Question: NACLS Submit Configure NACLs to control the access to the VMs according to the following: Allow the administrator to access all the VMs via

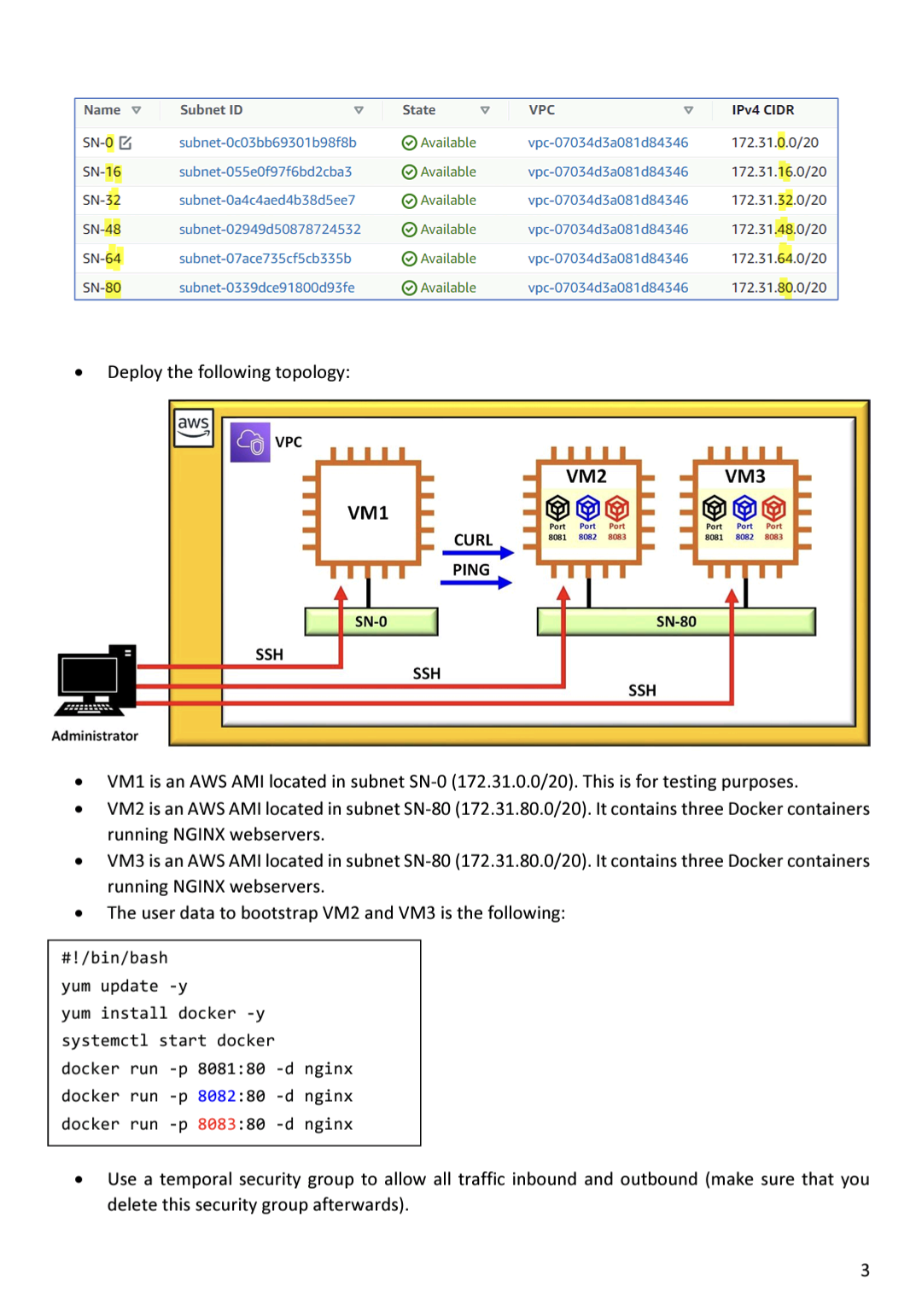
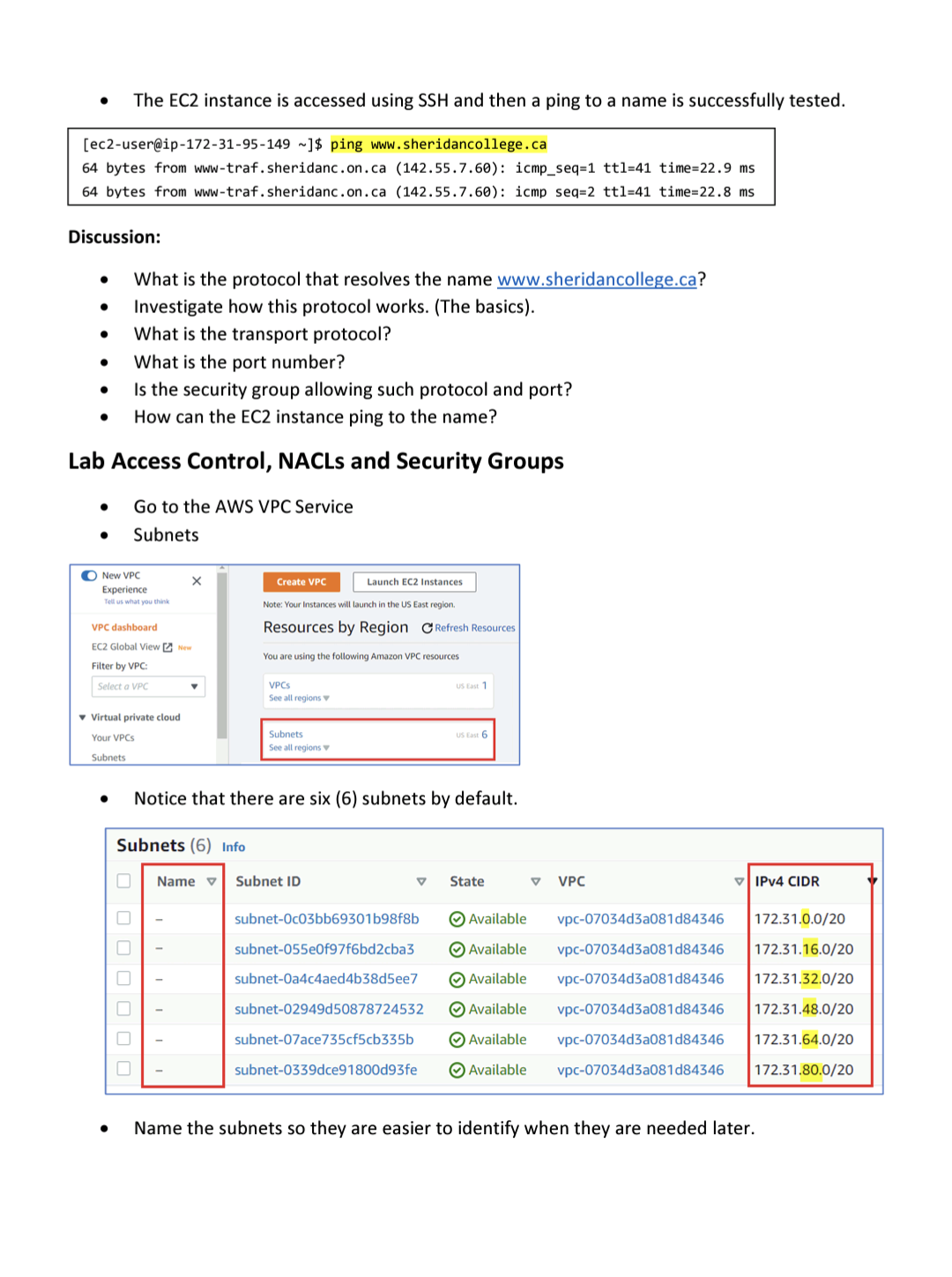
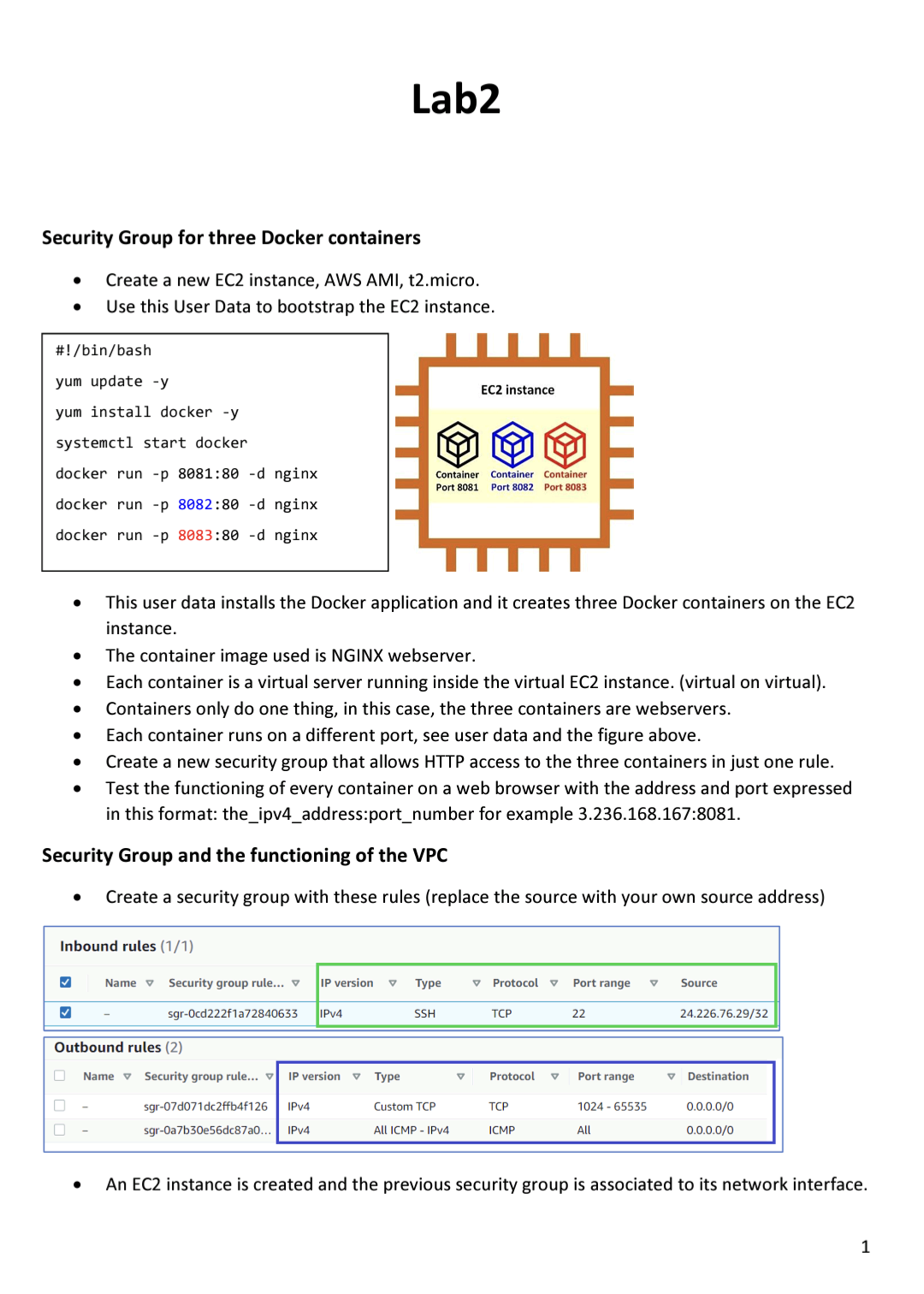
NACLS Submit Configure NACLs to control the access to the VMs according to the following: Allow the administrator to access all the VMs via SSH. Submit Allow pinging from VM1 only to either VM2 or VM3. Allow VM1 to curl the webservers in the containers. Security Groups The command curl is a tool to test the functioning of webservers since the VM do not have a graphic web browser interface. The answer to a curl is the website landing page in text. Submit clear snippets of all the NACLS and a brief explanation of their functioning. Submit the proofs of the successful ping to VM2 and VM3 from VM1. Submit the proofs of the successful curl to VM2 and VM3 from VM1. Remove the association of the previous NACLs to avoid interference. Associate the subnets back to the default NACL. Remove the temporal security group from the previous step to avoid interference. Configure Security Groups to control the access to the VMs according to the following: Allow the administrator to access all the VMs via SSH. Allow pinging from VM1 only to either VM2 or VM3. Allow VM1 to curl the webservers in the containers. The command curl is a tool to test the functioning of webservers since the VM do not have a graphic web browser interface. The answer to a curl is the website landing page in text. Submit clear snippets of all the Security Groups and a brief explanation of their functioning. Submit the proof of successfully pinging VM2 and VM3 from