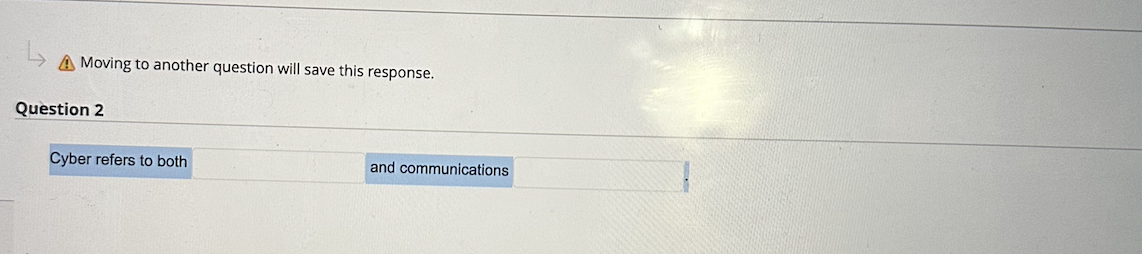
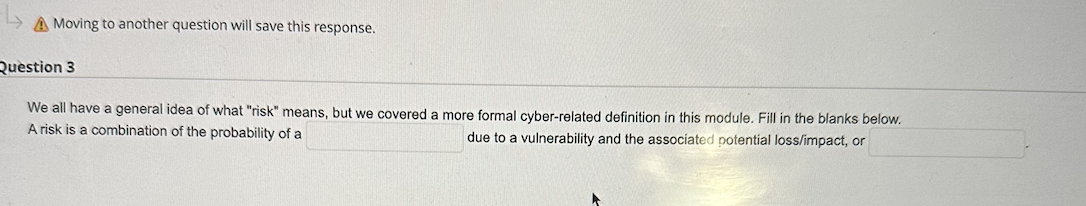

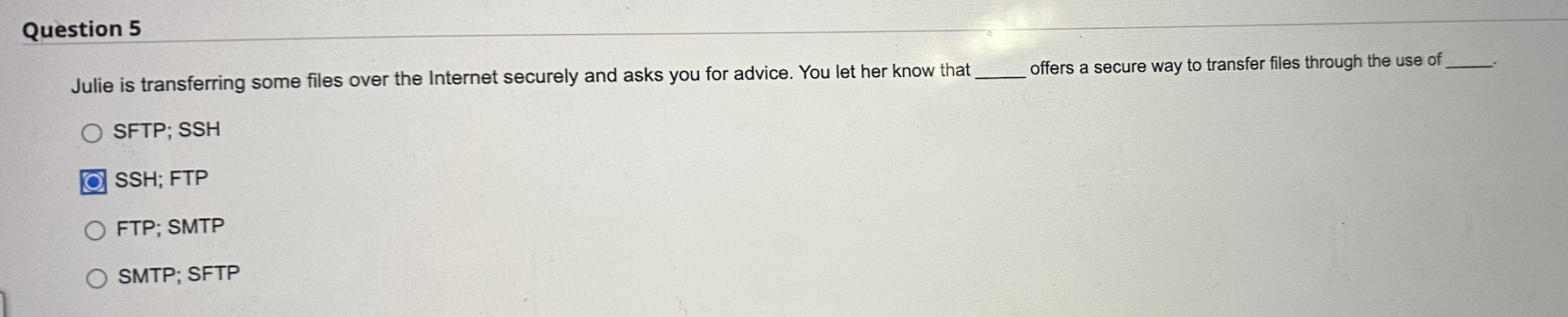

Moving to another question will save this response. A Moving to another question will save this response. uestion 3 We all have a general idea of what "risk" means, but we covered a more formal cyber-related definition in this module. Fill in the blanks below. A risk is a combination of the probability of a due to a vulnerability and the associated potential loss/impact, or Your peer programming buddy emphasizes the importance of a program anticipating problems due to errors such as incorrect, inappropriate or corrupt data and unavailability of needed resources such a connections. Doing so, she explains, reflects its robustness usability portability reliability Julie is transferring some files over the Internet securely and asks you for advice. You let her know that offers a secure way to transfer files through the use of SFTP; SSH SSH; FTP FTP; SMTP SMTP; SFTP Lila and Joseph are debating the elements of "cyberspace". Can you help them out? True or False: Cyberspace includes the interaction of both software and hardware. True False The term "cybersecurity" can mean many things to many people! We're relying the NISTIR definition in this course. Fill in the blanks below. Cybersecurity can be defined as the prevention of damage to, unauthorized use of, of, and-if needed-the of electronic information and communications systems, and the information they contain, in order to strengthen the confidentiality, and availability of these systems. Cyber incidents today are multifaceted and complex. In the broadest sense, the cornerstone of accountability in a cyber attack is in other words, determining who is to blame. Byron is a systems analyst who documents the inputs, processing, and outputs of each program within an application. True or False? Byron work aligns best with the maintenance phase of the Systems Development Life Cycle. True False Trevor is trying to connect his sandbox system to the Internet and knows he needs a "port" but cannot find it. He thinks a port on a device is a physical plugin to the Internet. Is this assumption True or False? True False















