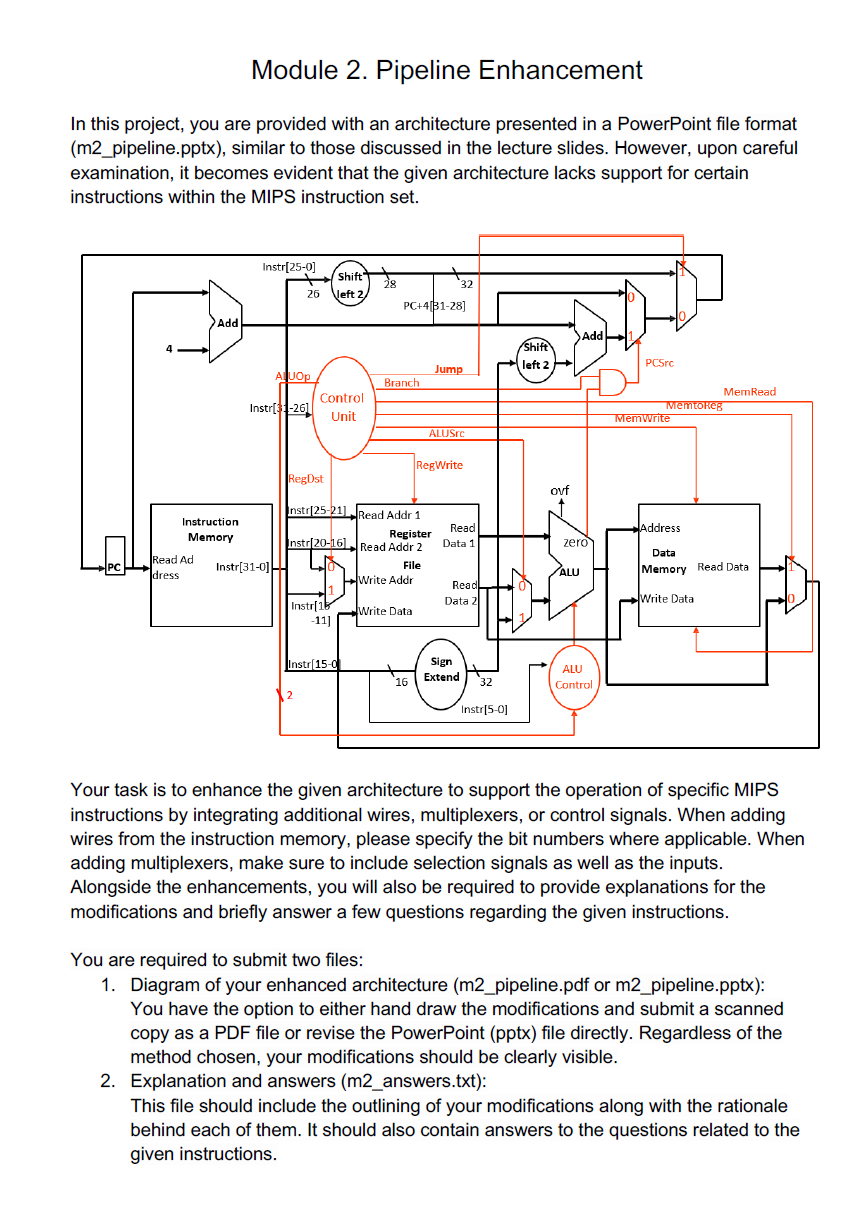
In this project, you are provided with an architecture presented in a PowerPoint file format mpipeline.pptx similar to those discussed in the lecture slides. However, upon careful examination, it becomes evident that the given architecture lacks support for certain instructions within the MIPS instruction set.
Your task is to enhance the given architecture to support the operation of specific MIPS instructions by integrating additional wires, multiplexers, or control signals. When adding wires from the instruction memory, please specify the bit numbers where applicable. When adding multiplexers, make sure to include selection signals as well as the inputs. Alongside the enhancements, you will also be required to provide explanations for the modifications and briefly answer a few questions regarding the given instructions.
You are required to submit two files:
Diagram of your enhanced architecture mpipeline.pdf or mpipeline.pptx: You have the option to either hand draw the modifications and submit a scanned copy as a PDF file or revise the PowerPoint pptx file directly. Regardless of the method chosen, your modifications should be clearly visible.
Explanation and answers manswers.txt:
This file should include the outlining of your modifications along with the rationale behind each of them. It should also contain answers to the questions related to the given instructions. The current architecture is unable to execute the jr instruction. Please make appropriate
modifications to the architecture to enable the operation and answer the following questions.
instruction format: jr RS
sample instruction: jr $
Q Why is the jr instruction not classified as a Jtype instruction?
Q What rationale could explain why the jr instruction is not categorized as an Itype
instruction?
The current architecture is unable to execute the sll Shift Left Logical instruction. Please
make appropriate modifications to the architecture to enable the operation and answer the
following questions. You may assume that the ALU takes two operands, source register and
shift amount, to perform the shift operation.
instruction format: sll RD RT SHAMT
sample instruction: sll $$
Q What factors might explain the choice of $rt over $rs as the source register for the sll
instruction?
Q What could be some reasons why shift operations utilize shamt as the operand
instead of using two source registers? Module Cache Simulation
In this project, you are given a template code of a simple cache simulator in Python file
format msimulatortemplate.py Note that the simulator's overall structure is
implemented, but important portions of code are missing. Also note that the block size,
associativity, and the replacement policy are all configurable at the source level, with non
default values commented out.
You are also provided with a cache access log file as a text file logtxt The log file gives a
decimal integer on each line, which denotes the address accessed by the processor. You
may assume the following:
The addresses references are given as byte addresses no byte offset required
The cache can hold bytes of data and is assumed to have extra space for required
information such as tags.
The log consists only of memory reads no write policies
For ease of implementation, you may disregard the data to be accessed. Only the
address of memory accesses is given, and the cache only stores the tag in order to
determine the hit or miss of accesses.
Your first task is to complete the four missing functions of the simulator.
Deriving the tag, index, and offset of the address: deriveTIO
The function receives the memory address and cache configurations as input. You
must complete the function to return the tag, index, and offset.
Hint: integer division and modulo operations can be helpful
Determining whether the access results in a hit or a miss: cacheaccess
The function receives the current status of the cache along with the tag, index, and
offset of the accessed address as input. You must complete the function to return
True if the access results in a cache hit, and False otherwise.
Implementing the FIFO replacement policy: replFIFO
The function receives a set of blocks as a list along with the memory access
information. You must complete the function to return a new list with the victim
block removed, if any, and with a new block containing the data included.
In the FIFO replacement policy, the oldest block must be removed.
Implementing the LRU replacement policy: replLRU
The function receives a set of blocks as a list along with the memory access
information. You must complete the function to return a new list with the victim
block removed, if any, and with a new block containing the data included.
In the LRU replacement policy, the least recently used block must be removed. After completing the cache simulat
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