VM1. Submit the proofs of the successful curl to VM2 and VM3 from VM1. Name v SN-0 SN-16 SN-32 SN-48 SN-64 SN-80 Administrator Deploy the following topology: Subnet ID subnet-Oc03bb69301b98f8b subnet-055e0f97f6bd2cba3 subnet-0a4c4aed4b38d5ee7 subnet-02949d50878724532 subnet-07ace735cf5cb335b subnet-0339dce91800d93fe aws VPC SSH VM1 SN-0 #!/bin/bash yum update -y yum install docker -y systemctl start docker docker run -p 8081:80 -d nginx docker run-p 8082:80 -d nginx docker run -p 8083:80 -d nginx State Available Available Available Available Available Available SSH V CURL PING VPC vpc-07034d3a081d84346 vpc-07034d3a081d84346 vpc-07034d3a081d84346 vpc-07034d3a081d84346 vpc-07034d3a081d84346 vpc-07034d3a081d84346 VM2 1998 Port Port Port 8081 8082 8083 V SSH SN-80 IPv4 CIDR 172.31.0.0/20 172.31.16.0/20 172.31.32.0/20 172.31.48.0/20 172.31.64.0/20 172.31.80.0/20 VM3 Port Port Port 8081 8082 8083 VM1 is an AWS AMI located in subnet SN-0 (172.31.0.0/20). This is for testing purposes. VM2 is an AWS AMI located in subnet SN-80 (172.31.80.0/20). It contains three Docker containers running NGINX webservers. VM3 is an AWS AMI located in subnet SN-80 (172.31.80.0/20). It contains three Docker containers running NGINX webservers. The user data to bootstrap VM2 and VM3 is the following: Use a temporal security group to allow all traffic inbound and outbound (make sure that you delete this security group afterwards). 3 The EC2 instance is accessed using SSH and then a ping to a name is successfully tested. [ec2-user@ip-172-31-95-149 ~]$ ping www.sheridancollege.ca 64 bytes from www-traf.sheridanc.on.ca (142.55.7.60): icmp_seq=1 ttl-41 time=22.9 ms 64 bytes from www-traf.sheridanc.on.ca (142.55.7.60): icmp seq=2 