Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Multiple Choice Multiple Choice 57. Which type of organizations should prepare for the unexpected? a. Organizations of every size and purpose should also prepare
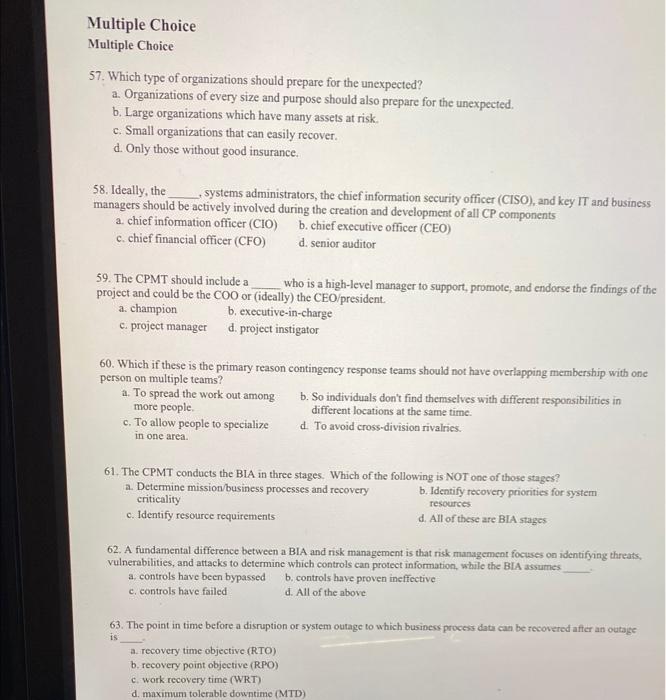
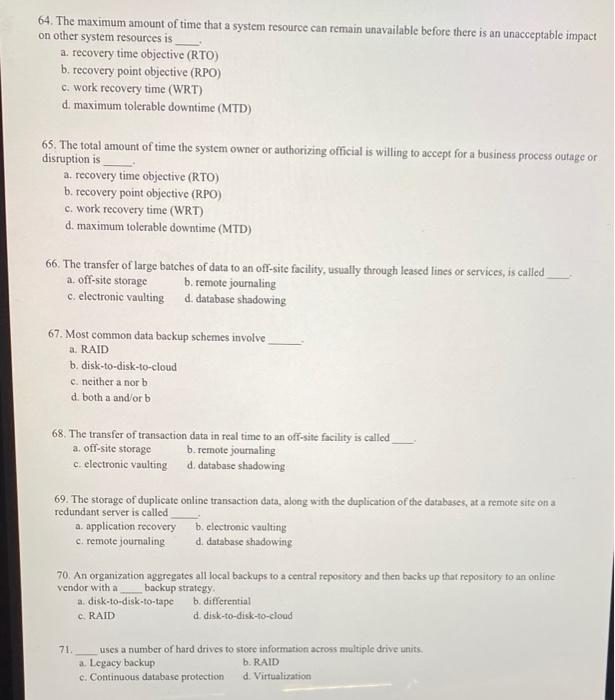
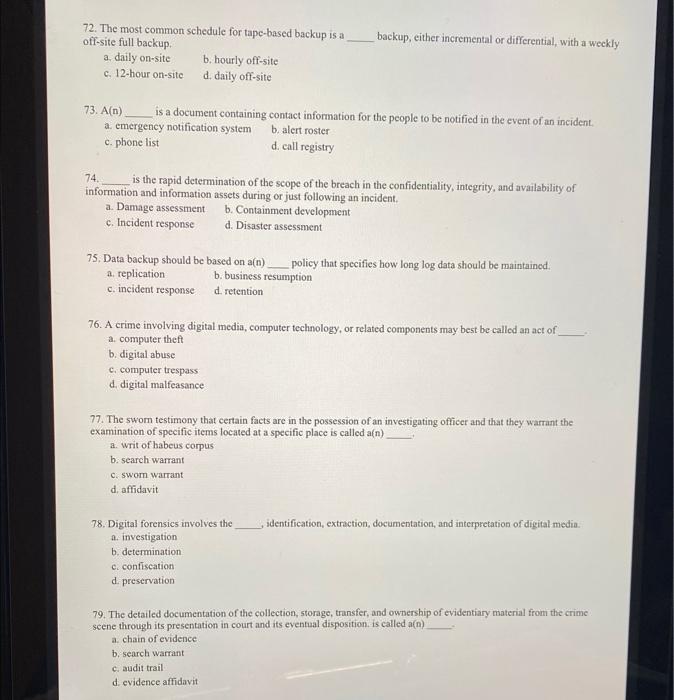

Multiple Choice Multiple Choice 57. Which type of organizations should prepare for the unexpected? a. Organizations of every size and purpose should also prepare for the unexpected. b. Large organizations which have many assets at risk. c. Small organizations that can easily recover. d. Only those without good insurance. 58. Ideally, the systems administrators, the chief information security officer (CISO), and key IT and business managers should be actively involved during the creation and development of all CP components a. chief information officer (CIO) b. chief executive officer (CEO) c. chief financial officer (CFO) 59. The CPMT should include a d. senior auditor who is a high-level manager to support, promote, and endorse the findings of the project and could be the COO or (ideally) the CEO/president. a. champion b. executive-in-charge c. project manager d. project instigator 60. Which if these is the primary reason contingency response teams should not have overlapping membership with one person on multiple teams? a. To spread the work out among more people. c. To allow people to specialize in one area. b. So individuals don't find themselves with different responsibilities in different locations at the same time. d. To avoid cross-division rivalries. 61. The CPMT conducts the BIA in three stages. Which of the following is NOT one of those stages? a. Determine mission/business processes and recovery criticality c. Identify resource requirements b. Identify recovery priorities for system resources d. All of these are BIA stages 62. A fundamental difference between a BIA and risk management is that risk management focuses on identifying threats, vulnerabilities, and attacks to determine which controls can protect information, while the BIA assumes a. controls have been bypassed c. controls have failed b. controls have proven ineffective d. All of the above 63. The point in time before a disruption or system outage to which business process data can be recovered after an outage is a. recovery time objective (RTO) b. recovery point objective (RPO) c. work recovery time (WRT) d. maximum tolerable downtime (MTD)
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