ttl=41 time=22.8 ms Discussion: What is the protocol that resolves the name www.sheridancollege.ca? Investigate how this protocol works. (The basics). What is the transport protocol? What is the port number? Is the security group allowing such protocol and port? How can the EC2 instance ping to the name? Lab Access Control, NACLs and Security Groups Go to the AWS VPC Service Subnets New VPC Experience Tell us what you think VPC dashboard EC2 Global ViewNew Filter by VPC: Select a VPC Virtual private cloud Your VPCS Subnets X 0000000 Create VPC Launch EC2 Instances. Note: Your Instances will launch in the US East region. Resources by Region Refresh Resources You are using the following Amazon VPC resources Name VPCs See all regions Subnets See all regions Notice that there are six (6) subnets by default. Subnets (6) Info Subnet ID US East 1 US East 6 subnet-Oc03bb69301b98f8b subnet-055e0f97f6bd2cba3 subnet-0a4c4aed4b38d5ee7 subnet-02949d50878724532 subnet-07ace735cf5cb335b subnet-0339dce91800d93fe V State V VPC IPv4 CIDR Available vpc-07034d3a081d84346 172.31.0.0/20 Available vpc-07034d3a081d84346 172.31.16.0/20 Available vpc-07034d3a081d84346 172.31.32.0/20 Available vpc-07034d3a081d84346 172.31.48.0/20 Available vpc-07034d3a081d84346 172.31.64.0/20 Available vpc-07034d3a081d84346 172.31.80.0/20 Name the subnets so they are easier to identify when they are needed later. Security Group for three Docker containers #!/bin/bash yum update -y yum install docker -y systemctl start docker docker run -p 8081:80 -d nginx docker run -p 8082:80 -d nginx docker run -p 8083:80 -d nginx 0 Create a new EC2 instance, AWS AMI, t2.micro. Use this User Data to bootstrap the EC2 instance. Inbound rules (1/1) Lab2 Create a new security group that allows HTTP access to the three containers in just one rule. Test the functioning of every container on a web browser with the address and port expressed in this format: the_ipv4_address:port_number for example 3.236.168.167:8081. Security Group and the functioning of the VPC Create a security group with these rules (replace the source with your own source address) This user data installs the Docker application and it creates three Docker containers on the EC2 instance. Outbound rules (2) Name The container image used is NGINX webserver. Each container is a virtual server running inside the virtual EC2 instance. (virtual on virtual). Containers only do one thing, in this case, the three containers are webservers. Each container runs on a different port, see user data and the figure above. Container Container Container Port 8081 Port 8082 Port 8083 Security group rule... V IP version V Type sgr-07d071dc2ffb4f126 IPv4 sgr-0a7b30e56dc87a0... IPv4 EC2 instance Name v Security group rule... v IP version V Type V Protocol sgr-Ocd222f1a72840633 IPv4 SSH Custom TCP All ICMP IPv4 V TCP Protocol TCP ICMP V Port range 22 Port range 1024-65535 All V Source 24.226.76.29/32 V Destination 0.0.0.0/0 0.0.0.0/0 An EC2 instance is created and the previous security group is associated to its network interface. 1
Step by Step Solution
3.37 Rating (150 Votes )
There are 3 Steps involved in it
Setup Subnets and Temporary Security Group Rename subnets as per the given pattern Create a temporary security group allowing all traffic This step is about organizing the network environment Renaming ... View full answer

Get step-by-step solutions from verified subject matter experts


